原文始发于HDW Sec:NETGEAR NIGHTHAWK R7000P UPNPD BUFFER OVERFLOW REMOTE CODE EXECUTION VULNERABILITY
NETGEAR NIGHTHAWK R7000P UPNPD BUFFER OVERFLOW REMOTE CODE EXECUTION VULNERABILITY
- Product links: https://www.netgear.com/support/product/r7000p.aspx
- Version: < 1.3.3.154
- Author: Jean-Jamil Khalife
VULNERABLE MODELS
Nighthawk Wi-Fi Mesh Systems
- MR60 – fixed in firmware version 1.1.7.132
- MS60 – fixed in firmware version 1.1.7.132
Routers
- R6900P – fixed in firmware version 1.3.3.154
- R7000P – fixed in firmware version 1.3.3.154
- R7960P – fixed in firmware version 1.4.4.94
- R8000P – fixed in firmware version 1.4.4.94
DISCLOSURE TIMELINE
- 2022-07-22: Netgear contacted
- 2022-11-01: Fix integrated
INTRODUCTION
As explained in our previous article [ https://hdwsec.fr/blog/20221109-netgear/ ] detailing a vulnerability in the Netgear R7000P router, here are the details of a second flaw we found.
A global memory corruption vulnerability exists in the upnpd server. A specially-crafted SUBSCRIBE request can lead to a stack buffer overflow. An attacker can send a malicious request to trigger this vulnerability and modify the execution flow to an arbitrary address somewhere in the memory of the upnpd process. This vulnerability can be exploited from the WAN or LAN.
The Nighthawk R7000P is a popular dual-band Wi-Fi router advertised with gaming-focused features, smart parental controls, and internal hardware that is sufficiently powerful to accommodate the needs of home power users.
The vulnerability resides in the /usr/sbin/upnpd binary, running on the Netgear router.
As a reminder, due to increasing demand, we do vulnerability research on connected objects (routers, cameras, printers, etc.). One of the missions entrusted to us by our client was to find vulnerabilities on a selection of embedded devices, including the aforementioned Netgear Nightawk router. Several vulnerabilities have been discovered and will be published on this blog.
VULNERABILITY
This vulnerability can be remotely exploited by an attacker on the LAN and WAN side of the router, without authentication.
This attack takes place in 3 steps:
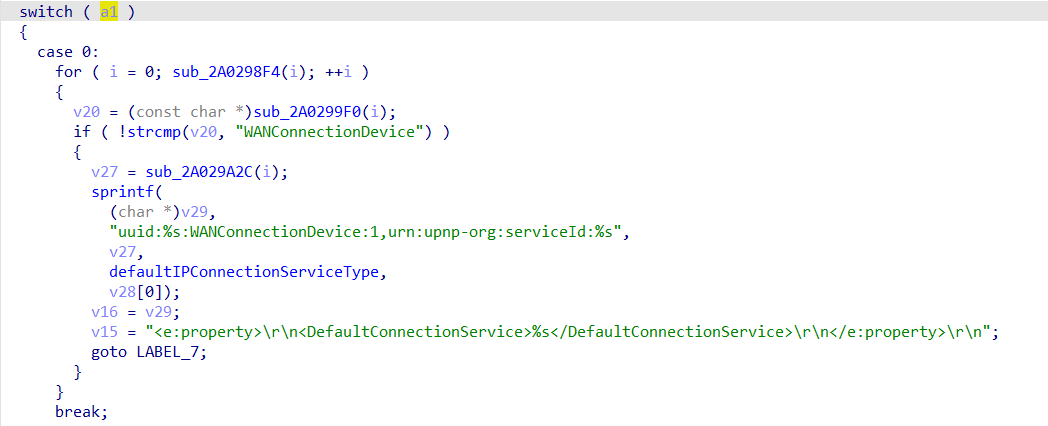
- A stack buffer overflow exists in the function sub_2A021AE0() because sprintf() does not check the size of the global variable defaultIPConnectionServiceType.
- defaultIPConnectionServiceType can be rewritten with a larger size by overflowing the previous global variable.
- This previous global variable is an array of structures and can be overflowed.
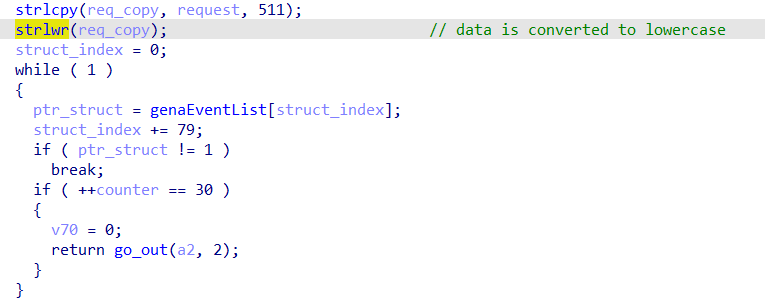
The upnpd server processes several types of requests, in particular SUBSCRIBE and UNSUBSCRIBE.
When it receives a SUBSCRIBE type request, it writes the data received in a structure in memory. Each of them is 79 bytes long and is part of a single array in global memory.
The number of structures is limited to 30. When the global table is full, it is no longer possible to add new structures.
