
A new attack dubbed ‘WiKI-Eve’ can intercept the cleartext transmissions of smartphones connected to modern WiFi routers and deduce individual numeric keystrokes at an accuracy rate of up to 90%, allowing numerical passwords to be stolen.
一种名为“WiKI-Eve”的新攻击可以拦截连接到现代WiFi路由器的智能手机的明文传输,并以高达90%的准确率推断出单个数字击键,从而窃取数字密码。
WiKI-Eve exploits BFI (beamforming feedback information), a feature introduced in 2013 with WiFi 5 (802.11ac), which allows devices to send feedback about their position to routers so the latter can direct their signal more accurately.
WiKI-Eve利用BFI(波束成形反馈信息),这是2013年WiFi 5(802.11ac)引入的一项功能,该功能允许设备向路由器发送有关其位置的反馈,以便后者可以更准确地引导信号。
The problem with BFI is that the information exchange contains data in cleartext form, meaning that this data can be intercepted and readily used without requiring hardware hacking or cracking an encryption key.
BFI的问题在于信息交换包含明文形式的数据,这意味着这些数据可以被拦截并随时使用,而无需硬件黑客攻击或破解加密密钥。
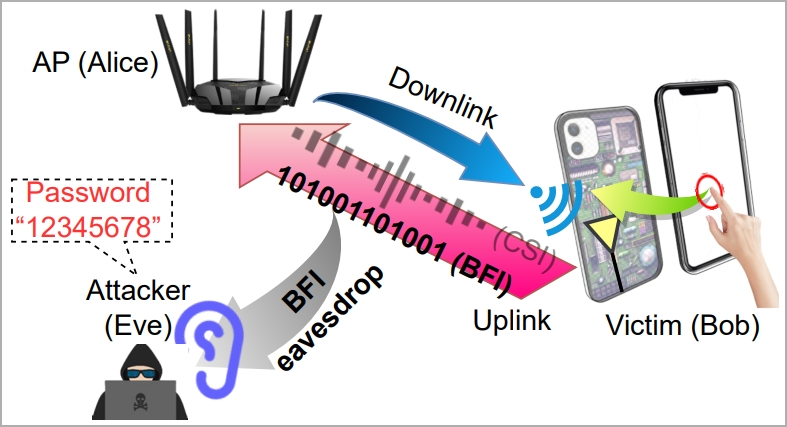
WiKI-Eve 攻击概述 (arxiv.org)
This security gap was discovered by a team of university researchers in China and Singapore, who tested the retrieval of potential secrets from these transmissions.
这个安全漏洞是由中国和新加坡的一组大学研究人员发现的,他们测试了从这些传输中检索潜在机密的方法。
The team found that it’s reasonably easy to identify numeric keystrokes 90% of the time, decipher 6-digit numerical passwords with an accuracy of 85%, and work out complex app passwords at an accuracy of roughly 66%.
该团队发现,在90%的时间内识别数字击键,以85%的准确率破译6位数字密码,并以大约66%的准确率计算出复杂的应用程序密码,这是相当容易的。
While this attack only works on numerical passwords, a study by NordPass showed that 16 out of 20 of the top passwords only used digits.
虽然这种攻击仅适用于数字密码,但NordPass的一项研究表明,20个顶级密码中有16个仅使用数字。
The WiKI-Eve attack WiKI-Eve 攻击
The WiKI-Eve attack is designed to intercept WiFi signals during password entry, so it’s a real-time attack that must be carried out while the target actively uses their smartphone and attempts to access a specific application.
WiKI-Eve攻击旨在在密码输入期间拦截WiFi信号,因此这是一种实时攻击,必须在目标积极使用智能手机并尝试访问特定应用程序时进行。
.jpg)
手指移动和敲击产生 BFI 信号变化 (arxiv.org)
The attacker must identify the target using an identity indicator on the network, like a MAC address, so some preparatory work is required.
