Analysis of FG-IR-22-398 – FortiOS – heap-based buffer overflow in SSLVPNd
Fortinet has published CVSS: Critical advisory FG-IR-22-398 / CVE-2022-42475 on Dec 12, 2022. The following writeup details our initial investigation into this malware and additional IoCs identified during our ongoing analysis.
Executive Summary
- Multiple additional IoCs have been uncovered related to the incident FG-IR-22-398 / CVE-2022-42475
- The complexity of the exploit suggests an advanced actor and that it is highly targeted at governmental or government-related targets.
Incident Analysis
As mentioned in the advisory, we detected this issue in the wild and were able to collect a sample of the malware along with related network traffic.
The malware was a variant of a generic Linux implant customized for FortiOS. The following information was gathered during the forensic filesystem and binary analysis of the received appliance.
Libips.bak

The suspicious binary was located at /data/lib/libips.bak. This file may be masquerading as a component of Fortinet’s IPS Engine, located at /data/lib/libips.so. The file /data/lib/libips.so was present, but with a zero file size.
Here is an image of the /data/lib directory:

Libgif.so, libips.bak, and libiptcp.so are not part of any FortiOS components or processes.
Libips.bak appears to be a trojanized version of the IPS Engine, typically located at /data/lib/libips.so. A diff comparing libips.bak with a clean libips.so from the same FortiOS build was performed. Up to about the 0x1900 byte mark, the files differ. After that point, the files are identical. Below is a screenshot of libips.bak (top) and the clean libips.so (bottom). libips.bak contains data where libips.so does not.

After the first ~0x1900 bytes, the files are identical.

Libips.bak exports the functions ips_so_patch_urldb and ips_so_query_interface. These are the same exports in the clean IPS engine binary, libips.so. Both exported functions lead to the same malicious code. If libps.bak is named libips.so in the /data/lib directory, the malicious code will be executed automatically as components of FortiOS will call these exported functions. The binary does not attempt to return to the clean IPS engine code, so IPS functionality is also compromised. Below is an example export function that immediately calls the malicious code.

The primary malicious code is shown below.

The malicious code begins by looping through file descriptors from 3 to 255. If it can duplicate the file descriptors, it will close both the duplicate and original descriptors.

Next, it will read from /data/lib/libiptcp.so and write the data to /data/lib/libjepg.so. /data/lib/libjepg.so is renamed as /data/lib/libips.so. fork() and is used multiple times initially as an anti-debugging technique.

It then calls fork() once more. The child process reads from /data/lib/libgif.so and writes that data to /data/lib/libjepg.so. /data/lib/libjepg.so is then renamed as /data/lib/libips.so.
The parent process checks for read access to /var/.sslvpnconfigbk. This file is opened, then closed immediately. Finally, /data/lib/libipudp.so is executed with the argument “/data/lib/libipudp.so”.
The files referenced in this code—libiptcp.so, libgif.so, .sslvpnconfigbk, and libipudp.so—could not be recovered.
Wxd.conf
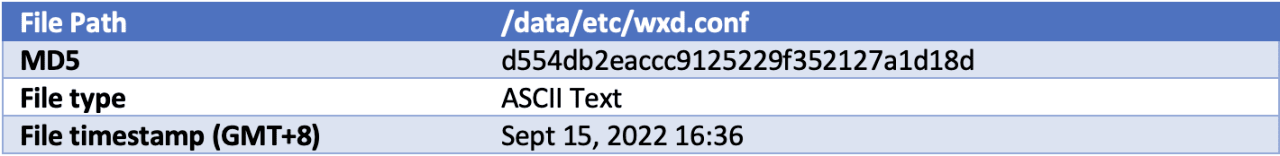
The format of this config file is similar to that of “Fast reverse proxy” found at https://github.com/fatedier/frp. This tool is described as “a fast reverse proxy to help you expose a local server behind a NAT or firewall to the Internet.”
There are records for the server IP address in logs. It sends traffic to the server’s ports 80, 443, and 444. Traffic is sent to a server with the address 188[.]34[.]130[.]40.
Packet Capture Analysis
Network packet captures obtained and analyzed by the FortiGuard Labs Threat Research Team identified suspicious traffic headed to 103[.]131[.]189[.]143. The major findings of this analysis are highlighted below.

103[.]131[.]189[.]143
Communications with the suspicious IP 103[.]131[.]189[.]143 server served two primary purposes:(1) downloading payloads and (2) receiving and executing commands. Payloads were hosted on 103[.]131[.]189[.]143 using a Python (SimpleHTTP) server listening on port: 30080.

The FortiGuard Labs Threat Research team was unable to recover the payloads because the packet captures were largely truncated or missing.
TCP Stream 1894
TCP stream 1894 contained the connection made to 103[.]131[.]189[.]143 listening on port 30443, which was an interactive shell session.

