Executive Summary 摘要
- SentinelLabs has identified suspected-Chinese malware and infrastructure potentially involved in China-associated operations directed at the gambling sector within Southeast Asia.
SentinelLabs已经确定了可疑的中国恶意软件和基础设施,这些恶意软件和基础设施可能涉及针对东南亚赌博业的中国相关行动。 - The threat actors abuse Adobe Creative Cloud, Microsoft Edge, and McAfee VirusScan executables vulnerable to DLL hijacking to deploy Cobalt Strike beacons.
威胁行为者滥用Adobe Creative Cloud,Microsoft Edge和McAfee VirusScan可执行文件容易受到DLL劫持,以部署Cobalt Strike信标。 - We’ve observed related malware using the signature of a likely stolen code signing certificate issued to PMG PTE LTD, a Singapore-based vendor of Ivacy VPN services.
我们观察到相关的恶意软件使用可能被盗的代码签名证书的签名,该证书颁发给新加坡Ivacy VPN服务提供商PMG PTE LTD。 - Indicators point to the China-aligned BRONZE STARLIGHT group; however, the exact grouping remains unclear due to the interconnected relationships among various Chinese APT groups.
指标指向与中国结盟的青铜星光集团;然而,由于中国各个APT团体之间的相互联系,确切的分组尚不清楚。
Overview 概述
Thriving after China’s crackdown on its Macao-based gambling industry, the Southeast Asian gambling sector has become a focal point for the country’s interests in the region, particularly data collection for monitoring and countering related activities in China.
在中国打击以澳门为基地的赌博业后,东南亚博彩业蓬勃发展,已成为该国在该地区利益的焦点,特别是为监测和打击中国相关活动而收集的数据。
We observed malware and infrastructure likely related to China-aligned activities targeting this sector. The malware and infrastructure we analyze are related to indicators observed in Operation ChattyGoblin and are likely part of the same activity cluster. Operation ChattyGoblin is ESET’s name for a series of attacks by China-nexus actors targeting Southeast Asian gambling companies with trojanized Comm100 and LiveHelp100 chat applications.
我们观察到恶意软件和基础设施可能与中国针对该行业的活动有关。我们分析的恶意软件和基础设施与在ChattyGoblin行动中观察到的指标有关,并且可能是同一活动集群的一部分。Operation ChattyGoblin是ESET的一系列攻击的名称,这些攻击由中国有联系的行为者针对东南亚赌博公司,使用木马化的Comm100和LiveHelp100聊天应用程序。
The targeting, used malware, and C2 infrastructure specifics point to past activities that third parties have linked to the China-aligned BRONZE STARLIGHT group (also known as DEV-0401 or SLIME34). This is a suspected Chinese ‘ransomware’ group whose main goal appears to be espionage rather than financial gain, using ransomware as means for distraction or misattribution. Team T5 has also reported on BRONZE STARLIGHT’s politically-motivated involvement in targeting the Southeast Asian gambling industry.
目标、使用的恶意软件和 C2 基础设施细节指向第三方与中国结盟的 BRONZE STARLIGHT 集团(也称为 DEV-0401 或 SLIME34)相关的过去活动。这是一个可疑的中国“勒索软件”组织,其主要目标似乎是间谍活动而不是经济利益,使用勒索软件作为分散注意力或错误归因的手段。T5团队还报道了BRONZE STARLIGHT出于政治动机参与针对东南亚赌博业。
Despite the indicators observed, accurate clustering remains challenging. The Chinese APT ecosystem is plagued by extensive sharing of malware and infrastructure management processes between groups, making high confidence clustering difficult based on current visibility. Our analysis has led us to historical artifacts that represent points of convergence between BRONZE STARLIGHT and other China-based actors, which showcases the complexity of a Chinese threat ecosystem composed of closely affiliated groups.
尽管观察到了这些指标,但准确的聚类仍然具有挑战性。中国的APT生态系统受到群组之间广泛共享恶意软件和基础设施管理流程的困扰,这使得基于当前可见性的高置信度集群变得困难。我们的分析将我们引向了代表BRONZE STARLIGHT与其他中国参与者之间交汇点的历史文物,这些文物展示了由紧密联系的团体组成的中国威胁生态系统的复杂性。
Background 背景
ESET reported that a ChattyGoblin-related attack in March 2023 targeted the support agents of a gambling company in the Philippines. In the attack, a trojanized LiveHelp100 application downloaded a .NET malware loader named agentupdate_plugins.exe. The final payload was a Cobalt Strike beacon using the duckducklive[.]top domain for C2 purposes. The hash of this malware loader was not disclosed.
