
Microsoft addressed our LocalPotato vulnerability in the SMB scenario with CVE-2023-21746 during the January 2023 Patch Tuesday. However, the HTTP scenario remains unpatched, as per Microsoft’s decision, and it is still effective on updated systems.
Microsoft 在 2023 年 1 月的星期二补丁期间通过 CVE-2023-21746 解决了 SMB 场景中的 LocalPotato 漏洞。但是,根据 Microsoft 的决定,HTTP 方案仍未修补,并且在更新的系统上仍然有效。
This is clearly an edge case, but it is important to be aware of it and avoid situations that could leave you vulnerable.
这显然是一个边缘情况,但重要的是要意识到这一点并避免可能使您容易受到攻击的情况。
In this brief post, we will explain a possible method of performing an arbitrary file write with SYSTEM privileges starting from a standard user by leveraging the context swap in HTTP NTLM local authentication using the WEBDAV protocol.
在这篇简短的文章中,我们将解释一种可能的方法,通过使用 WEBDAV 协议利用 HTTP NTLM 本地身份验证中的上下文交换,从标准用户开始,以 SYSTEM 权限执行任意文件写入。
For all the details about the NTLM Context swapping refer to our previous post.
有关 NTLM 上下文交换的所有详细信息,请参阅我们之前的文章。
LAB SETUP 实验室设置
First of all, we need to install IIS on our Windows machine and enable Webbav, The following screenshot is taken from Windows 11, but is quite similar on Windows servers as well.
首先,我们需要在 Windows 机器上安装 IIS 并启用 Webbav,以下屏幕截图取自 Windows 11,但在 Windows 服务器上也非常相似。
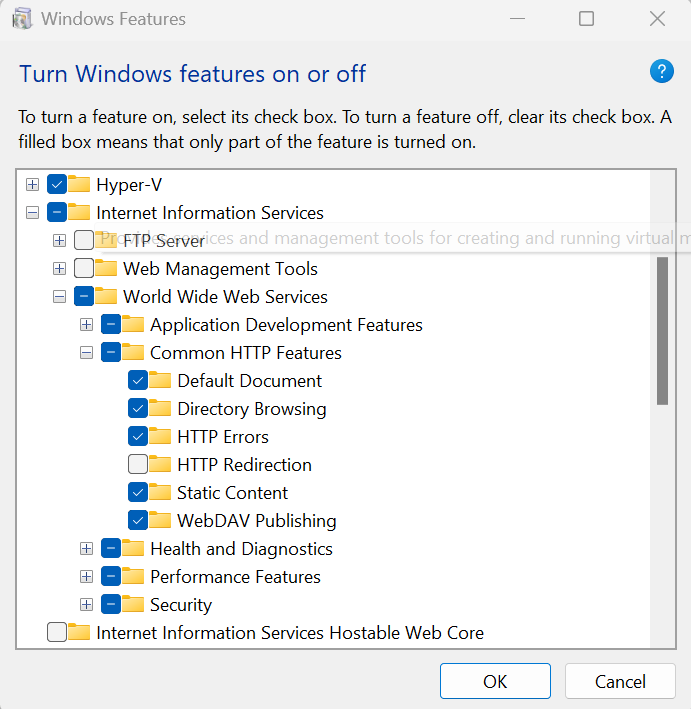
Upon enabling WEBDAV, the next step is to create a virtual directory under our root website. In this instance, we’ll name it webdavshare and mount it, for the sake of simplicity, on the C:\Windows directory.
启用 WEBDAV 后,下一步是在我们的根网站下创建一个虚拟目录。在本例中,为了简单起见,我们将它命名为 webdavshare,并将其挂载到 C:\Windows 目录下。

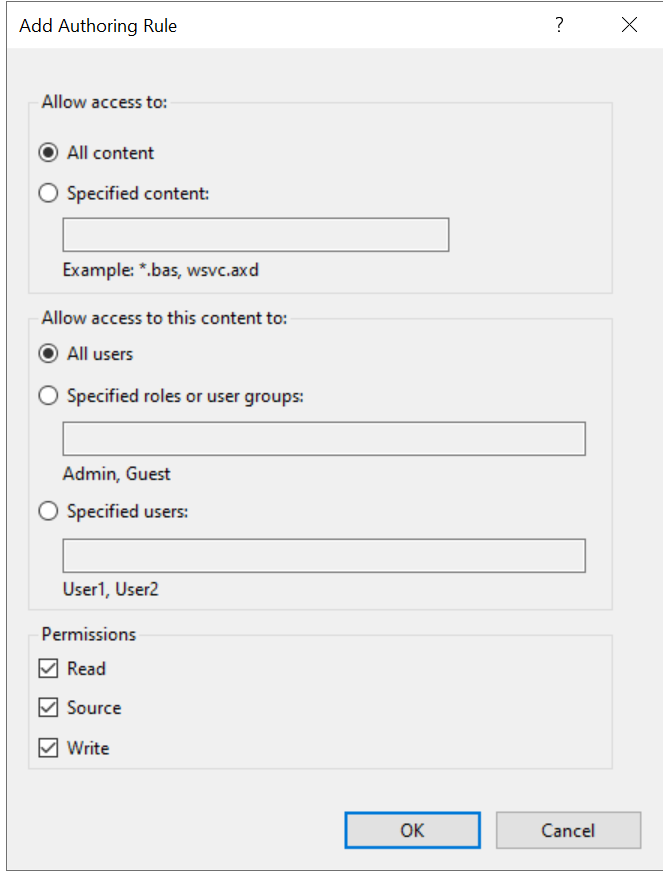
We need to permit read/write operations on this share by adding an authoring rule:
我们需要通过添加创作规则来允许对此共享进行读/写操作:
Last but not least, we need to enable NTLM authentication and disable all the other methods:
最后但并非最不重要的一点是,我们需要启用 NTLM 身份验证并禁用所有其他方法:

EXPLOITING CONTEXT SWAPPING WITH HTTP/WEBDAV
利用 HTTP/WEBDAV 进行上下文交换
In our latest LocalPotato release, we have added and “hardcoded” this method with http/webdav protocol. The tool will perform an arbitrary file write with SYSTEM privileges in the location specified in the webdav share with a static content of “we always love potatoes”. Refer to the source code for all the details, it’s not black magic ![]()
在我们最新的 LocalPotato 版本中,我们使用 http/webdav 协议添加并“硬编码”了此方法。该工具将在 webdav 共享中指定的位置以 SYSTEM 权限执行任意文件写入,静态内容为“我们总是喜欢土豆”。有关所有详细信息,请参阅源代码,这不是黑魔法 ![]()

You can certainly modify the code and tailor it to your specific needs, depending on the situation you encounter ![]()
您当然可以修改代码并根据您的特定需求进行定制,具体取决于您遇到 ![]() 的情况
的情况
原文始发于Decoder’s Blog:LocalPotato HTTP edition