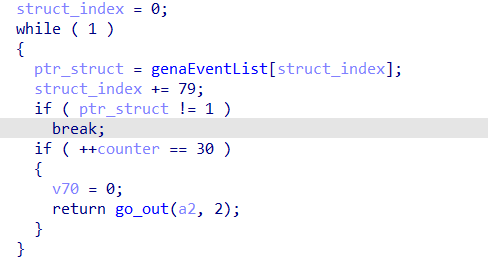
When a SUBSCRIBE request is received, the request data is parsed by upnpd and written in a new structure.
Indeed, each field is parsed (URI, IP, …, Callback) then inserted into a new structure in memory.

If the data content of the “callback” field is large enough, it is possible to exceed 79 bytes and thus overflow the following structure.
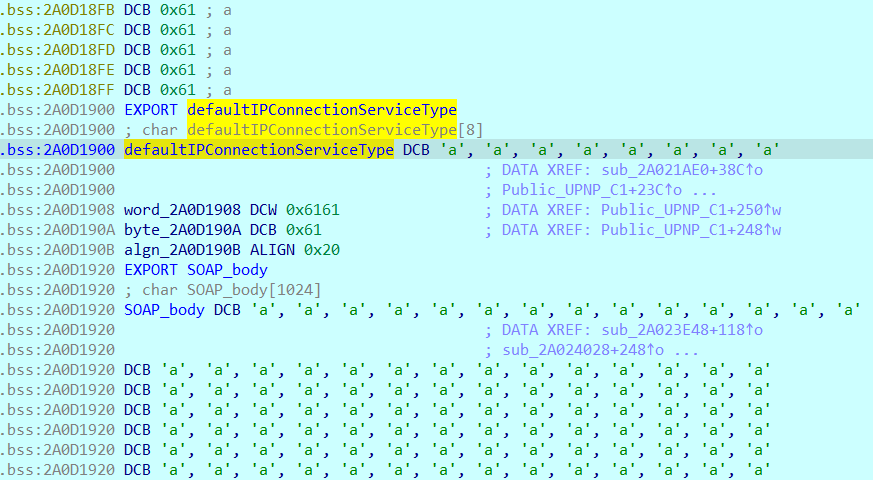
Also, if the global table is filled to the max (30) and the 30th structure overflows the data sequence in memory, it is possible to rewrite the value of the defaultIPConnectionServiceType global variable with a larger size.
When creating a new subscribe structure in memory, the function sub_2A021AE0() is called and the defaultIPConnectionServiceType variable is positioned as a parameter to sprintf(), creating a stack overflow since the size of the destination buffer is not checked.
EXPLOITATION
To summarize, we need to:
- Fill the whole structure table;
- Overflow the buffer defaultIPConnectionServiceType and trigger the stack overflow.
Bypass ASLR
The upnpd binary is not ASLR compiled and the executable addresses are in the range 0x2a000000 and 0x2a055000. All other mapped modules run with ASLR.
This will be enough to later find a gadget allowing the exploitation of this flaw.
|
1
|
2a000000-2a055000 r-xp 00000000 1f:03 1872 /usr/sbin/upnpd |
Finding gadget and getting root
When the vulnerability is triggered, the stack is overflowed and some registers can be controlled (here registers R4, R5, R6, R7, R8, … and PC), which facilitates the exploitation of this flaw, in particular by increasing the number of possible gadget rops.
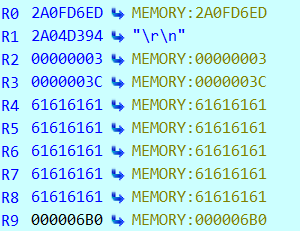
Some gadgets allow making direct usage of the system() function.
The only constraint is to determine an address where each byte is not between 0x41 and 0x5A (uppercase alphabet) because the overflowed data will be written in lowercase by upnpd before triggering the stack overflow.
There are no other filters complicating the exploitation of this flaw (removal of special characters, etc.) unlike another Netgear vulnerability found that we may detail in a future article.
This ROP gadget is what we need, allowing the execution of an arbitrary command; here: utelnetd -l /bin/sh;

Note: the exploit takes about 2mn30s because it takes time to fill in the structure table. The upnpd server takes several seconds to process each request.
RECOMMENDATIONS
Validating the data copied into the structures in memory must be systematic in order to avoid any buffer overflow.
Also, it is necessary to replace sprintf() with safer functions — such as snprintf() — to control the size of the processed data in order to avoid memory safety problems. Use appropriate compiler options (like -Wformat-overflow=2, -Wformat-security, -Wfortify-source, -Wformat=2, …) to detect these issues preemptively.
CONCLUSION
Even if the upnpd server used by Netgear has been widely audited in recent years, it continues to remain vulnerable.
This vulnerability research was requested by one of our customers who wanted to know if it was possible to compromise the company’s routers.
The vulnerability we found made it possible to obtain a shell on the router which could subsequently lead to access to third-party subnets.
Netgear is a major player in network devices for home and small/medium companies which makes their product a valuable target for hacker. Note that other Netgear products were affected by the same vulnerability.
REFERENCES
转载请注明:NETGEAR NIGHTHAWK R7000P UPNPD BUFFER OVERFLOW REMOTE CODE EXECUTION VULNERABILITY | CTF导航