ESET 报告称,2023 年 3 月与 ChattyGoblin 相关的攻击针对的是菲律宾一家赌博公司的支持代理。在攻击中,一个木马化的 LiveHelp100 应用程序下载了一个名为 agentupdate_plugins.exe .最终的有效载荷是一个钴打击信标,用于 duckducklive[.]top C2目的。此恶意软件加载程序的哈希值未披露。
We subsequently identified malware loaders that we assess are closely related to those observed as part of Operation ChattyGoblin and are likely part of the same activity cluster – a .NET executable also named agentupdate_plugins.exe and its variant AdventureQuest.exe.
我们随后确定了恶意软件加载程序,我们评估这些加载程序与作为 ChattyGoblin 行动的一部分观察到的恶意软件加载程序密切相关,并且可能是同一活动群集的一部分——一个 .NET 可执行文件也被命名 agentupdate_plugins.exe 及其变体 AdventureQuest.exe 。
This association is based on naming conventions, code, and functional overlaps with the sample described in ESET’s report. Although we cannot conclusively determine whether the agentupdate_plugins.exe we analyzed is the same as that reported by ESET, we note that one of its VirusTotal submissions is dated March 2023 and originates from the Philippines. This aligns with the geolocation of the target and the timeline of the ChattyGoblin-related attack involving agentupdate_plugins.exe.
此关联基于命名约定、代码和功能与 ESET 报告中描述的示例重叠。尽管我们无法最终确定我们分析的内容 agentupdate_plugins.exe 是否与 ESET 报告的相同,但我们注意到其提交的 VirusTotal 之一日期为 2023 年 3 月,来自菲律宾。这与目标的地理位置和涉及的ChattyGoblin相关攻击的时间线一致 agentupdate_plugins.exe 。
The Malware Loaders 恶意软件加载程序
agentupdate_plugins.exe and AdventureQuest.exe deploy .NET executables based on the SharpUnhooker tool, which download second-stage data from Alibaba buckets hosted at agenfile.oss-ap-southeast-1.aliyuncs[.]com and codewavehub.oss-ap-southeast-1.aliyuncs[.]com. The second-stage data is stored in password-protected zip archives.
agentupdate_plugins.exe 并 AdventureQuest.exe 部署基于 SharpUnhooker 工具的 .NET 可执行文件,该工具从托管在 和 codewavehub.oss-ap-southeast-1.aliyuncs[.]com 的 agenfile.oss-ap-southeast-1.aliyuncs[.]com 阿里巴巴存储桶下载第二阶段数据。第二阶段数据存储在受密码保护的zip存档中。
The zip archives downloaded by agentupdate_plugins.exe and AdventureQuest.exe contain sideloading capabilities. Each of the archives we were able to retrieve consists of a legitimate executable vulnerable to DLL search order hijacking, a malicious DLL that gets sideloaded by the executable when started, and an encrypted data file named agent.data.
由 下载并 agentupdate_plugins.exe AdventureQuest.exe 包含旁加载功能的 zip 存档。我们能够检索的每个存档都包含一个易受 DLL 搜索顺序劫持的合法可执行文件、一个在启动时被可执行文件旁加载的恶意 DLL,以及一个名为 agent.data 的加密数据文件。
The executables are components of the software products Adobe Creative Cloud, Microsoft Edge, and McAfee VirusScan. The malicious DLLs masquerade as their legitimate counterparts: They export functions with the same names, such that specific functions, when invoked by the legitimate executables, decrypt and execute code embedded in the data files. The data files we could retrieve implement Cobalt Strike beacons.
可执行文件是软件产品Adobe Creative Cloud,Microsoft Edge和McAfee VirusScan的组件。恶意 DLL 伪装成其合法对应项:它们导出具有相同名称的函数,以便特定函数在由合法可执行文件调用时解密并执行嵌入在数据文件中的代码。我们可以检索的数据文件实现了钴打击信标.
| Zip archive 压缩存档 | Archive content 存档内容 | Final payload 最终有效载荷 |
| adobe_helper.zip (agentupdate_plugins.exe) adobe_helper.zip (agentupdate_plugins.exe) |
Adobe CEF Helper.exe libcef.dll agent.data (not available) Adobe CEF Helper.exe libcef.dll agent.data (不可用) |
/ |
| cefhelper.zip (AdventureQuest.exe) cefhelper.zip (AdventureQuest.exe) |
identity_helper.exe msedge_elf.dll agent.data identity_helper.exe msedge_elf.dll代理数据 |
Cobalt Strike C2: www.100helpchat[.]com 钴打击C2:www.100helpchat[.].com |
| Agent_bak.zip (AdventureQuest.exe) Agent_bak.zip(冒险任务.exe) |
mfeann.exe LockDown.dll agent.data mfeann.exe LockDown.dll agent.data |
Cobalt Strike C2: live100heip[.]com 钴打击C2:live100heip[.]。.com |
The 100helpchat[.]com and live100heip[.]com C2 domains follow the naming convention of the LiveHelp100 trojanized application used in operation ChattyGoblin, possibly to make malicious network activity look like legitimate LiveHelp100 activity.
