
Researchers at Eurecom have developed six new attacks collectively named ‘BLUFFS’ that can break the secrecy of Bluetooth sessions, allowing for device impersonation and man-in-the-middle (MitM) attacks.
Eurecom的研究人员开发了六种新的攻击,统称为“BLUFFS”,可以破坏蓝牙会话的保密性,允许设备冒充和中间人(MitM)攻击。
Daniele Antonioli, who discovered the attacks, explains that BLUFFS exploits two previously unknown flaws in the Bluetooth standard related to how session keys are derived to decrypt data in exchange.
发现这些攻击的丹尼尔·安东尼奥利(Daniele Antonioli)解释说,BLUFFS利用了蓝牙标准中两个以前未知的缺陷,这些缺陷与会话密钥的派生方式有关,以解密交换中的数据。
These flaws are not specific to hardware or software configurations but are architectural instead, meaning they affect Bluetooth at a fundamental level.
这些缺陷并非特定于硬件或软件配置,而是架构上的缺陷,这意味着它们在基本层面上影响蓝牙。
 Top Stories 头条新闻
Top Stories 头条新闻 READ MORE
READ MORE



 Linux version of Qilin ransomware focuses onVMware ESXi
Linux version of Qilin ransomware focuses onVMware ESXi
The issues are tracked under the identifier CVE-2023-24023 and impact Bluetooth Core Specification 4.2 through 5.4.
这些问题在标识符 CVE-2023-24023 下进行跟踪,并影响蓝牙核心规范 4.2 到 5.4。
Considering the widespread use of the well-established wireless communication standard and the versions impacted by the exploits, BLUFFS could work against billions of devices, including laptops, smartphones, and other mobile devices.
考虑到公认的无线通信标准的广泛使用以及受漏洞影响的版本,BLUFFS 可以针对数十亿台设备,包括笔记本电脑、智能手机和其他移动设备。
How BLUFFS works BLUFFS如何运作
BLUFFS is a series of exploits targeting Bluetooth, aiming to break Bluetooth sessions’ forward and future secrecy, compromising the confidentiality of past and future communications between devices.
BLUFFS 是一系列针对蓝牙的漏洞利用,旨在破坏蓝牙会话的前向和未来保密性,损害设备之间过去和未来通信的机密性。
This is achieved by exploiting four flaws in the session key derivation process, two of which are new, to force the derivation of a short, thus weak and predictable session key (SKC).
这是通过利用会话密钥派生过程中的四个缺陷(其中两个是新的)来强制派生一个短的、因此弱且可预测的会话密钥 (SKC) 来实现的。
Next, the attacker brute-forces the key, enabling them to decrypt past communication and decrypt or manipulate future communications.
接下来,攻击者暴力破解密钥,使他们能够解密过去的通信并解密或操纵未来的通信。
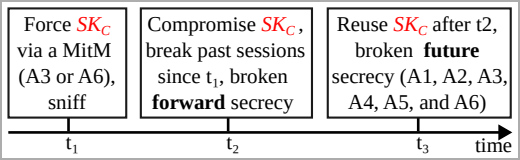
攻击步骤 (dl.acm.org)
Executing the attack presupposes that the attacker is within Bluetooth range of the two targets that exchange data and impersonates one to negotiate for a weak session key with the other, proposing the lowest possible key entropy value and using a constant session key diversifier.
执行攻击的前提是攻击者在交换数据的两个目标的蓝牙范围内,并冒充其中一个目标与另一个目标协商弱会话密钥,提出尽可能低的密钥熵值,并使用常量会话密钥多样化器。
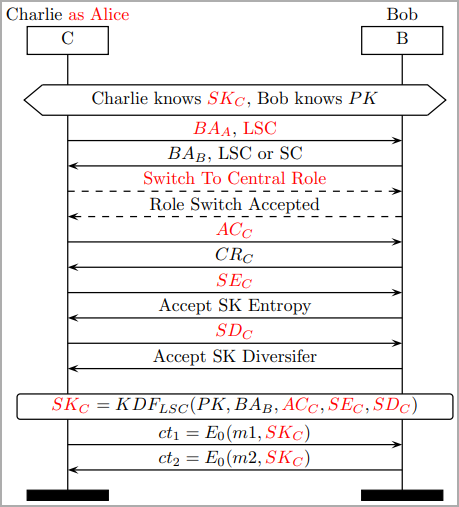
协商会话密钥,同时欺骗合法方
(dl.acm.org) (dl.acm.org)
The published paper presents six types of BLUFFS attacks, covering various combinations of impersonating and MitM attacks, which work regardless of whether the victims support Secure Connections (SC) or Legacy Secure Connections (LSC).
发表的论文介绍了六种类型的虚张声势攻击,涵盖了冒充和 MitM 攻击的各种组合,无论受害者是否支持安全连接 (SC) 或传统安全连接 (LSC),这些攻击都有效。
The researchers developed and shared a toolkit on GitHub that demonstrates the effectiveness of BLUFFS. It includes a Python script to test the attacks, the ARM patches, the parser, and the PCAP samples captured during their tests.
