Over the past few months, several new ransomware actors have been observed targeting businesses of all sizes in various countries around the world. These include groups like Hunters International, Meow, DragonForce, Werewolves, Malekteam, etc. All of these actors are being tracked by Symantec, whether they engage in single extortion through exfiltration or encryption, or use double-extortion involving both exfiltration and encryption.
在过去的几个月里,已经观察到几个新的勒索软件行为者针对世界各国各种规模的企业。其中包括 Hunters International、Meow、DragonForce、Werewolves、Malekteam 等团体。所有这些行为者都受到赛门铁克的跟踪,无论他们是通过外泄或加密进行单次勒索,还是使用涉及外泄和加密的双重勒索。
In this protection highlight, we will cover Hunters International, which made the news in late 2023 after claiming multiple victims, and moving into 2024 has claimed even more. This actor is using a ransomware that appears to be closely based on the infamous Hive ransomware code, of which the original group was disrupted by law enforcement in early 2023.
在这个保护亮点中,我们将介绍 Hunters International,它在 2023 年底声称多名受害者后成为新闻,而进入 2024 年则声称更多。该行为者正在使用一种勒索软件,该勒索软件似乎与臭名昭著的 Hive 勒索软件代码密切相关,该代码的原始组织于 2023 年初被执法部门破坏。
As of today, the Hunters International group’s full tactics, techniques, and procedures remain incomplete analysis-wise. However, they are known to move laterally within the victim’s infrastructure and upon finding what they consider to be worthy targets, they exfiltrate sensitive data and encrypt files – a classic modus operandi of most double-extortion ransomware actors.
截至今天,Hunters International 集团的完整战术、技术和程序在分析方面仍不完整。然而,众所周知,他们会在受害者的基础设施内横向移动,并在找到他们认为有价值的目标后,他们会泄露敏感数据并加密文件——这是大多数双重勒索勒索软件参与者的经典作案手法。
If the ransomware binary (collected in January) is successfully triggered on compromised machines, similar to previous samples, it will attempt to kill processes and services. Next, it executes commands to delete backups and disable recovery mechanisms. Then, it iterates through local and mapped drives, as well as shared drives found on the local network through the NetServerEnum and NetShareEnum APIs, encrypting files that are discovered. It adds the extension .lock to each encrypted file and drops a ransom message named “Contact Us.txt” in the same directory. Although the goal is to encrypt files, it will skip the following:
如果勒索软件二进制文件(1 月份收集)在受感染的计算机上成功触发(与之前的示例类似),它将尝试终止进程和服务。接下来,它执行命令以删除备份并禁用恢复机制。然后,它通过 NetServerEnum 和 NetShareEnum API 循环访问本地和映射的驱动器,以及在本地网络上找到的共享驱动器,对发现的文件进行加密。它将扩展名 .lock 添加到每个加密文件中,并在同一目录中放置名为“联系我们 .txt”的勒索消息。尽管目标是加密文件,但它将跳过以下内容:
- Files in folders with these substrings in their names: $Recycle bin, $windows.~bt, $windows.~ws, all users, appdata, boot, config.msi, default, google, intel, mozilla, msocache, perflogs, system volume information, tor browser, internet explorer, windows, windows.old, windows nt
名称中包含以下子字符串的文件夹中的文件:$Recycle bin、$windows.~bt、$windows.~ws、所有用户、appdata、boot、config.msi、default、google、intel、mozilla、msocache、perflogs、系统卷信息、tor 浏览器、internet explorer、windows、windows.old、Windows NT - Files named: autorun.inf, bootfont.bin, boot.ini, bootsect.bak, desktop.ini, iconcache.db, ntldr, ntuser.dat, ntuser.dat.log, ntuser.ini.log, thumbs.db
名为:autorun.inf、bootfont.bin、boot.ini、bootsect.bak、desktop.ini、iconcache.db、ntldr、ntuser.dat、ntuser.dat.log、ntuser.ini.log、thumbs.db - Files with the following extensions: 386, adv, ani, bat, bin, cab, cmd, com, cpl, cur, deskthemepack, diagcab, diagcfg, diagpkg, dll, drv, exe, hlp, hta, icl, icns, ico, ics, idx, key, ldf, lnk, lock, mod, mpa, msc, msi, msp, msstyles, msu, nls, nomedia, ocx, pdb, prf, ps1, rom, rtp, scr, shs, spl, sys, theme, themepack, wpx
具有以下扩展名的文件:386、adv、ani、bat、bin、cab、cmd、com、cpl、cur、deskthemepack、diagcab、diagcfg、diagpkg、dll、drv、exe、hlp、hta、icl、icns、ico、ics、idx、key、ldf、lnk、lock、mod、mpa、msc、msi、msp、msstyles、msu、nls、nomedia、ocx、pdb、prf、ps1、rom、rtp、scr、shs、spl、sys、theme、themepack、wpx
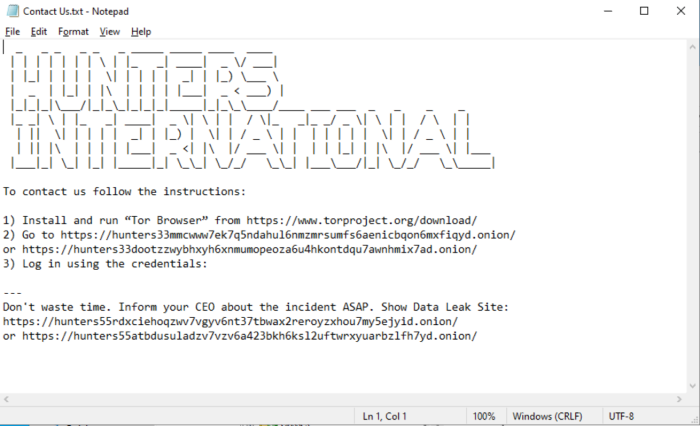
A screenshot of the ransom note left on the victim’s machine.