100helpchat[.]com 和 live100heip[.]com C2 域遵循 ChattyGoblin 操作中使用的 LiveHelp100 木马化应用程序的命名约定,可能使恶意网络活动看起来像合法的 LiveHelp100 活动。
agentupdate_plugins.exe and AdventureQuest.exe implement geofencing based on the ifconfig.co IP-based geolocation service. The loaders are meant to stop their execution if they are run on a machine located in the United States, Germany, France, Russia, India, Canada, or the United Kingdom. This may indicate that the threat actors have no interest in intrusions in these countries for this campaign. Due to errors in implementation, the geofencing fails to work as intended.
agentupdate_plugins.exe 并 AdventureQuest.exe 基于 ifconfig.co IP的地理定位服务实施地理围栏。如果加载程序在美国、德国、法国、俄罗斯、印度、加拿大或英国的计算机上运行,则加载程序将停止执行。这可能表明威胁行为者对入侵这些国家/地区进行此活动没有兴趣。由于实施中的错误,地理围栏无法按预期工作。
Stolen Ivacy VPN Certificate
被盗的 Ivacy VPN 证书
AdventureQuest.exe is signed using a certificate issued to the Ivacy VPN vendor PMG PTE LTD:
AdventureQuest.exe 使用颁发给Ivacy VPN供应商PMG PTE LTD的证书进行签名:
- Thumbprint: 62E990CC0A26D58E1A150617357010EE53186707
指纹: 62E990CC0A26D58E1A150617357010EE53186707 - Serial number: 0E3E037C57A5447295669A3DB1A28B8A.
序列号:0E3E037C57A5447295669A3DB1A28B8A。
Ivacy has been present on the market since 2007 and attracts users with low-price offerings.
Ivacy自2007年以来一直出现在市场上,并以低价产品吸引用户。
It is likely that at some point the PMG PTE LTD singing key has been stolen – a familiar technique of known Chinese threat actors to enable malware signing. VPN providers are critical targets, since they enable threat actors to potentially gain access to sensitive user data and communications.
很可能在某个时候,PMG PTE Ltd的歌唱密钥被盗了 – 这是已知的中国威胁行为者启用恶意软件签名的熟悉技术。VPN提供商是关键目标,因为它们使威胁参与者能够潜在地访问敏感的用户数据和通信。
At the time of writing, we have not observed any public statements by PMG PTE LTD clarifying the circumstances that have led to the use of their signing keys for signing malware. The DigiCert Certificate Authority has revoked the compromised certificate after a public discussion on the issue.
在撰写本文时,我们尚未观察到PMG PTE Ltd的任何公开声明,澄清导致使用其签名密钥对恶意软件进行签名的情况。DigiCert证书颁发机构在就此问题进行公开讨论后已吊销已泄露的证书。
HUI Loader 回族装载机
The malicious DLLs libcef.dll, msedge_elf.dll, and LockDown.dll distributed by agentupdate_plugins.exe and AdventureQuest.exe are HUI Loader variants. HUI Loader is a custom malware loader shared between several China-nexus groups. The loader is executed through sideloading by legitimate executables vulnerable to DLL hijacking and stages a payload stored in an encrypted file. HUI Loader variants may differ in implemented payload staging and execution techniques as well as additional functionalities, such as establishing persistence and disabling security features.
恶意 libcef.dll DLL 、 msedge_elf.dll 和 LockDown.dll 由 和 AdventureQuest.exe 分发, agentupdate_plugins.exe 是 HUI 加载程序的变体。HUI 加载程序是一个自定义恶意软件加载程序,由多个中国关联组织共享。加载程序通过易受 DLL 劫持的合法可执行文件旁加载来执行,并暂存存储在加密文件中的有效负载。HUI 加载程序变体在实现的有效负载暂存和执行技术以及其他功能(例如建立持久性和禁用安全功能)方面可能有所不同。
libcef.dll, msedge_elf.dll, and LockDown.dll closely resemble HUI Loader variants observed in a string of cyberespionage and ransomware operations that third parties have linked to APT10, TA410, and BRONZE STARLIGHT.
