Special thanks to Adrian Hetman, Alejandro Munoz-McDonald, Ivan Benavides, and Leon Spacewalker.
特别感谢Adrian Hetman,Alejandro Munoz-McDonald,Ivan Benavides和Leon Spacewalker。
Top 7 Strategies for Smart Contract Bug Hunting
智能合约漏洞搜寻的 7 大策略
Hunting for smart contract bugs can be a ludicrously well-paying job, and it’s also an integral part of protecting the ecosystem from hacks. I recently had the pleasure of interviewing a developer who found a $7 billion dollar bug—and was paid $2.2M for reporting it.
寻找智能合约漏洞可能是一项高薪可笑的工作,也是保护生态系统免受黑客攻击不可或缺的一部分。我最近有幸采访了一位开发人员,他发现了一个价值 70 亿美元的漏洞,并因报告它而获得了 2.2M 美元的报酬。
In this blog, we’re going to go through the bug that this developer found and how it had the potential to compromise $7b in value before offering some strategies and tools that will help you find bugs.
在这篇博客中,我们将介绍该开发人员发现的错误,以及它如何有可能损害 70 亿美元的价值,然后再提供一些可以帮助您找到错误的策略和工具。
Let’s dive in. 让我们潜入。
Polygon Smart Contract Bug Example
多边形智能合约错误示例
Build Up 建立起来
On May 31, 2020, the Matic blockchain went live (Matic would later be rebranded as Polygon). Polygon is an EVM-compatible blockchain known for it’s low gas fees and short block time. The chain has recently begun exploring zk-rollup technology.
2020 年 5 月 31 日,Matic 区块链上线(Matic 后来更名为 Polygon)。Polygon是一个与EVM兼容的区块链,以其低汽油费和短的区块时间而闻名。该连锁店最近开始探索zk-rollup技术。
If you take a look at block 0 of Polygon, the absolute first block of the blockchain, also known as its “genesis” block, you’ll see 10 transactions. One of these transactions created a contract called MRC20.
如果你看一下Polygon的区块0,区块链的绝对第一个区块,也被称为它的“创世”区块,你会看到10笔交易。其中一笔交易创建了一个名为MRC20的合约。
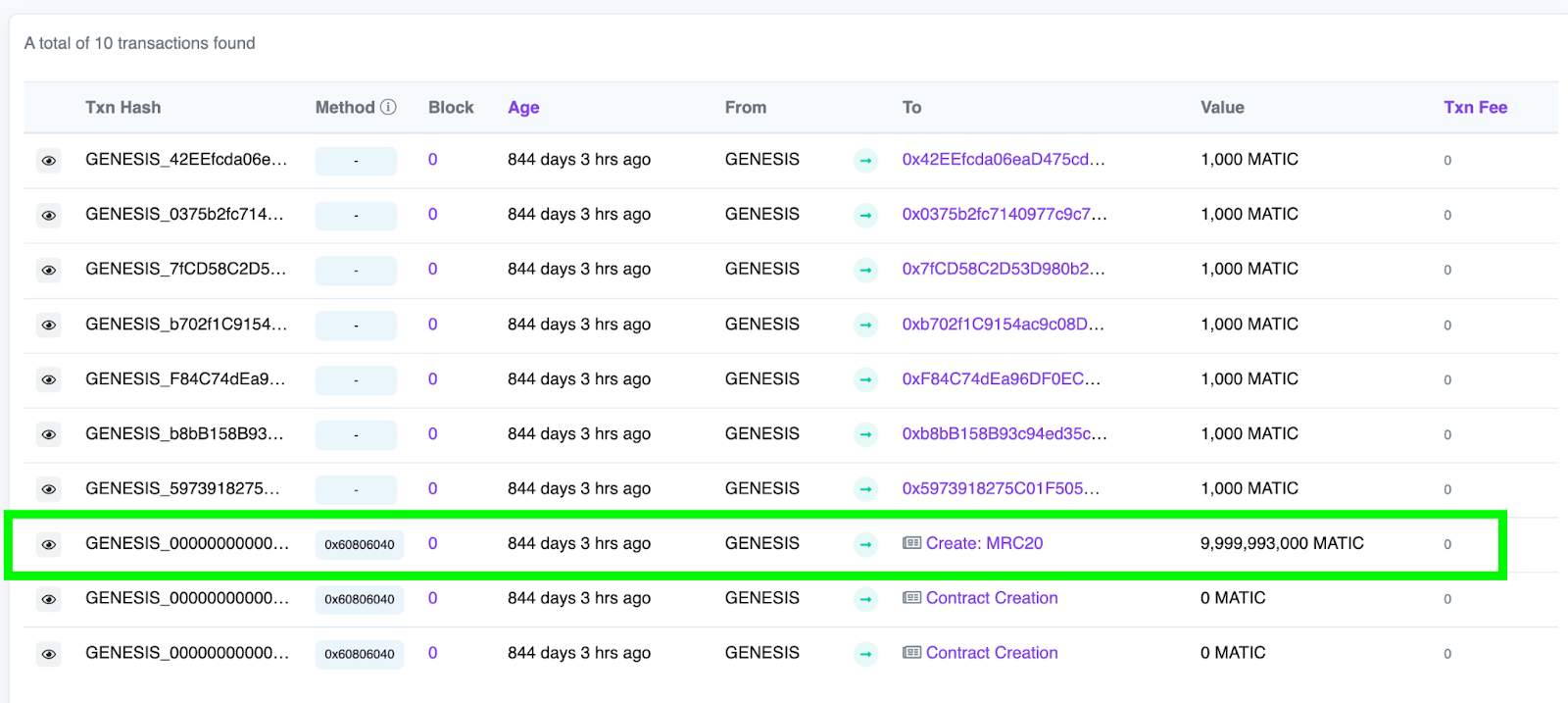
What is this contract? 这个合同是什么?
When we send a native blockchain token we have to spend gas to do so. So the Polygon team deployed a contract that allows you to sign a transaction to send someone ETH, with someone else able to pay the gas fee for this transaction. Known as a “meta transaction,” this capability was popularized with the introduction of EIP-712.
