Chinese Hacking Group Exploits Barracuda Zero-Day to Target Government, Military, and Telecom
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway (ESG) appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign.
Mandiant, which is tracking the activity under the name UNC4841, described the threat actor as “highly responsive to defensive efforts” and capable of actively tweaking their modus operandi to maintain persistent access to targets.
“UNC4841 deployed new and novel malware designed to maintain presence at a small subset of high priority targets that it compromised either before the patch was released, or shortly following Barracuda’s remediation guidance,” the Google-owned threat intelligence firm said in a new technical report published today.
Almost a third of the identified affected organizations are government agencies. Interestingly enough, some of the earliest compromises appear to have taken place on a small number of devices geolocated to mainland China.
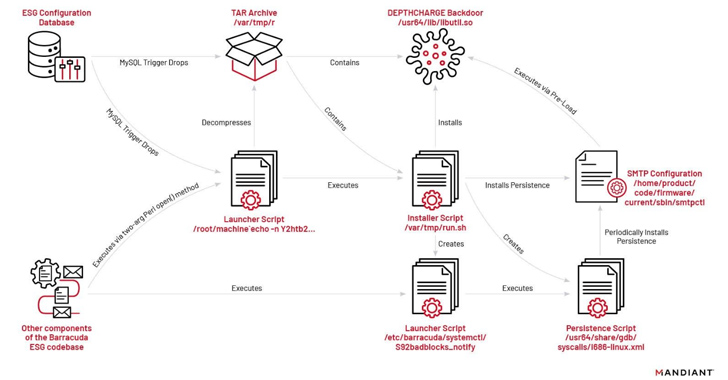
The attacks entail the exploitation of CVE-2023-2868 to deploy malware and conduct post-exploitation activities. In select cases, the intrusions have led to the deployment of additional malware, such as SUBMARINE (aka DEPTHCHARGE), to maintain persistence in response to remediation endeavors.
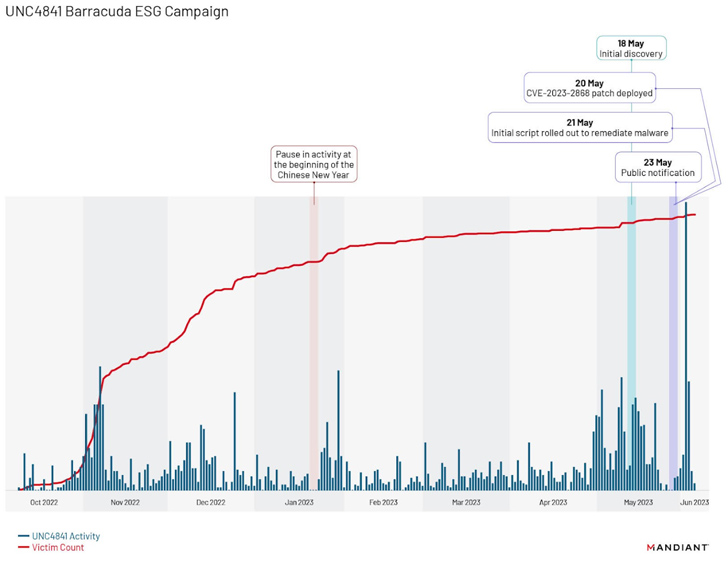
Further analysis of the campaign has revealed a “distinct fall off in activity from approximately January 20 to January 22, 2023,” coinciding with the beginning of the Chinese New Year, followed by two surges, one after Barracuda’s public notification on May 23, 2023, and a second one in early June 2023.

The latter is said to have involved the attacker “attempting to maintain access to compromised environments via the deployment of the new malware families SKIPJACK, DEPTHCHARGE, and FOXTROT / FOXGLOVE.”
While SKIPJACK is a passive implant that registers a listener for specific incoming email headers and subjects before decoding and running their content, DEPTHCHARGE is pre-loaded into the Barracuda SMTP (BSMTP) daemon using the LD_PRELOAD environment variable, and retrieves encrypted commands for execution.
The earliest use of DEPTHCHARGE dates back to May 30, 2023, merely days after Barracuda publicly disclosed the flaw. Mandiant said it observed the malware being rapidly deployed to a subset of targets, indicating a high level of preparation and an attempt to persist within high-value environments.
“It also suggests that despite this operation’s global coverage, it was not opportunistic, and that UNC4841 had adequate planning and funding to anticipate and prepare for contingencies that could potentially disrupt their access to target networks,” the company explained.
Roughly 2.64 percent of the total compromised appliances are estimated to have been infected with DEPTHCHARGE. This victimology spans U.S. and foreign government entities, as well as high-tech and information technology providers.
The third malware strain, also selectively delivered to targets, is FOXTROT, a C++ implant that’s launched using a C-based program dubbed FOXGLOVE. Communicating via TCP, it comes with features to capture keystrokes, run shell commands, transfer files, and set up a reverse shell.
What’s more, FOXTROT shares overlaps with an open-source rootkit called Reptile, which has been extensively used by multiple Chinese hacking crews in recent months. This also comprises UNC3886, a threat actor linked to the zero-day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system.
“FOXTROT and FOXGLOVE are also notable in that they are the only malware families observed being used by UNC4841 that were not specifically designed for Barracuda ESGs,” Mandiant pointed out. “Based on functionality, FOXTROT was likely also intended to be deployed to other Linux-based devices within a network to enable lateral movement and credential theft.”
Another aspect that makes FOXGLOVE and FOXTROT stand out is the fact that they have been the most selectively deployed among all malware families used by UNC4841, exclusively using it to target government or government-related organizations.
The adversarial collective has also been detected performing internal reconnaissance and subsequent lateral movement actions within a limited number of victim environments. More than one case entailed utilizing Microsoft Outlook Web Access (OWA) to attempt to log in to mailboxes for users within the organizations.

As an alternative form of remote access, the advanced persistent threat (APT) actor created accounts containing four randomly generated characters within the etc/passwd file on roughly five percent of the previously impacted appliances.
UNC4841’s Chinese connections are further bolstered by the infrastructure commonalities between the group and another uncategorized cluster codenamed UNC2286, which, in turn, shares overlaps with other Chinese espionage campaigns tracked as FamousSparrow and GhostEmperor.
The latest disclosure comes against the backdrop of the U.S. Federal Bureau of Investigation (FBI) urging impacted customers to replace their ESG appliances with immediate effect, citing continued risk.
“UNC4841 is a well-resourced actor that has utilized a wide range of malware and purpose-built tooling to enable their global espionage operations,” the company said, calling out the threat actor’s ability to selectively deploy more payloads to specific victim environments.
“Shared infrastructure and techniques for anonymization are common amongst Chinese cyber espionage actors, as is shared tooling and likely malware development resources. It is likely that we will continue to observe Chinese cyber espionage operations targeting edge infrastructure with zero-day vulnerabilities and the deployment of malware customized to specific appliance ecosystems.”
原文始发于THN:Chinese Hacking Group Exploits Barracuda Zero-Day to Target Government, Military, and Telecom
转载请注明:Chinese Hacking Group Exploits Barracuda Zero-Day to Target Government, Military, and Telecom | CTF导航