libcef.dll 、,并且 LockDown.dll 与第三方链接到 APT10、 msedge_elf.dll TA410 和青铜星光的一系列网络间谍和勒索软件操作中观察到的 HUI 加载程序变体非常相似。
| Threat actor 威胁参与者 | Description 描述 |
| BRONZE STARLIGHT 青铜星光 Aliases: DEV-0401, SLIME34 别名:DEV-0401、史莱姆34 |
A China-based ransomware operator active since 2021. The group is known for deploying a variety of ransomware families, such as LockFile, AtomSilo, NightSky, LockBit 2.0, and Pandora, and shares tooling with APT10. BRONZE STARLIGHT’s main goal is suspected to be espionage rather than financial gain, using ransomware as means for distraction or misattribution. 自 2021 年以来活跃的中国勒索软件运营商。该组织以部署各种勒索软件系列而闻名,例如LockFile,AtomSilo,NightSky,LockBit 2.0和Pandora,并与APT10共享工具。BRONZE STARLIGHT的主要目标被怀疑是间谍活动而不是经济利益,使用勒索软件作为分散注意力或错误归因的手段。 |
| APT10 APT10 Aliases: BRONZE RIVERSIDE, MenuPass 别名:青铜河畔,菜单通行证 |
A China-nexus cyberespionage group active since at least 2009. The group focuses on targeting entities considered strategically important by the Chinese state. 一个与中国有联系的网络间谍组织,至少自2009年以来一直活跃。该组织专注于针对中国政府认为具有重要战略意义的实体。 |
| TA410 TA410 | A China-nexus cyberespionage group loosely linked to APT10, tracked as a distinct entity. The group is mostly known for targeting the US utilities sector and Middle Eastern governments. 一个与中国有联系的网络间谍组织,与APT10松散地联系在一起,作为一个独特的实体进行跟踪。该组织主要以针对美国公用事业部门和中东政府而闻名。 |
APT10 and TA410 Operations
APT10 和 TA410 操作
The cef_string_map_key function of libcef.dll downloaded by agentupdate_plugins.exe references the C:\Users\hellokety.ini file.
libcef.dll 下载方式 agentupdate_plugins.exe cef_string_map_key 引用 C:\Users\hellokety.ini 文件的功能。
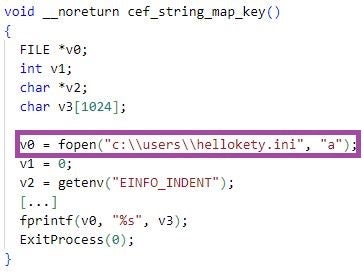
cef_string_map_key功能
HUI Loader variants with this exact artifact have been reported as part of several cyberespionage operations:
据报道,具有此精确工件的 HUI 装载机变体是几次网络间谍行动的一部分:
- enSilo (now Fortinet) has disclosed cyberespionage activities in Southeast Asia observed in April 2019 and attributed them with medium confidence to APT10.
enSilo(现为 Fortinet)披露了 2019 年 4 月在东南亚观察到的网络间谍活动,并将其中等信心归因于 APT10。
- Researchers from Macnica, Secureworks, and Kaspersky have presented on A41APT campaign activity conducted throughout 2021. A41APT is a long-running cyberespionage campaign targeting Japanese companies and their overseas branches. Kaspersky has attributed earlier A41APT activity (from March 2019 to the end of December 2020) with high confidence to APT10. TrendMicro has attributed A41APT activity over 2020 and 2021 to a group they track as Earth Tengshe, noting that Earth Tengshe is related to APT10 with some differences in employed TTPs.
来自Macnica,Secureworks和卡巴斯基的研究人员介绍了2021年全年进行的A41APT活动。A41APT是一项针对日本公司及其海外分支机构的长期网络间谍活动。卡巴斯基将早期的A41APT活动(从2019年3月至2020年12月底)归因于APT10,信心很高。趋势科技将 2020 年和 2021 年的 A41APT 活动归因于他们追踪的地球腾舍组,并指出地球腾舍与 APT10 有关,但在使用的 TTP 上存在一些差异。
- ESET has presented on TA410 activities, noting the
hellokety.iniartifact in this context. ESET also notes the possibility of misattribution the April 2019 activities reported by Fortinet to APT10 instead of TA410.