当我们发送原生区块链代币时,我们必须花费汽油才能这样做。因此,Polygon 团队部署了一份合同,允许您签署交易以发送某人 ETH,其他人可以支付此交易的 gas 费用。此功能被称为“元事务”,随着 EIP-712 的引入而普及。
You can see that this contract was given almost 10 billion MATIC tokens in order to help facilitate these gasless transactions. However, this clever contract contained a vulnerability that could have potentially been exploited to drain the entire balance!
您可以看到,该合约获得了近 100 亿个 MATIC 代币,以帮助促进这些无气交易。但是,这个聪明的合同包含一个漏洞,该漏洞可能被利用来耗尽整个余额!
On December 3rd, 2021 the hero of the story, pseudo-anon developer Leon Spacewalker, submitted a report to the Immunefi bug bounty program laying out the details of this exact function. A second hero, who we will just call Whitehat2, also reported the vulnerability a day later.
2021 年 12 月 3 日,故事的主人公、伪匿名开发者 Leon Spacewalker 向 Immunefi 漏洞赏金计划提交了一份报告,列出了这个确切功能的细节。第二位英雄,我们称之为Whitehat2,也在一天后报告了这个漏洞。
Around 800,000 MATIC tokens were stolen before the chain was finally forked, rolled back, and fixed December 5th, 2021.
在链最终分叉、回滚并修复 2021 年 12 月 5 日之前,大约有 800,000 个 MATIC 代币被盗。
This leaves us with some more questions: What was the vulnerability? How did it stay undiscovered for so long? How was it found?
这给我们留下了更多的问题:漏洞是什么?它是如何长期未被发现的?它是怎么找到的?
The Exploit 漏洞利用
Below is the function that facilitates these gasless transactions.
以下是促进这些无气交易的功能。
function transferWithSig(
bytes calldata sig,
uint256 amount,
bytes32 data,
uint256 expiration,
address to
) external returns (address from) {
require(amount > 0);
require(
expiration == 0 || block.number <= expiration,
"Signature is expired"
);
bytes32 dataHash = getTokenTransferOrderHash(
msg.sender,
amount,
data,
expiration
);
require(disabledHashes[dataHash] == false, "Sig deactivated");
disabledHashes[dataHash] = true;
from = ecrecovery(dataHash, sig);
_transferFrom(from, address(uint160(to)), amount);
}
At first glance, it seems harmless: It takes the signature of the user, how many tokens and who they want to send them to, and any further data, along with an expiration date for the transaction.