研究人员在GitHub上开发并分享了一个工具包,展示了BLUFFS的有效性。它包括一个用于测试攻击的 Python 脚本、ARM 补丁、解析器和测试期间捕获的 PCAP 示例。
Impact and remediation 影响和补救措施
BLUFFS impacts Bluetooth 4.2, released in December 2014, and all versions up to the latest, Bluetooth 5.4, released in February 2023.
BLUFFS 影响 2014 年 12 月发布的蓝牙 4.2 以及 2023 年 2 月发布的最新版本蓝牙 5.4 之前的所有版本。
The Eurecom paper presents test results for BLUFFS against various devices, including smartphones, earphones, and laptops, running Bluetooth versions 4.1 through 5.2. All of them were confirmed to be susceptible to at least three out of six BLUFFS attacks.
Eurecom 论文介绍了 Bluffs 在运行蓝牙版本 4.1 至 5.2 的各种设备(包括智能手机、耳机和笔记本电脑)上的测试结果。他们都被证实容易受到六次虚张声势攻击中的至少三次。
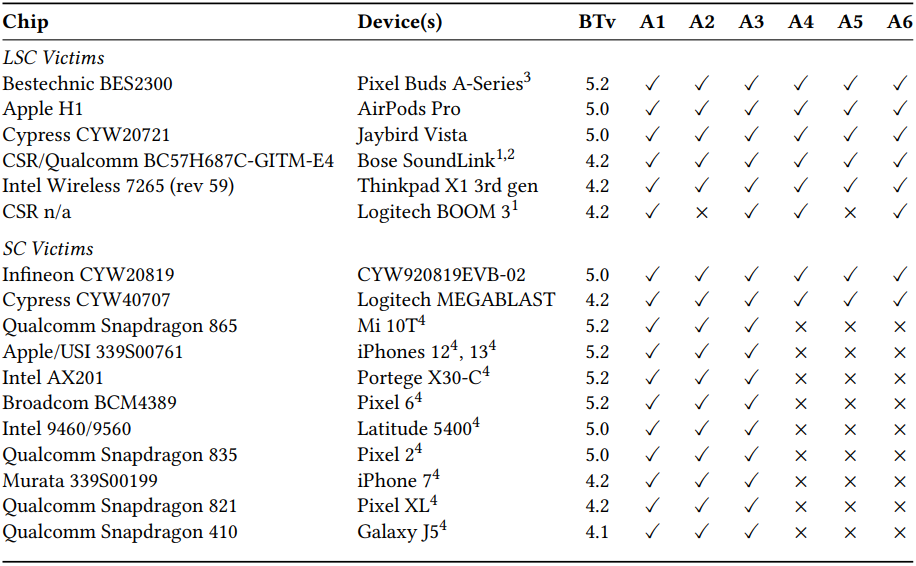
针对各种设备进行虚张声势测试 (dl.acm.org)
The paper also proposes the following backward-compatible modifications that would enhance session key derivation and mitigate BLUFFS and similar threats:
本文还提出了以下向后兼容的修改,这些修改将增强会话密钥派生并减轻虚张声势和类似威胁:
- Introduce a new “Key Derivation Function” (KDF) for Legacy Secure Connections (LSC) that involves mutual nonce exchange and verification, adding minimal overhead.
为传统安全连接 (LSC) 引入新的“密钥派生函数”(KDF),该函数涉及相互随机数交换和验证,从而将开销降至最低。 - Devices should use a shared pairing key for the mutual authentication of key diversifiers, ensuring the legitimacy of session participants.
设备应使用共享配对密钥进行密钥多样化器的相互身份验证,以确保会话参与者的合法性。 - Enforce Secure Connections (SC) mode where possible.
尽可能强制实施安全连接 (SC) 模式。 - Maintain a cache of session key diversifiers to prevent reuse.
维护会话密钥多样化器的缓存,以防止重复使用。
Bluetooth SIG (Special Interest Group), the non-profit organization that oversees the development of the Bluetooth standard and is responsible for licensing the technology, has received Eurecom’s report and published a statement on its site.
Bluetooth SIG(Special Interest Group)是负责监督蓝牙标准开发并负责该技术许可的非营利组织,已收到Eurecom的报告,并在其网站上发表了一份声明。
The organization suggests that implementations reject connections with low key strengths below seven octets, use ‘Security Mode 4 Level 4’, which ensures a higher encryption strength level, and operate in ‘Secure Connections Only’ mode when pairing.
该组织建议,实现拒绝低于七个八位字节的低密钥强度的连接,使用“安全模式 4 级别 4”,以确保更高的加密强度级别,并在配对时以“仅安全连接”模式运行。
原文始发于Bill Toulas:New BLUFFS attack lets attackers hijack Bluetooth connections
转载请注明:New BLUFFS attack lets attackers hijack Bluetooth connections | CTF导航