ESET介绍了TA410活动,并指出了此背景下的hellokety.ini工件。ESET还指出,Fortinet向APT10而不是TA410报告了2019年4月的活动。
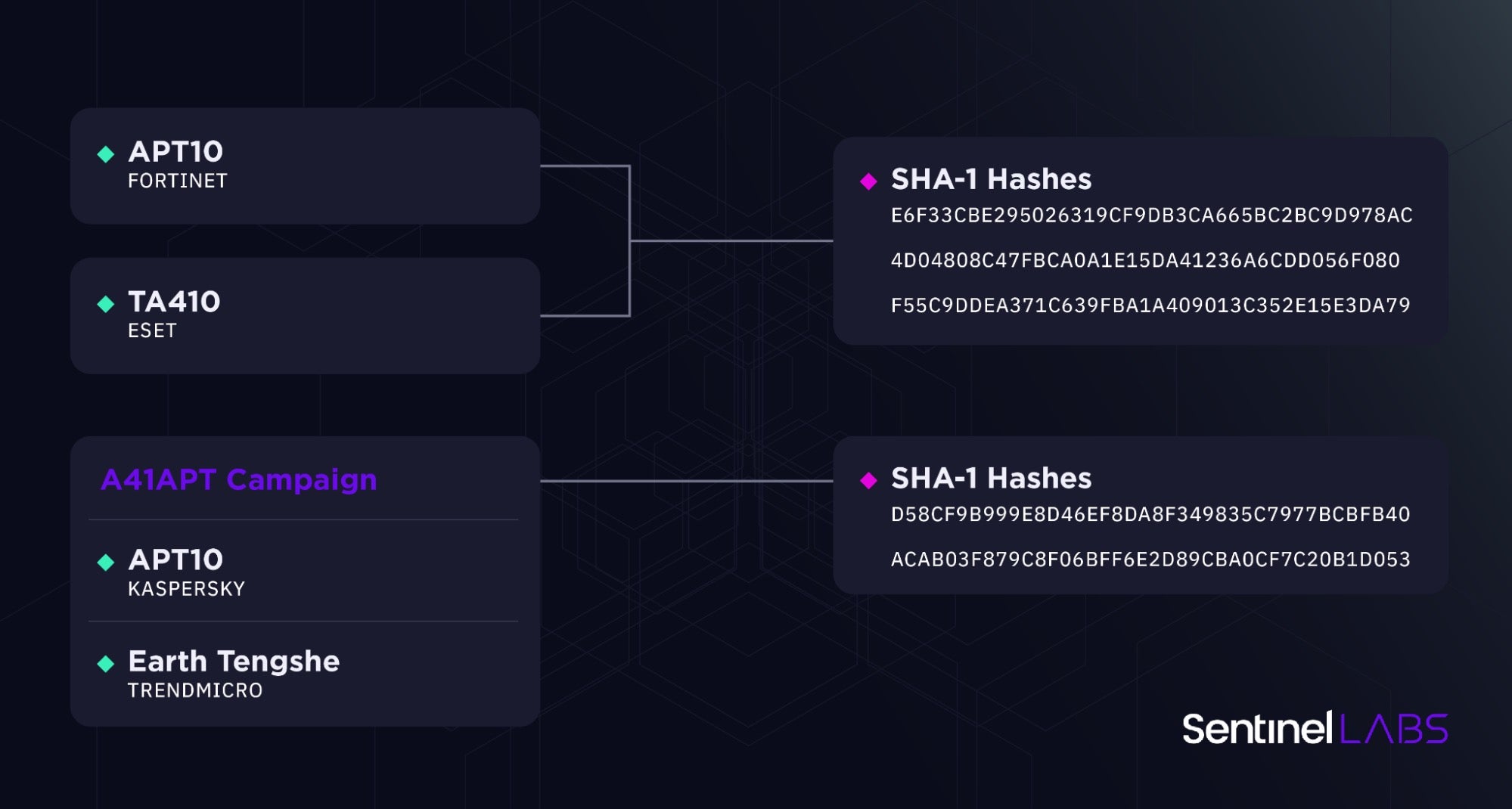
用于 APT10 和 TA410 操作的 HUI 装载机变体 (hellokety.ini)
BRONZE STARLIGHT Operations
青铜星光行动
Since around 2021, HUI Loader variants have been deployed in operations involving the ransomware families LockFile (Symantec, 2021; NSFOCUS, 2021), AtomSilo (Sophos, 2021), NightSky (Microsoft, 2021), LockBit 2.0 (SentinelLabs, 2022), and Pandora (TrendMicro, 2022). Some of these operations have been attributed to BRONZE STARLIGHT by the organizations disclosing them and all of them collectively by Secureworks. All of these ransomware families have been noted by Microsoft as being part of the BRONZE STARLIGHT arsenal in time intervals aligning with those of the previously mentioned operations.
自 2021 年左右以来,HUI 加载程序变体已部署在涉及勒索软件家族 LockFile 的操作中(赛门铁克,2021 年;绿盟科技,2021 年)、原子筒仓(Sophos,2021 年)、夜空(Microsoft年,2021 年)、LockBit 2.0(哨兵实验室,2022 年)和潘多拉(趋势科技,2022 年)。其中一些操作被披露它们的组织归因于BRONZE STARLIGHT,所有这些操作都由Secureworks共同承担。Microsoft 指出所有这些勒索软件系列都是 BRONZE STARLIGHT 武器库的一部分,时间间隔与前面提到的操作一致。
C2 Infrastructure C2 基础设施
The Cobalt Strike C2 GET and POST URIs associated with the Operation ChattyGoblin domain duckducklive[.]top contain /functionalStatus and /rest/2/meetings, respectively. Their uncommon full forms closely resemble those observed by Secureworks in AtomSilo, Night Sky, and Pandora operations they attribute to BRONZE STARLIGHT. The researchers reported that, as of June 2022, they had not seen this Cobalt Strike configuration associated with other ransomware families. The threat actors have likely adapted a public Cobalt Strike malleable C2 profile available in a Github repository of the user xx0hcd.