乍一看,它似乎是无害的:它需要用户的签名,多少代币以及他们想要将它们发送给谁,以及任何进一步的数据,以及交易的到期日期。
It runs some requires, gets the data hash in order to send the meta transaction, makes sure the data hash hasn’t been used, and does this ecrecovery function.
它运行一些需求,获取数据哈希以发送元事务,确保数据哈希未被使用,并执行此功能 ecrecovery 。
This function is essentially a wrapper for the Solidity ecrecover function.
此函数本质上是 Solidity ecrecover 函数的包装器。
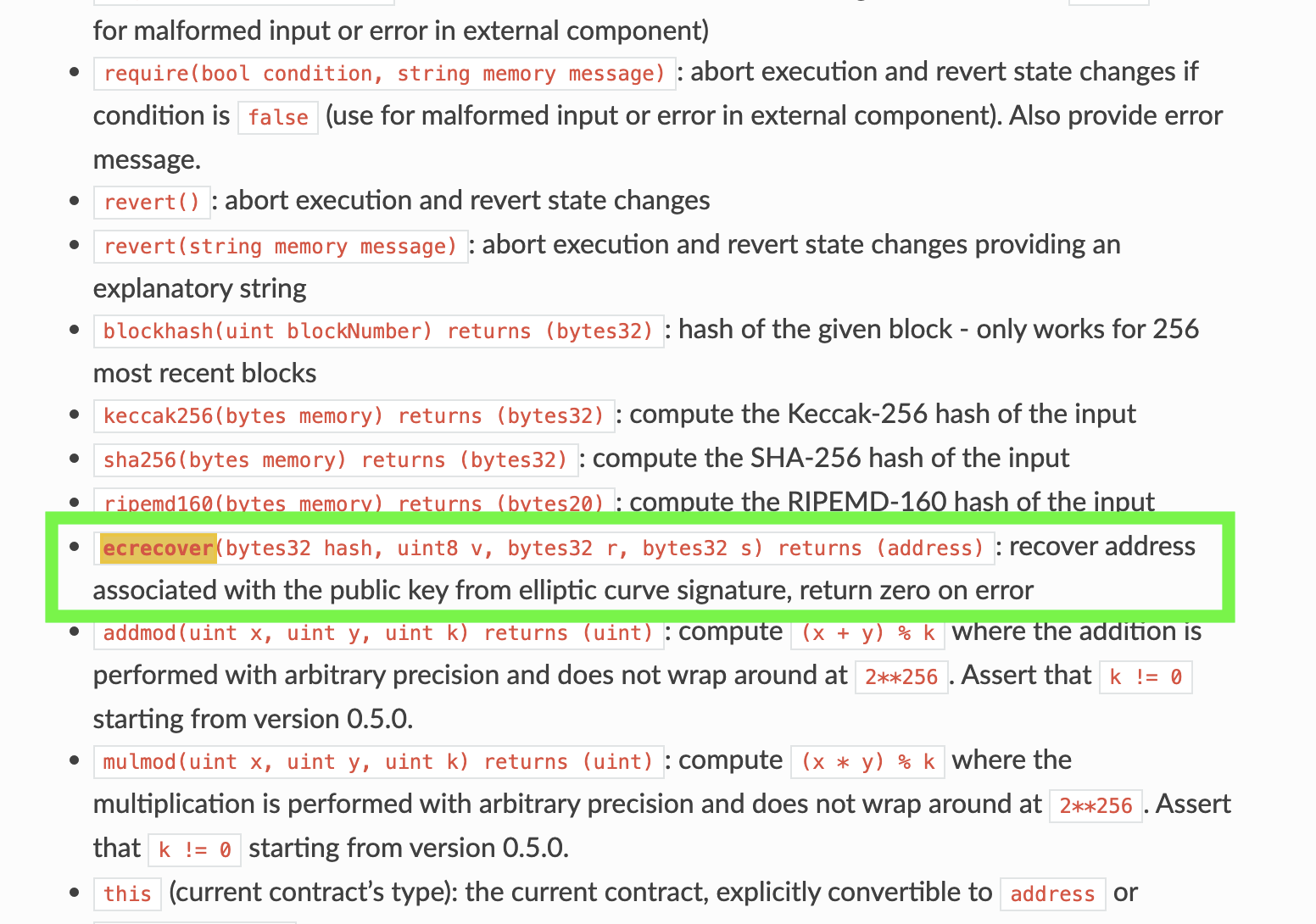
Solidity ecrecover 函数包装器。
This function is how we can verify where signed transactions are coming from. You’ll notice, even in the Solidity documentation, it says it will “return zero on error”. The ecrecovery function copied this, and if it had an issue, it would return 0. Which, as many developers know, can be scary. If it returns zero on error, that means that we should check to make sure that the returned address isn’t zero, right?