Post Incident Meta Data Investigation
Through our detailed investigation of the PCAPs, an additional IoC was uncovered.
185[.]174[.]136[.]20
The identification of this IoC led to a folder on the server containing binaries built specifically for relevant FortiGate hardware versions.
Using a Yara Rule created by the FortiGuard Threat Research Team, we were able to hunt for similar file samples. This also allowed us to identify the /var/w files that were seen executed in the PCAPs but not obtained directly from the file system.
Sample Analysis
From the analysis of the collected /var/w files samples, we found that the attacker uses advanced capabilities to manipulate FortiOS logging, as follows:
- The malware patches the logging processes of FortiOS to manipulate logs to evade detection. – /bin/miglogd & /bin/syslogd
- It includes offsets and opcodes for 27 FortiGate models and version pairs. The malware opens a handle to the processes and injects data into them.
- Versions range from 6.0.5 to 7.2.1
- Models are FG100F, FG101F, FG200D, FG200E, FG201F, FG240D, FG3H0E, FG5H0E, FG6H1E, FG800D, FGT5HD, FGT60F, FGT80F.
- The malware can manipulate log files. It searches for elog files, which are logs of events in FortiOS. After decompressing them in memory, it searches for a string the attacker specifies, deletes it, and reconstructs the logs.
- The malware can also kill the logging processes.
By emulating the malware’s execution, we found a unique string of bytes in its communication with its command & control server that can be used for an IPS signature.
- This string detects the TLS traffic by the TLS request header.
- The buffer “\x00\x0C\x08http/1.1\x02h2\x00\x00\x00\x14\x00\x12\x00\x00\x0Fwww.example.com” (unescaped) should appear inside the “Client Hello” packet.
IOCs
The following network indicators were found as part of the original and supplemental analysis (original IoCs are bolded). For details on how to search on your FortiGate device for evidence of these indicators, see the following Knowledgebase Article.
Filenames
Presence of the following artifacts in the filesystem:
/data/lib/libips.bak
/data/lib/libgif.so
/data/lib/libiptcp.so
/data/lib/libipudp.so
/data/lib/libjepg.so
/var/.sslvpnconfigbk
/data/etc/wxd.conf
/flash
IP/Domains
High Confidence
188[.]34[.]130[.]40 (port 444 observed)
103[.]131[.]189[.]143 (ports 30080,30081,30443,20443 observed)
193[.]36[.]119[.]61 (ports 8443,444 observed)
172[.]247[.]168[.]153 (port 8033 observed)
139[.]180[.]184[.]197
66[.]42[.]91[.]32
158[.]247[.]221[.]101
107[.]148[.]27[.]117
139[.]180[.]128[.]142
155[.]138[.]224[.]122
185[.]174[.]136[.]20
139[.]180[.]184[.]197
66[.]42[.]91[.]32
158[.]247[.]221[.]101
107[.]148[.]27[.]117
139[.]180[.]128[.]142
155[.]138[.]224[.]122
185[.]174[.]136[.]20
45[.]86[.]229[.]220
45[.]86[.]231[.]71
139[.]99[.]35[.]116
139[.]99[.]37[.]119
194[.]62[.]42[.]105
45[.]86[.]231[[.]71
45[.]86[.]229[[.]220
185[.]250[.]149[[.]32
137[.]175[.]30[.]138
146[.]70[.]157[[.]133
Older Actor IPs
156[.]251[.]162[.]76
156[.]251[.]163[.122
156[.]251[.]163[.]19
156[.]251[.]162[.111
File Path Samples
Files from /var/w
Hashes of post-exploitation implants—MD5
f68c3f72270800ea675889e82bb02fb8
e3f640d8785c0c864739529889b1863a
08cbaafb176ce6118f7e4e0b2d2d77cf
bdc2d2f5d5246f8956711bcce9f456b6
4548fa6625cb154ab320833186117393
e5d989b651b3eb351e10e408d5a062b3
3191cb2e06e9a30792309813793f78b6
12e28c14bb7f7b9513a02e5857592ad7
ae0839351721db5a9c269fd75dcb57ce
856341349dd954d82b112ba9165c4563
Windows sample found on VT with significant code similarity to the samples found on FortiGates
54bbea35b095ddfe9740df97b693627b
JA3 Fingerprint
The JA3 for the malware SSL/TLS client connection appears to be unique to the malware and can be used to detect an attack.
bf2b95ac267823f6588b2436bc537b26.
Summary of Our Knowledge About the Actor
The complexity of the exploit suggests an advanced actor:
- The exploit requires a deep understanding of FortiOS and the underlying hardware.
- The use of custom implants shows that the actor has advanced capabilities, including reverse-engineering various parts of FortiOS.
- The actor is highly targeted, with some hints of preferred governmental or government-related targets.
- The discovered Windows sample attributed to the attacker displayed artifacts of having been compiled on a machine in the UTC+8 timezone, which includes Australia, China, Russia, Singapore, and other Eastern Asian countries.
- The self-signed certificates created by the attackers were all created between 3 and 8 AM UTC. However, it is difficult to draw any conclusions from this given hackers do not nessesarily operate during office hours and will often operate during victim office hours to help obfuscate their activity with general network traffic.
Conclusion
Fortinet will continue to track this threat actor activity. To mitigate this issue, we recommend that all customers immediately take the actions recommended in the Critical Advisory, FG-IR-22-398. Additional guidance has been provided here for how to search for the IoCs. Should you identify that your system is showing indicators of compromise, please reach out to Fortinet for support.
Fortinet will continue to monitor this incident and will update this blog with information as it is found.
Fortinet Protection
The Fortinet Antivirus engine detects all binaries discussed in this blog using the following AV signatures:
The WebFiltering client blocks all network-based URIs.
A Fortinet Outbreak Alert Package has been created for FortiAnalyzer to detect and report on all traffic to or from IPs within the IoC range specified and will be included in Outbreak Alert Package DB 1.00083.
https://www.fortiguard.com/updates/outbreak-detection-service?version=1.00083
Details on how to search for these IoCs can be found in the following Fortinet Community Tech Tip:
Fortinet has released an IPS signature to proactively protect our customers from the exploit CVE-2022-42475 and the C&C channel respectively.
FortiOS.SSL-VPN.Heap.Buffer.Overflow
Bakso.Linux.Backdoor
原文始发于Carl Windsor, Guillaume Lovet, Hongkei Chan, and Alex Kong:Analysis of FG-IR-22-398 – FortiOS – heap-based buffer overflow in SSLVPNd
转载请注明:Analysis of FG-IR-22-398 – FortiOS – heap-based buffer overflow in SSLVPNd | CTF导航