与Operation ChattyGoblin域 duckducklive[.]top 关联的Cobalt Strike C2 GET和POST URI分别包含 /functionalStatus 和 /rest/2/meetings 。它们不寻常的完整形式与Secureworks在AtomSilo,Night Sky和Pandora操作中观察到的非常相似,他们将其归因于BRONZE STARLIGHT。研究人员报告说,截至 2022 年 6 月,他们还没有看到这种与其他勒索软件系列相关的钴打击配置。威胁行为者可能已经改编了用户 xx0hcd Github 存储库中可用的公共 Cobalt Strike 可延展 C2 配置文件。
| Cobalt Strike C2 POST URI 钴打击 C2 后 URI |
Relation 关系 |
| /rest/2/meetingsmCRW64qPFqLKw7X56lR41fx /rest/2/meetingsmCRW64qPFqLKw7X56lR41fx |
Operation ChattyGoblin 查蒂哥布林行动 |
| /rest/2/meetingsVDcrCtBuGm8dime2C5zQ3EHbRE156AkpMu6W /rest/2/meetingsVDcrCtBuGm8dime2C5zQ3EHbRE156AkpMu6W |
AtomSilo 原子筒仓 |
| /rest/2/meetingsQpmhJveuV1ljApIzpTAL /rest/2/meetingsQpmhJveuV1ljApIzpTAL |
Night Sky 夜空 |
| /rest/2/meetingsKdEs85OkdgIPwcqbjS7uzVZKBIZNHeO4r5sKe /rest/2/meetingsKdEs85OkdgIPwcqbjS7uzVZKBIZNHeO4r5sKe |
Pandora 潘多拉 |
The C2 GET and POST URIs associated with the www.100helpchat[.]com and live100heip[.]com domains we observed contain /owa followed by character strings. The format of these strings resembles those in the URIs associated with duckducklive[.]top and also those reported in past BRONZE STARLIGHT activities. It is likely that the threat actors have adapted another open source Cobalt Strike malleable C2 profile, which is also available in a Github repository of the user xx0hcd.
与我们观察到的 www.100helpchat[.]com 和 live100heip[.]com 域关联的 C2 GET 和 POST URI 包含 /owa 后跟字符串。这些字符串的格式类似于与 URI 关联的 duckducklive[.]top 字符串,也类似于过去青铜星光活动中报告的格式。威胁参与者很可能已经改编了另一个开源的Cobalt Strike可延展的C2配置文件,该配置文件也可以在用户的 xx0hcd Github存储库中找到。
| Domain 域 | Cobalt Strike C2 URIs 钴走向 C2 URI |
| live100heip[.]com live100heip[.]。.com | GET: /owa/Z7bziD-BDtV9U1aLS9AhW4jyN1NEOelTEi GET: /owa/Z7bziD-BDtV9U1aLS9AhW4jyN1NEOelTEi POST: /owa/LAC9kgQyM1HD3NSIwi–mx9sHB3vcmjJJm POST: /owa/LAC9kgQyM1HD3NSIwi–mx9sHB3vcmjJJm |
| www.100helpchat[.]com www.100helpchat[.]。.com | GET: /owa/aLgnP5aHtit33SA2p2MenNuBmYy GET: /owa/aLgnP5aHtit33SA2p2MenNuBmYy POST: /owa/XF0O-PjSCEslnDo51T0K4TOY POST: /owa/XF0O-PjSCEslnDo51T0K4TOY |
The Cobalt Strike profiles associated with the duckducklive[.]top, www.100helpchat[.]com, and live100heip[.]com domains share a C2 port number (8443) and a watermark (391144938). The earliest record of duckducklive[.]top becoming active is dated 24 Feb 2023. The earliest records of live100heip[.]com and 100helpchat[.]com becoming active are dated 24 Feb 2023 (overlapping with that of duckducklive[.]top) and 28 Feb 2023, respectively.
与 duckducklive[.]top 、 www.100helpchat[.]com 和 live100heip[.]com 域关联的钴攻击配置文件共享 C2 端口号 ( 8443 ) 和水印 ( 391144938 )。最早活跃的 duckducklive[.]top 记录是 2023 年 2 月 24 日。最早 live100heip[.]com 的记录和 100helpchat[.]com 活跃日期分别为 2023 年 2 月 24 日(与 duckducklive[.]top 重叠)和 2023 年 2 月 28 日。
The three domains are each hidden behind CloudFlare, who were quick in remediation after we reported the service abuse. In this case, however, the actors revealed their true-hosting locations due to an OPSEC mistake in their initial deployment of the domain’s SSL certificates on their Alibaba Cloud hosting servers at 8.218.31[.]103, 47.242.72[.]118, and 47.242.159[.]242.