此功能是我们如何验证签名交易的来源。您会注意到,即使在 Solidity 文档中,它也说它将“错误时返回零”。该 ecrecovery 函数复制了它,如果它有问题,它将返回 0。正如许多开发人员所知,这可能很可怕。如果它在错误时返回零,这意味着我们应该检查以确保返回的地址不为零,对吧?
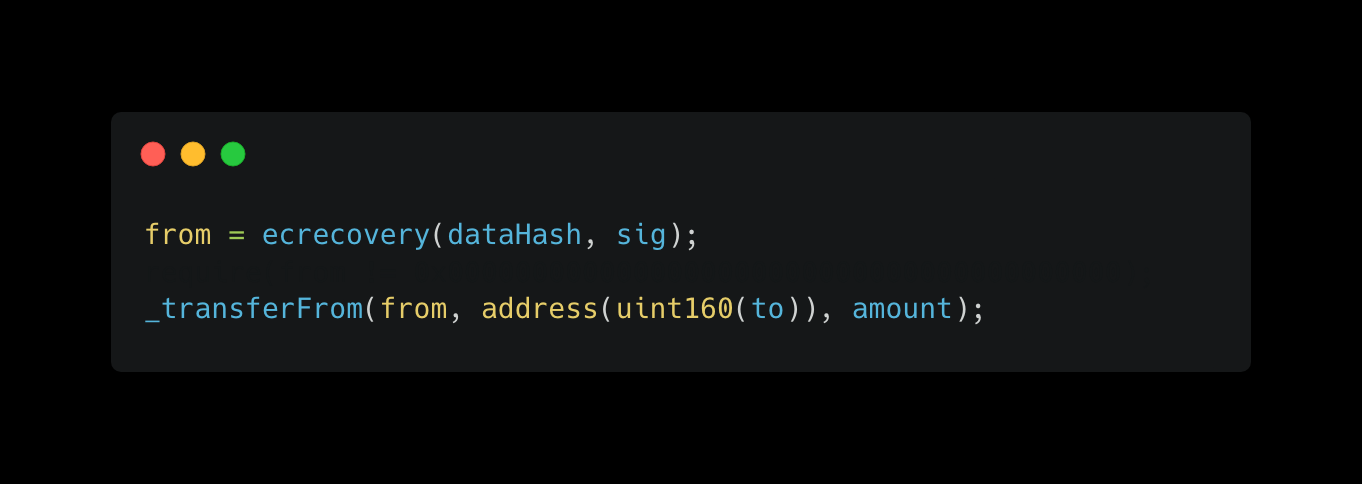
Here’s the actual code: 下面是实际代码:
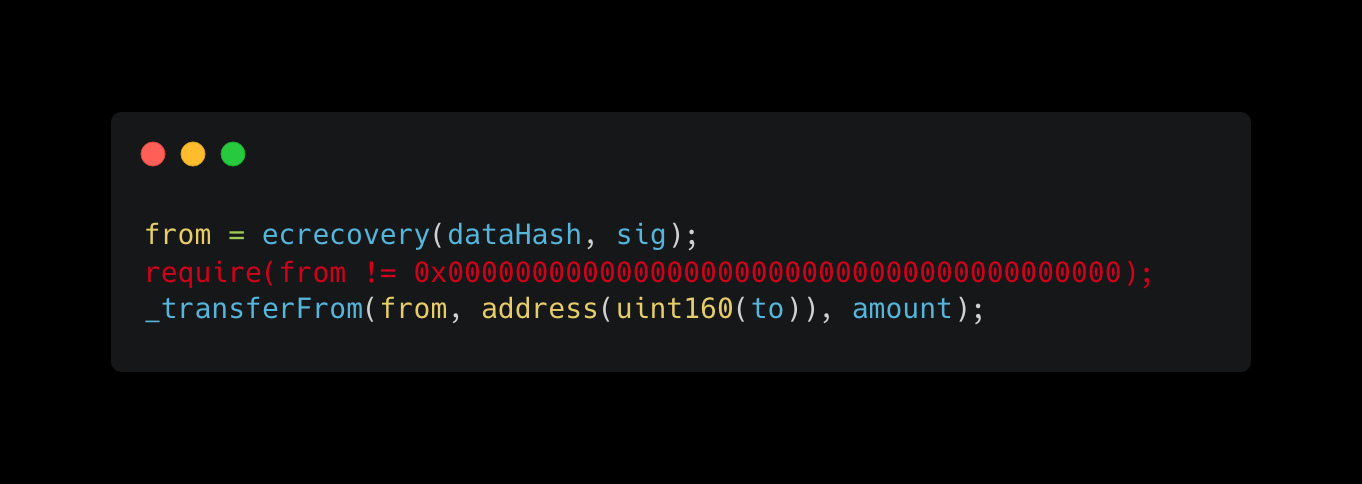
Here’s what should probably be there:
以下是可能应该存在的内容:
So we don’t perform a check on the address to make sure it didn’t result in an error. Not a problem. The last line of code in our transferWithSig function does the actual transfer, surely we will perform some sort of check there, right?