受害者机器上留下的赎金票据的屏幕截图。
As mentioned above, Symantec constantly tracks new ransomware actors by monitoring new ransom/leak websites and other data from both external and internal sources. While the malware and tools used are not always readily available or easily found, we continue to actively seek samples and identify all TTPs. It’s a constant cat-and-mouse game where staying informed and obtaining indicators of compromise (IOCs) are critical components of effective threat detection and mitigation.
如上所述,赛门铁克通过监控来自外部和内部来源的新勒索/泄密网站和其他数据,不断跟踪新的勒索软件行为者。虽然所使用的恶意软件和工具并不总是容易获得或容易找到,但我们将继续积极寻找样本并识别所有 TTP。这是一场持续的猫捉老鼠游戏,随时了解情况并获得入侵指标 (IOC) 是有效检测和缓解威胁的关键组成部分。
Symantec protects you from this threat, identified by the following:
赛门铁克可保护您免受此威胁的侵害,具体表现如下:
File-based 基于文件
- Ransom.Hunters!g1 赎金猎人!g1
- Trojan.Gen.MBT 特洛伊木马.Gen.MBT
- Trojan Horse 特洛伊木马
Behavior-based 基于行为
- SONAR.SuspLaunch!gen4 声纳。SuspLaunch!gen4
- SONAR.SuspLaunch!g18 声纳。SuspLaunch!g18
- SONAR.SuspLaunch!g195 声纳。暂停发射!g195
- SONAR.SuspLaunch!g253 声纳。SuspLaunch!g253
- SONAR.RansomPlay!gen1 声纳。赎金Play!gen1
- SONAR.RansomGen!gen3 声纳。赎金Gen!gen3
- SONAR.SuspLaunch!g193 声纳。SuspLaunch!g193
Machine Learning-based 基于机器学习
- Heur.AdvML.B!100 Heur.AdvML.B!100
Policy-based 基于策略
- Symantec DCS Hardening policy for Windows provides 0-day protection against Hunter’s Hive ransomware. The default sandboxing controls prevent webshells and malware tools from getting installed and prevent arbitrary system command execution from privileged applications.
适用于 Windows 的 Symantec DCS 强化策略提供针对 Hunter’s Hive 勒索软件的 0 天保护。默认沙盒控件可防止安装 Webshell 和恶意软件工具,并防止特权应用程序执行任意系统命令。
EDR-based 基于 EDR
- Symantec EDR is capable of monitoring and flagging this threat actor’s tactics, techniques and procedures.
Symantec EDR 能够监控和标记此威胁参与者的策略、技术和程序。 - Symantec added malware-specific threat hunting queries which can be fired on the customer iCDM console. For more information, refer to this link: https://github.com/Symantec/threathunters/tree/main/Ransomwares/HunterInternational/
赛门铁克添加了特定于恶意软件的威胁搜寻查询,这些查询可以在客户 iCDM 控制台上触发。有关更多信息,请参阅此链接:https://github.com/Symantec/threathunters/tree/main/Ransomwares/HunterInternational/
Click here to learn more about Symantec’s Endpoint Security Service.
单击此处了解有关赛门铁克端点安全服务的更多信息。
Click here to learn how Symantec behavioral security technologies provide protection against zero-day attacks.
单击此处,了解赛门铁克行为安全技术如何提供针对零日攻击的防护。
Click here to learn more about how Symantec Endpoint Protection uses advanced machine learning.
单击此处,详细了解 Symantec Endpoint Protection 如何使用高级机器学习。
Click here to learn more about Symantec’s Data Center Security.
单击此处了解有关赛门铁克数据中心安全的更多信息。
Click here to learn about Symantec Endpoint Detection & Response.
单击此处了解 Symantec Endpoint Detection & Response。
** Symantec Endpoint Detection and Response (EDR) uses machine learning and behavioral analytics to detect and expose suspicious network activities. EDR alerts about potentially harmful activity, prioritizes incidents for quick triage, and allows incident responders to navigate device activity records for purposes of forensic analysis of potential attacks.
** Symantec Endpoint Detection and Response (EDR) 使用机器学习和行为分析来检测和揭露可疑网络活动。EDR 会针对潜在有害活动发出警报,确定事件的优先级以便快速分类,并允许事件响应者浏览设备活动记录,以便对潜在攻击进行取证分析。
原文始发于BROADCOM:Protection Highlight: Hunters International Ransomware
转载请注明:Protection Highlight: Hunters International Ransomware | CTF导航