这三个域都隐藏在CloudFlare后面,在我们报告服务滥用后,CloudFlare迅速进行了修复。但是,在这种情况下,由于在阿里云托管服务器上最初部署域的SSL证书时出现OPSEC错误,参与者透露了其真实托管位置,该位置位于 8.218.31[.]103 , 47.242.72[.]118 和 47.242.159[.]242 。
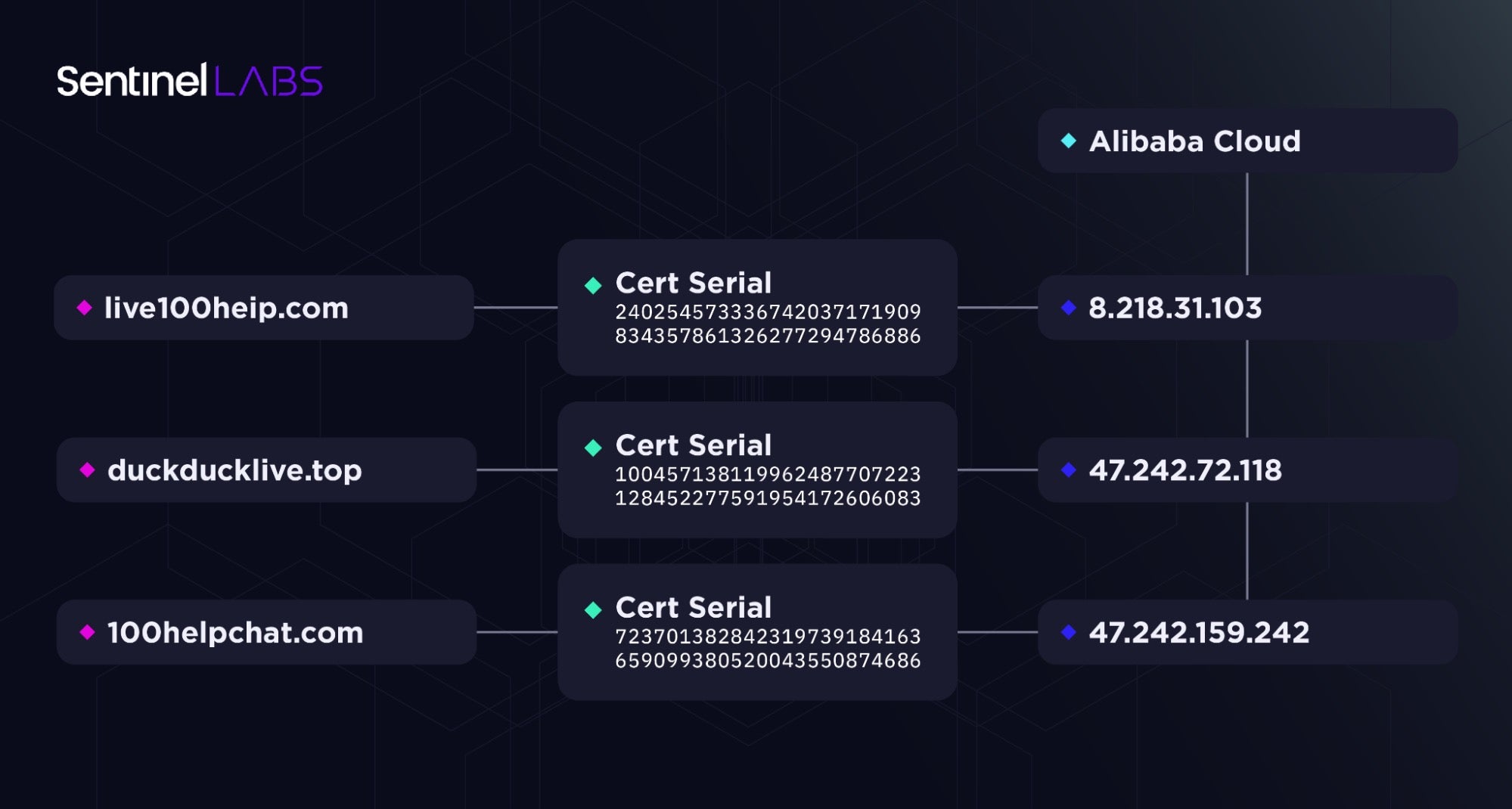
在阿里巴巴 IP 上使用的证书
While the analysis of the Cobalt Strike profiles provides links to previous BRONZE STARLIGHT activities, an assessment of the specific group attribution based on current intelligence should be treated with caution. It is noteworthy that Chinese cyber espionage threat actors are progressively refining their operational tactics in manners that obfuscate clear attribution through publicly available intelligence sources alone.
虽然对钴罢工概况的分析提供了与以前的青铜星光活动的链接,但根据当前情报对特定群体归属的评估应谨慎对待。值得注意的是,中国网络间谍威胁行为者正在逐步完善其行动策略,其方式仅通过公开的情报来源混淆了明确的归属。
To illustrate this concept, consider the scenario where a broader array of domains imitating various brands may be interconnected, such as those publicly documented involving the BRONZE STARLIGHT, TA410, and APT10 threat actors. Examples include microsofts[.]net, microupdate[.]xyz, microsofts[.]info, microsofts[.]org, miscrosofts[.]com, microsofts[.]com, kaspresksy[.]com, tencentchat[.]net, and microsoftlab[.]top.