因此,我们不会对地址执行检查以确保它不会导致错误。没问题。我们 transferWithSig 函数中的最后一行代码执行实际传输,我们肯定会在那里执行某种检查,对吧?
function _transfer(address sender, address recipient, uint256 amount)
internal
{
require(recipient != address(this), "can't send to MRC20");
address(uint160(recipient)).transfer(amount); // It just sends the money!
emit Transfer(sender, recipient, amount);
}
The _transferFrom function just called our _transfer function, shown above. You’ll notice it doesn’t check to make sure the from address has enough money.
该 _transferFrom 函数刚刚调用了我们的 _transfer 函数,如上所示。您会注意到它不会检查以确保 from 地址有足够的钱。
This means that someone could send an invalid signature, which would result in a zero address returned from ecrecovery, but the MRC20 contract would still send the to address an amount of money. This is how that 9,999,993,000 MATIC could be drained, since the MRC20 contract sends the money directly from itself!
这意味着有人可以发送无效的签名,这将导致从ecrecovery返回零地址,但MRC20合约仍然会向地址 to 发送一定金额。这就是 9,999,993,000 MATIC 的流失方式,因为 MRC20 合约直接从自身发送资金!
A check to make sure that the from address has enough money for this signed transaction would have prevented this issue.
检查以确保 from 地址有足够的钱用于此签名交易可以防止此问题。
How Did the Smart Contract Bug Elude Discovery for So Long?
智能合约漏洞是如何躲避发现这么久的?
What’s odd to me is that, after the vulnerability laying dormant for almost a year and a half, it was discovered by Leon, another white hat, and a hacker within the span of a few days.
令我感到奇怪的是,在漏洞休眠了近一年半之后,它被Leon,另一个白帽子和一名黑客在几天内发现。
Seems fishy. But the Immunefi team told me this can often happen. Some exploits can become popular based on an article, write-up, or challenge and people then start looking for that vulnerability, resulting in several people finding it at the same time.
似乎很腥。但Immunefi团队告诉我,这种情况经常发生。一些漏洞利用可能会根据一篇文章、文章或挑战而变得流行,然后人们开始寻找该漏洞,导致几个人同时找到它。
But more likely is that it turns out that polygon verified the contract on Polygonscan around this time – so that was when people really started to look at it.
但更有可能的是,事实证明,Polygon大约在这个时候验证了Polygonscan上的合同 – 所以那是人们真正开始关注它的时候。
Maybe there is more to the story, but maybe not.
In any case, let’s use this bug as a teachable moment and look at some of the skills Leon and other bug hunters use to find bugs, helping protect the Web3 ecosystem.
无论如何,让我们将此错误用作可教的时刻,看看 Leon 和其他错误猎人用来查找错误的一些技能,以帮助保护 Web3 生态系统。
Top 7 Strategies 前 7 大策略
Now, we are going to learn the skills Leon and other bug hunters use to find these vulnerabilities and claim bug bounties. This list of tips assumes you already know the basics of smart contracts, so yes, learning Solidity is a prerequisite.
现在,我们将学习Leon和其他漏洞猎人用来发现这些漏洞并领取漏洞赏金的技能。这个提示列表假设你已经了解智能合约的基础知识,所以是的,学习Solidity是一个先决条件。
Use these superpowers for ethical hacking, and please remember to responsibly disclose any vulnerabilities you find.