攻击者必须使用网络上的身份指示器(如 MAC 地址)识别目标,因此需要进行一些准备工作。
“In reality, Eve can acquire this information beforehand by conducting visual and traffic monitoring concurrently: correlating network traffic originating from various MAC addresses with users’ behaviors should allow Eve to link Bob’s physical device to his digital traffic, thereby identifying Bob’s MAC address,” explains the researchers.
“实际上,Eve可以通过同时进行视觉和流量监控来事先获取这些信息:将来自各种MAC地址的网络流量与用户的行为相关联,应该允许Eve将Bob的物理设备链接到他的数字流量,从而识别Bob的MAC地址,”研究人员解释说。
In the main phase of the attack, the victim’s BFI time series during password entry is captured by the attacker using a traffic monitoring tool like Wireshark.
在攻击的主要阶段,攻击者使用Wireshark等流量监控工具捕获受害者在密码输入期间的BFI时间序列。
Each time the user presses a key, it impacts the WiFi antennas behind the screen, causing a distinct WiFi signal to be generated.
每次用户按下一个键时,它都会撞击屏幕后面的WiFi天线,从而产生明显的WiFi信号。
“Though they only account for part of the downlink CSIs concerning the AP side, the fact that on-screen typing directly impacts the Wi-Fi antennas (hence channels) right behind the screen (see Figure 1) allows BFIs to contain sufficient information about keystrokes,” reads the paper.
“虽然它们只占AP端下行链路CSI的一部分,但屏幕上的打字直接影响屏幕后面的Wi-Fi天线(因此是信道)(见图1)这一事实允许BFI包含有关击键的足够信息,”该论文写道。
However, the paper emphasizes that the recorded BFI series might blur boundaries between keystrokes, so they developed an algorithm for parsing and restoring usable data.
然而,该论文强调,记录的BFI系列可能会模糊击键之间的界限,因此他们开发了一种解析和恢复可用数据的算法。

用于解析捕获数据的神经模型 (arxiv.org)
To tackle the challenge of filtering out factors that interfere with the results, like typing style, typing speed, adjacent keystrokes, etc. the researchers use machine learning called “1-D Convolutional Neural Network.”
为了应对过滤掉干扰结果的因素的挑战,如打字风格、打字速度、相邻击键等,研究人员使用称为“一维卷积神经网络”的机器学习。
The system is trained to consistently recognize keystrokes regardless of typing styles through the concept of “domain adaptation,” which comprises a feature extractor, a keystroke classifier, and a domain discriminator.
该系统经过训练,通过“域适应”的概念(包括特征提取器、击键分类器和域鉴别器)来一致地识别击键,无论键入样式如何。
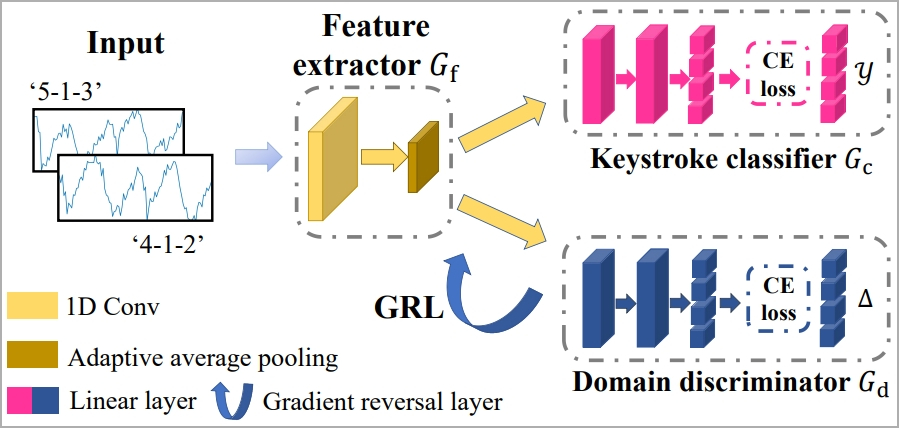
用于WiKI-Eve的ML框架训练(arxiv.org)
Finally, a “Gradient Reversal Layer” (GRL) is applied to suppress domain-specific features, helping the model learn consistent keystroke representations across domains.