为了说明此概念,请考虑以下场景:模仿各种品牌的更广泛域可能相互关联,例如涉及 BRONZE STARLIGHT、TA410 和 APT10 威胁参与者的公开记录。示例包括 microsofts[.]net 、、、、、 miscrosofts[.]com 、 microsofts[.]com kaspresksy[.]com microupdate[.]xyz microsofts[.]info microsofts[.]org t encentchat[.]net 和 microsoftlab[.]top 。
Conclusion 结论
China-nexus threat actors have consistently shared malware, infrastructure, and operational tactics in the past, and continue to do so. The activities this post discusses illustrate the intricate nature of the Chinese threat landscape.
中国-纽带威胁行为者过去一直在共享恶意软件、基础设施和运营策略,并将继续这样做。这篇文章讨论的活动说明了中国威胁形势的复杂性。
Better understanding of this landscape is essential for keeping up with its dynamics and improving defense strategies. Achieving this necessitates consistent collaborative and information sharing efforts. SentinelLabs remains dedicated to this mission and continues to closely monitor related threats.
更好地了解这一景观对于跟上其动态和改进防御战略至关重要。实现这一目标需要始终如一的协作和信息共享努力。SentinelLabs仍然致力于这一使命,并继续密切监视相关威胁。
Indicators of Compromise
妥协指标
Files (SHA1) 行 (SHA1)
| Indicator 指示器 | Description 描述 |
| 09f82b963129bbcc6d784308f0d39d8c6b09b293 09f82b963129bbcc6d784308f0d39d8c6b09b293 |
agentupdate_plugins.exe |
| 1a11aa4bd3f2317993cfe6d652fbe5ab652db151 1a11aa4bd3f2317993cfe6d652fbe5ab652db151 |
LockDown.dll |
| 32b545353f4e968dc140c14bc436ce2a91aacd82 32b545353f4e968dc140c14bc436ce2a91aacd82 |
mfeann.exe |
| 4b79016d11910e2a59b18275c786682e423be4b4 4b79016d11910e2a59b18275c786682e423be4b4 |
Adobe CEF Helper.exe Adobe CEF Helper.exe |
| 559b4409ff3611adaae1bf03cbadaa747432521b 559b4409ff3611adaae1bf03cbadaa747432521b |
identity_helper.exe |
| 57bbc5fcfd97d25edb9cce7e3dc9180ee0df7111 57bbc5fcfd97d25edb9cce7e3dc9180ee0df7111 |
agentdata.dat |
| 6e9592920cdce90a7c03155ef8b113911c20bb3a 6e9592920cdce90a7c03155ef8b113911c20bb3a |
AdventureQuest.exe |
| 76bf5ab6676a1e01727a069cc00f228f0558f842 76bf5ab6676a1e01727a069cc00f228f0558f842 |
agentdata.dat |
| 88c353e12bd23437681c79f31310177fd476a846 88c353e12bd23437681c79f31310177fd476a846 |
libcef.dll |
| 957e313abaf540398af47af367a267202a900007 957e313abaf540398af47af367a267202a900007 |
msedge_elf.dll |
Second-Stage Data URLs 第二阶段数据网址
| https[://]agenfile.oss-ap-southeast-1[.]aliyuncs.com/agent_source/temp1/cefhelper.zip https[://]agenfile.oss-ap-southeast-1[.]aliyuncs.com/agent_source/temp1/cefhelper.zip |
AdventureQuest.exe |
| https[://]agenfile.oss-ap-southeast-1.aliyuncs.com/agent_source/temp2/agent_bak.zip https[://]agenfile.oss-ap-southeast-1.aliyuncs.com/agent_source/temp2/agent_bak.zip |
AdventureQuest.exe |
| https[://]agenfile.oss-ap-southeast-1.aliyuncs.com/agent_source/temp3/adobe_helper.zip https[://]agenfile.oss-ap-southeast-1.aliyuncs.com/agent_source/temp3/adobe_helper.zip |
agentupdate_plugins.exe |
| https[://]codewavehub.oss-ap-southeast-1.aliyuncs[.]com/org/com/file/CodeVerse.zip https[://]codewavehub.oss-ap-southeast-1.aliyuncs[.]com/org/com/file/CodeVerse.zip |
AdventureQuest.exe |
C2 Domains C2 域
| www.100helpchat[.]com www.100helpchat[.]。.com | Cobalt Strike 钴罢工 |
| live100heip[.]com live100heip[.]。.com | Cobalt Strike 钴罢工 |
C2 IP Addresses C2 IP 地址
| 8.218.31[.]103 8.218.31[.]103 | Cobalt Strike 钴罢工 |
| 47.242.72[.]118 47.242.72[.]118 | Cobalt Strike 钴罢工 |