使用这些超能力进行道德黑客攻击,请记住负责任地披露您发现的任何漏洞。
A lot of the work of finding vulnerabilities comes from looking at the code and running tools like slither. For this $2.2M payout, Leon said he was able to find the bug by looking line-by-line at the smart contract code, so remember, finding vulnerabilities is often a huge manual lift!
查找漏洞的很多工作都来自查看代码和运行像slither这样的工具。对于这笔2.2M美元的支出,Leon说他能够通过逐行查看智能合约代码来找到漏洞,所以请记住,发现漏洞通常是一个巨大的手动提升!
In addition to the practical tips below, Leon’s biggest takeaway was for smart contract bug hunters to “find your edge,” but what does he mean by that? Typically, this means finding that thing that sets you apart from other hackers. We as a community need to cover every corner of the smart contract space, so find a section that you are specifically good at and excel.
除了下面的实用技巧外,Leon最大的收获是智能合约漏洞猎人“找到你的优势”,但他的意思是什么?通常,这意味着找到使您与其他黑客区分开来的东西。作为一个社区,我们需要覆盖智能合约空间的每个角落,所以找到一个你特别擅长和擅长的部分。
Here are the seven strategies and tips to help find your edge, to make you a successful smart contract bug hunter.
以下是帮助您找到优势的七种策略和技巧,使您成为成功的智能合约错误猎人。
1. Find a Project and Search For Bugs
1. 查找项目并搜索错误
The first way you can find bugs is to know every inch of how a protocol works. This is one of the first skills every smart contract bug hunter needs to be learn: the ability to understand a protocol end to end.
找到错误的第一种方法是了解协议工作原理的每一寸。这是每个智能合约漏洞猎人首先需要学习的技能之一:端到端理解协议的能力。
Go through docs, try to reimplement a protocol yourself, and view transactions through that protocol on a block explorer.
Leon said this strategy works for other hunters but not him. He focuses on the next three, but it’s important for every bug hunter to be able to do this.
莱昂说,这种策略适用于其他猎人,但不适用于他。他专注于接下来的三个,但对于每个虫子猎人来说,能够做到这一点是很重要的。
2. Find a Bug and Search For Projects
2. 查找错误并搜索项目
An easier approach to hunting for bugs is to find a bug that not a lot of people know about and try to see which protocols have implemented it.
寻找错误的更简单方法是找到一个没有多少人知道的错误,并尝试查看哪些协议实现了它。
This strategy takes a lot of research, as there are a lot of people working on exposing bugs to the general public.
这种策略需要大量的研究,因为有很多人致力于向公众公开错误。
You first need to understand all the basic smart contract exploits, and then their advanced versions. You need to be aware of best practices and see if there are protocols that have not followed them.
您首先需要了解所有基本的智能合约漏洞,然后是它们的高级版本。您需要了解最佳实践,并查看是否有协议未遵循它们。
Once you find a smart contract bug you think a lot of projects might not have protected against, start searching for that bug. Get really familiar with this new bug and how to find it. And be sure to write a blog or some kind of post to help other smart contract developers who run into this bug protect themselves.
一旦你发现一个智能合约错误,你认为很多项目可能没有保护,就开始搜索这个错误。非常熟悉这个新错误以及如何找到它。请务必写一篇博客或某种帖子,以帮助遇到此错误的其他智能合约开发人员保护自己。
3. Be Fast 3. 要快
Projects that want bug hunters to look at their smart contracts need to sign up for bug bounty programs like Immunefi. And you’ll want to be one of the first developers to find the new bounties. If you start looking at a contract before other hunters, you’ll have more time to find a bug than other hunters.
希望漏洞猎人查看他们的智能合约的项目需要注册像Immunefi这样的漏洞赏金计划。你会想成为第一批找到新赏金的开发者之一。如果你在其他猎人之前开始查看合同,你将比其他猎人有更多的时间来发现虫子。
There are a few ways to be fast—one of the ways Leon was able to find the smart contract vulnerability before others was by having notifications on for the Immunifi updates Discord channel. He received a notification anytime a new project came in, or a project was updated. Tools like this can help you get to digging into code before anyone else does.