最后,应用“梯度反转层”(GRL)来抑制特定于域的特征,帮助模型学习跨域的一致击键表示。
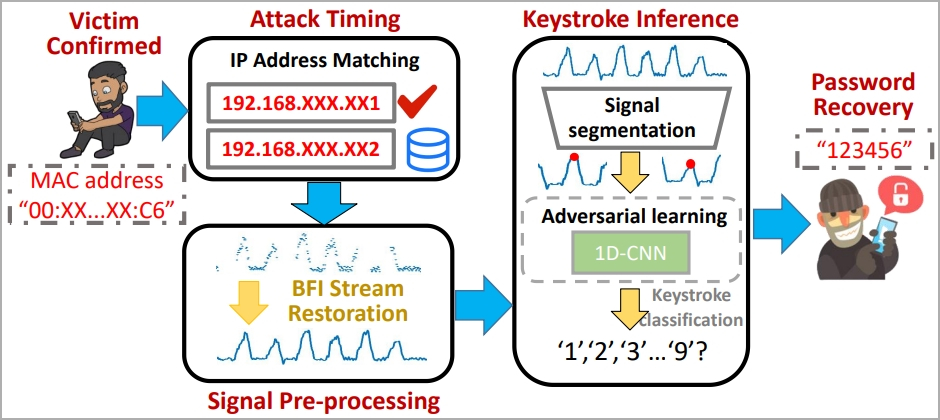
WiKI-Eve 攻击步骤 (arxiv.org)
Attack results 攻击结果
The researchers experimented with WiKI-Eve using a laptop and WireShark but also pointed out that a smartphone can also be used as an attacking device, although it might be more limited in the number of supported WiFi protocols.
研究人员使用笔记本电脑和WireShark对WiKI-Eve进行了实验,但也指出智能手机也可以用作攻击设备,尽管它在支持的WiFi协议数量上可能受到更多限制。
The captured data was analyzed using Matlab and Python, and the segmentation parameters were set to values shown to produce the best results.
使用Matlab和Python分析捕获的数据,并将分割参数设置为显示的值以产生最佳结果。
Twenty participants connected to the same WiFi access point used different phone models. They typed various passwords using a mix of active background apps and varying typing speeds while measurements were taken from six different locations.
连接到同一WiFi接入点的20名参与者使用不同的手机型号。他们使用活动的后台应用程序和不同的打字速度混合输入各种密码,同时从六个不同的位置进行测量。
The experiments showed that WiKI-Eve’s keystroke classification accuracy remains stable at 88.9% when sparse recovery algorithm and domain adaptation are used.
实验表明,采用稀疏恢复算法和域自适应时,WiKI-Eve的击键分类准确率稳定在88.9%。
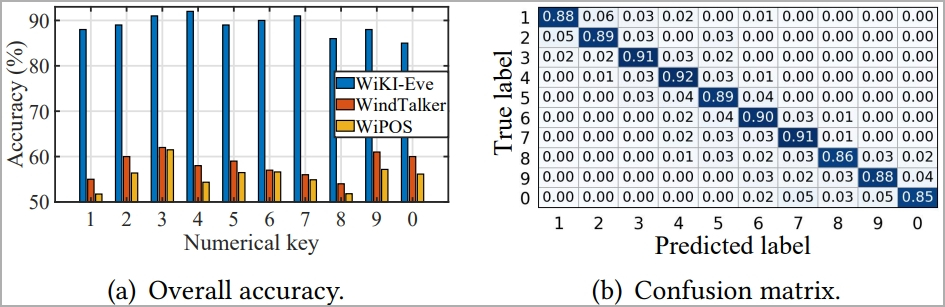
WiKI-Eve 与 CSI 定位模型相比的总体准确性 (arxiv.org)
For six-digit numerical passwords, WiKI-Eve could infer them with an 85% success rate in under a hundred attempts, remaining consistently above 75% in all tested environments.