有几种方法可以快速 – Leon能够在其他人之前找到智能合约漏洞的方法之一是为Immunifi更新Discord频道打开通知。每当有新项目进来或项目更新时,他都会收到通知。像这样的工具可以帮助你在其他人之前深入研究代码。
4. Be Creative 4. 要有创意
Another way Leon was able to get an edge, was traversing community forums, and finding out they were thinking about submitting a bug. He’d then start looking at the smart contracts even before the bounty was approved. This gave him way more time to look at a contract than other developers, since they would wait for a bug bounty to be submitted.
Leon 能够获得优势的另一种方式是浏览社区论坛,并发现他们正在考虑提交错误。然后,甚至在赏金获得批准之前,他就开始查看智能合约。这给了他比其他开发人员更多的时间来查看合同,因为他们会等待提交漏洞赏金。
5. Know Your Tooling 5. 了解您的工具
Bug hunters use tools like the VSCode Solidity visual developer extension, Hardhat, Foundry, Brownie, Dune, Etherscan, plus a host of others.
Bug hunter使用VSCode Solidity可视化开发人员扩展,Hardhat,Foundry,Brownie,Dune,Etherscan等工具。
A typical bug hunting strategy might be loading up VSCode, adding the code to VSCode with the Solidity visual extension, and going line by line looking for common bugs or bad best practices.
典型的错误搜寻策略可能是加载VSCode,使用Solidity可视化扩展将代码添加到VSCode,然后逐行查找常见错误或不良最佳实践。
After finding a weakness, setting up a testing environment to run tests on the contract is a good next step. You can often reuse a lot of the tests the developers of the protocol originally used.
发现弱点后,设置测试环境以在合约上运行测试是一个很好的下一步。您通常可以重用协议开发人员最初使用的许多测试。
6. Don’t Be Afraid of Audited Projects
6. 不要害怕被审计的项目
Not much else to say here. Audit firms make mistakes. Many of the projects Leon found vulnerabilities for had been audited by top firms.
这里没什么好说的。审计公司会犯错误。Leon发现的许多项目漏洞都经过了顶级公司的审计。
Using the skills we talked about in this blog can be the difference for you to find these issues!
使用我们在本博客中讨论的技能可以使您找到这些问题!
7. Industry-Specific Knowledge
7. 行业特定知识
One of the biggest advantages in finding your edge is specializing in a specific niche. If you understand one area incredibly well, you’ll have the advantage of knowing how all the functions interact with each other. If you’re a phenomenal smart contract vulnerability expert but don’t know anything about DeFi, it’ll be hard to find vulnerabilities in DeFi contracts. For example, a lot of developers understand code, but don’t understand financial primitives.
找到优势的最大优势之一是专注于特定的利基市场。如果你非常了解一个领域,你将有了解所有功能如何相互作用的优势。如果你是一个非凡的智能合约漏洞专家,但对DeFi一无所知,那么在DeFi合约中很难找到漏洞。例如,许多开发人员理解代码,但不了解金融原语。
You could get incredibly good at understanding decentralized exchanges, borrowing protocols, or maybe just NFTs!
您可以非常擅长理解去中心化交易所、借款协议,或者只是 NFT!
If you can become a master of security and a master of a certain vertical within Web3, you’ll be well-positioned to have a massive leg up on everyone else looking for bugs.
如果您可以成为 Web3 中某个垂直领域的安全大师和某个垂直领域的大师,那么您将处于有利地位,可以比其他寻找错误的其他人拥有巨大的优势。
Summary 总结
I hope this piece is useful to you in your smart contract bug-hunting journey. If you want to learn more about security when writing your smart contracts, be sure to check out Top Ten DeFi Security Best Practices.
我希望这篇文章对你的智能合约bug搜寻之旅有用。如果您想在编写智能合约时了解有关安全性的更多信息,请务必查看十大 DeFi 安全最佳实践。
And, as always, I hope to see you out there building and keeping the ecosystem a little safer.
而且,与往常一样,我希望看到你们在那里建立并保持生态系统更安全。
Links 链接
Change to Polygon contracts.
更改为多边形合同。
Previous Polygon contracts.
以前的多边形合同。
The opinions expressed within this post are solely the author’s and do not reflect the opinions and beliefs of the Chainlink Foundation or Chainlink Labs.
本文中表达的观点仅代表作者的观点,并不反映链链基金会或链链实验室的观点和信念。
原文始发于 Chainlink :Top 7 Strategies for Finding Smart Contract Vulnerabilities
转载请注明:Top 7 Strategies for Finding Smart Contract Vulnerabilities | CTF导航