对于六位数的数字密码,WiKI-Eve可以在不到一百次尝试中以85%的成功率推断出它们,在所有测试环境中始终保持在75%以上。
However, the distance between the attacker and the access point is crucial to this performance. Increasing that distance from 1m to 10m resulted in a 23% successful guess rate drop.
但是,攻击者和接入点之间的距离对于此性能至关重要。将距离从 1m 增加到 10m 导致成功猜测率下降 23%。
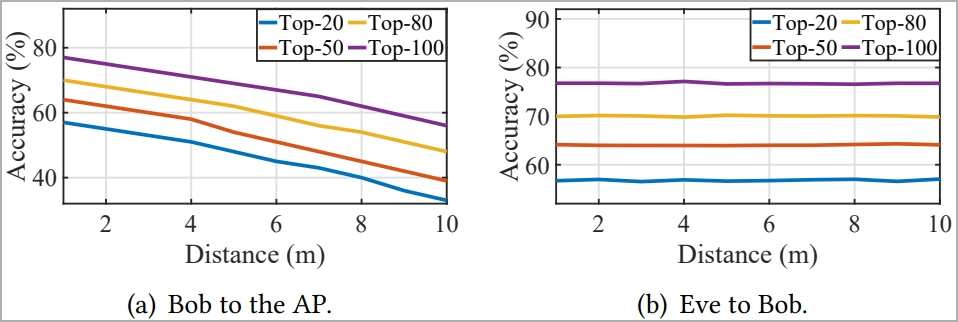
距离对猜测性能的影响(arxiv.org)
The researchers also experimented with retrieving user passwords for WeChat Pay, emulating a realistic attack scenario, and found that WiKI-Eve deduced the passwords correctly at a rate of 65.8%.
研究人员还尝试检索微信支付的用户密码,模拟真实的攻击场景,发现WiKI-Eve以65.8%的比率正确推断出密码。
The model consistently predicted the correct password within its top 5 guesses in over 50% of the 50 tests conducted. This means an attacker has a 50% chance of gaining access before hitting the security threshold of five incorrect password attempts, after which the app locks.
该模型在进行的 50 次测试中超过 50% 的测试中始终预测其前 5 次猜测中的正确密码。这意味着攻击者有 50% 的机会获得访问权限,然后达到五次错误密码尝试的安全阈值,之后应用程序锁定。
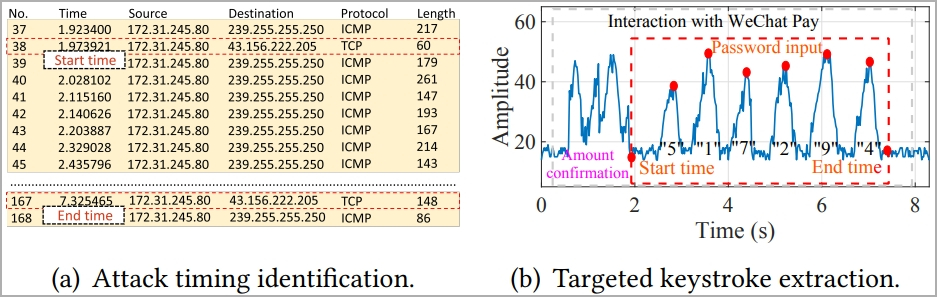
攻击微信密码(arxiv.org)
In conclusion, the paper shows that adversaries can deduce secrets without hacking access points and by simply using network traffic monitoring tools and machine learning frameworks.
总之,该论文表明,攻击者可以在不入侵接入点的情况下推断出秘密,只需使用网络流量监控工具和机器学习框架即可。
This calls for heightened security in WiFi access points and smartphone apps, like potentially keyboard randomization, encryption of data traffic, signal obfuscation, CSI scrambling, WiFi channel scrambling, and more.
这要求提高WiFi接入点和智能手机应用程序的安全性,例如潜在的键盘随机化,数据流量加密,信号混淆,CSI加扰,WiFi信道加扰等。
原文始发于Bill Toulas :New WiKI-Eve attack can steal numerical passwords over WiFi
转载请注明:New WiKI-Eve attack can steal numerical passwords over WiFi | CTF导航